The Journey to Zero Trust

The Zero Trust concept has been around for a while now, and the rise of remote work related to COVID lockdowns supercharged the Zero Trust conversation. Many organizations had to scramble to enable employees to work remotely but did not have technology environments that were prepared for it. As a result, technology groups often were forced to implement and now manage a mishmash of VPN, BYOD, VDI, and other solutions to keep people productive. Now there is a need to streamline and clean up these environments but also retain the advantages of easy access to resources wherever people are working. Zero Trust is an excellent way to accomplish that but getting there can be a bit intimidating. (See my colleague Keith’s blog here for more in this topic.)
The Maturity Model
Today, I would like to introduce a maturity model for Zero Trust that outlines both what the framework includes and the Microsoft solutions that address the requirements. This shows what solutions are needed for an organization to move from the Traditional column to an Advanced or Optimal configuration. Most organizations will have elements of their environment in two or even all three columns as they progress through the journey.
The most crucial element to bringing the Zero Trust approach to life is that Zero Trust really should be an intentional goal and addressed through actions defined on your overall technology roadmap. Once you get there, future application and system decisions will also need to be designed around the framework, often using the same tools and approaches outline in the maturity model.
So, let us have a look at the maturity model:
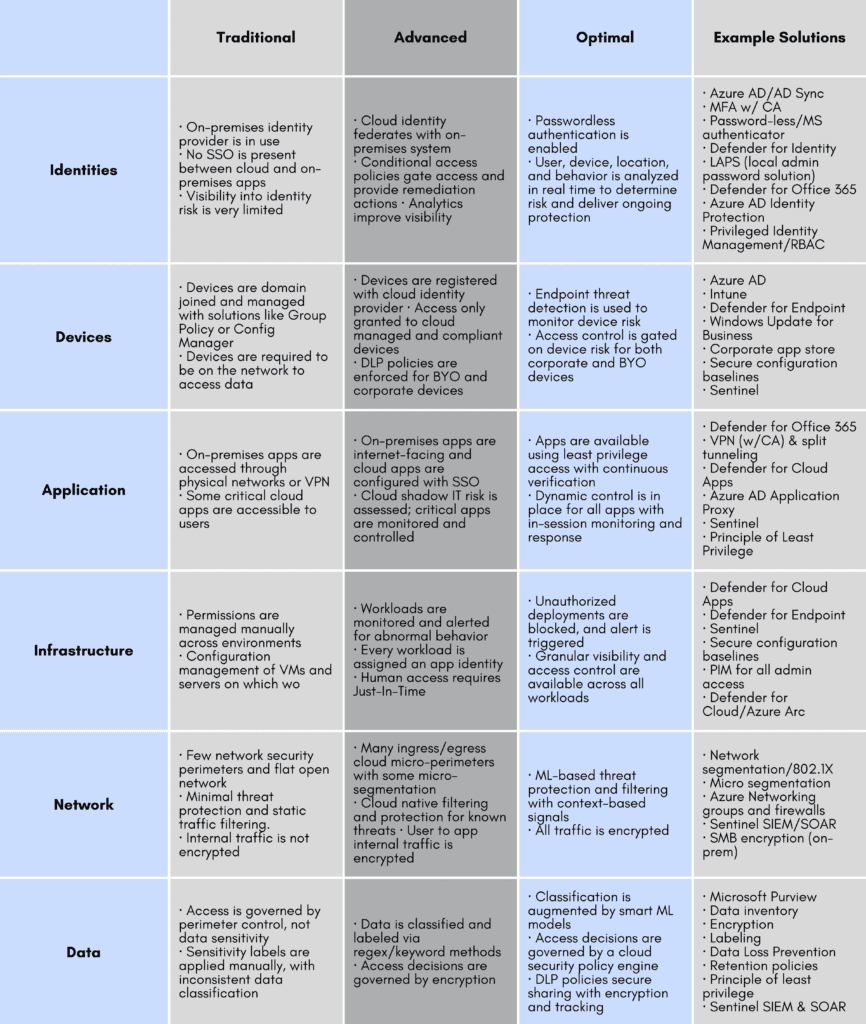
This chart shows the securable elements in the left column and the relevant Microsoft solutions to secure those elements in the right column. Organizations should evaluate how they are securing each of the elements (Identities, Devices, Network, Data, etc.) and place their current technology and controls in the appropriate colored column. The further to the right you are, the closer you are to your Zero Trust goal for that element.
Identifying the End of Your Journey
If an organization has controls deployed as described in the blue column, that will indicate that it has completed the journey to Zero Trust. As you can see, many of the Microsoft cloud solutions that you have in your environment today are applicable to Zero Trust if deployed the right way. Some other points to note:
Given the depth and interaction of the solutions listed here, you can see that Zero Trust can only realistically be achieved through being intentional and building an architecture to achieve it. Once that is complete, however, securing future systems and data becomes much easier as you incorporate them into the design and have them leverage your existing security and control structure.

Strategic Advisor - Enabling Technologies