AudioCodes OVOC Server Security Vulnerability and Required Remediation
On August 20, 2023, AudioCodes published Product Notice #0511 – Vulnerabilities Discovered and Subsequent Mitigations in One Voice Operations Center (OVOC) Server. The article provides configuration information to mitigate possible security vulnerabilities on One Voice Operations Center (OVOC) servers. The notice includes the recommended steps to mitigate these issues.
Vulnerability
Remediation
There are two required changes to address the vulnerabilities:
Once the software upgrade has been completed, the passwords can be changed. The password changes are made through the “Security” section of the “OVOC Server Manager” tool in the OVOC console.
Here are the detailed mitigation steps for each of the four (4) vulnerabilities:
Upgrading from OVOC Server Version 8.0
Upgrading from OVOC Servers with Older Software
ncif Password
1. Using SSH, sign onto the OVOC server and switch to the “root” user.
2. At the “#” sign prompt type “EmsServerManager” and press the return key.
3. From the “Main Menu”, select option “7. Security”.
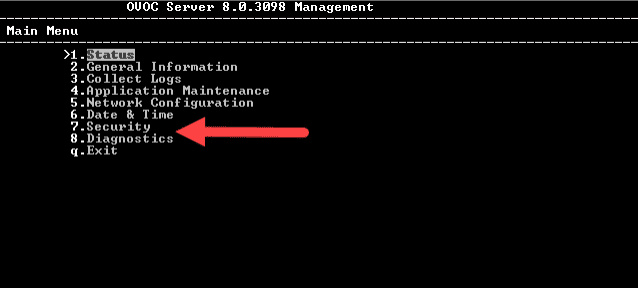
4. From the “Security” menu, select option “6. Security”.
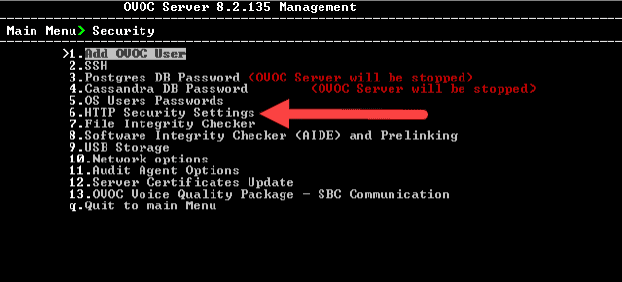
5. From the “HTTP Security” menu, select option “17. Change HTTP/S authentication password for NBIF directory”.
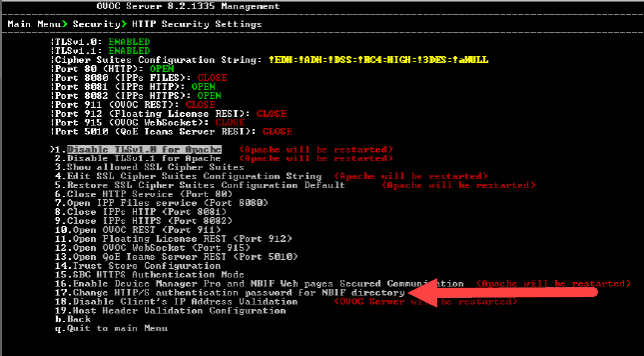
6. Type “y” and press enter in response to the question “Would you like to change HTTP/S authentication password for NBIF directory (Username: nbif)?”.
7. Follow the prompts to change the password. You may not be prompted for the old password.
8. The Apache server will restart.
9. Return to the “Security” menu.
acems and root Accounts
Default Database-PostgreSQL Password
1. From the “Security” menu, select option “3. Postgres DB Password”.
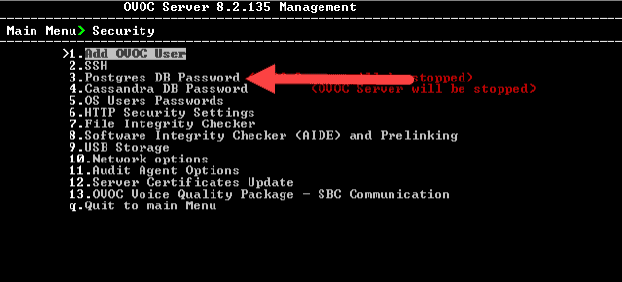
2. Type “y” and press enter in response to the question “Would you like to change Postgres DB password?”.
3. When prompted, type in the default password.
4. Follow the prompts to change the password.
5. Return to the “Security” menu.
Cassandra DB Password
1. From the “Security” menu, select option “4. Cassandra DB Password”.
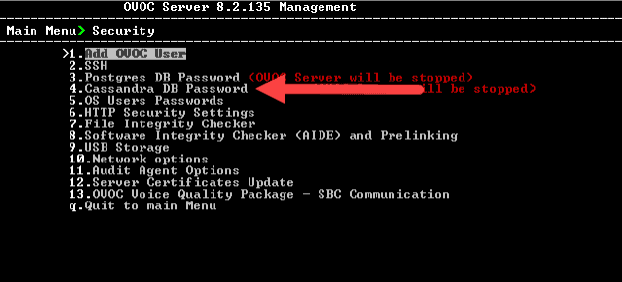
2. Type “y” and press enter in response to the question “Would you like to change Postgres DB password?”.
3. When prompted, for the “Current Password:”, press enter.
4. Follow the prompts to change the password.
5. Return to the “Security” menu.
Add an OVOC User
1. From the “Security” menu, select option “1. Add OVOC User”.
2. Enter the name of the new user and press enter.
3. Enter the password for the new user and press enter.
4. Type “y” to confirm your changes and press enter.
5. When prompted, for the “Current Password:”, press enter.
Summary
eGroup | Enabling Technologies is available and ready to answer any questions that you might have about this security update and its mitigation, as well as overall security for your enterprise. If you need help with this process or in implementing a security infrastructure for your organization, please contact us at info@eGroup-us.
Bibliography
All AudioCodes documentation can also be found in the Library section of the AudioCodes website.

Cloud Solutions Architect - eGroup | Enabling Technologies
Contact our team of experts to learn how you can protect yourself from vulnerabilities and strengthen your security!