Azure AD Third Party MFA Integration with DUO
3rd Party Multi-factor authentication Integration with Microsoft Entra ID (formerly known as Azure AD) and Conditional Access is available to allow administrators to use an alternative Multi-factor authentication provider instead of Azure Multi-factor authentication. This still requires Microsoft Entra ID (formerly known as Azure AD) Premium P1, which does include Azure Multi-factor authentication. It is relatively quick and simple to setup this integration for some providers, such as DUO.
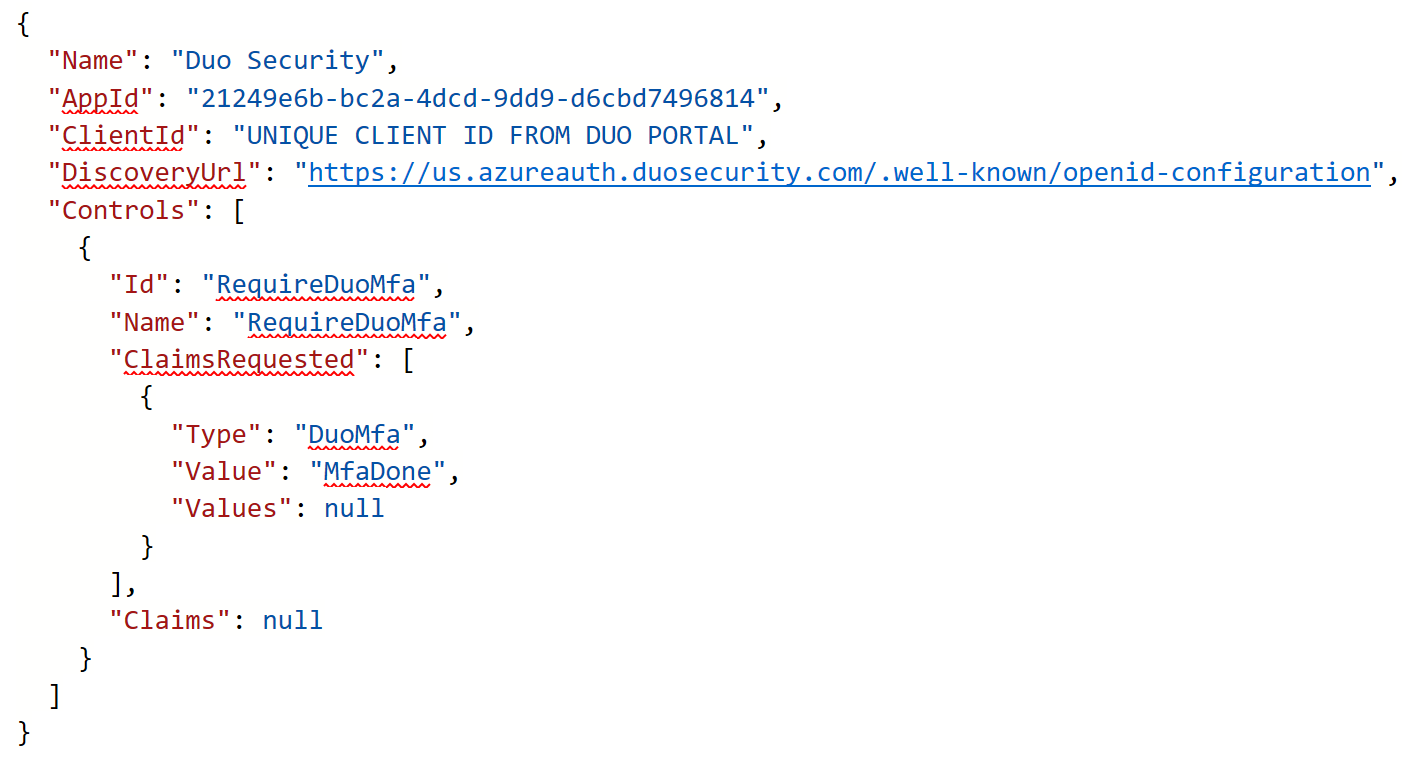
DUO has a documented process at https://duo.com/docs/azure-ca. Within the DUO Admin Panel, you need to add Microsoft Entra ID (formerly known as Azure AD) as an application to protect. This will prompt for a Global Administrator login to authorize the integration. Once complete, DUO will provide a bit of JSON code. This is used on a custom control in Microsoft Entra ID (formerly known as Azure AD) Conditional Access.
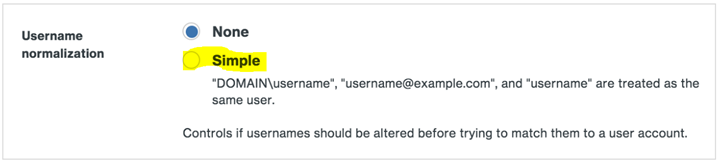
An additional setting should be changed in DUO portal that defines username formats. It is recommended to allow multiple username formats. Within the properties of Microsoft Entra ID (formerly known as Azure AD) in the DUO Admin Portal, go to Username Normalization and change from None to Simple. With normalization off, the usernames “jdoe,” “DOMAIN\jdoe,” and “jdoe@domain.com” would be three separate users in Duo.
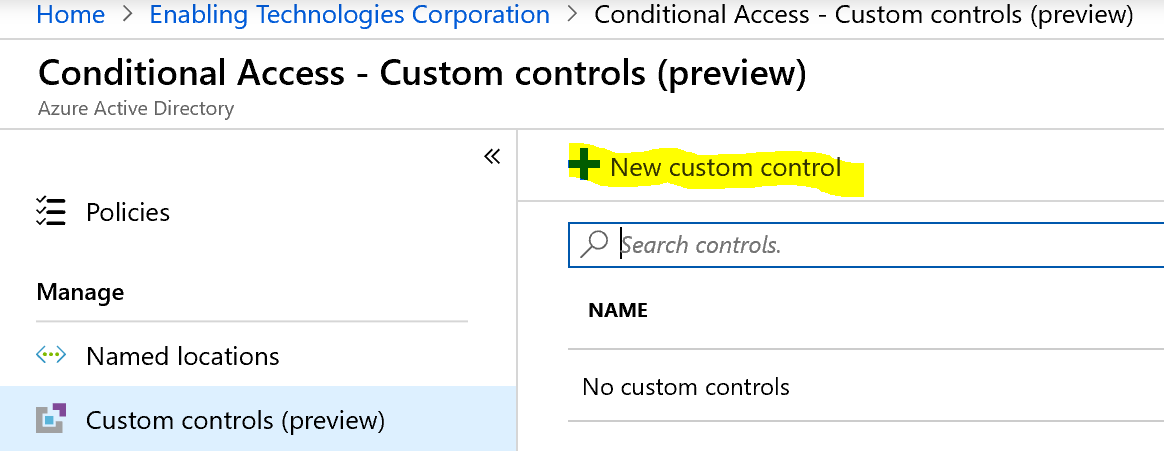
Once the integration is complete on the DUO Admin Panel, a custom control needs to be created in Microsoft Entra ID (formerly known as Azure AD) Conditional Access using the JSON code provided by DUO. Once created, the option will show up as a Grant option within a Conditional Access Policy.
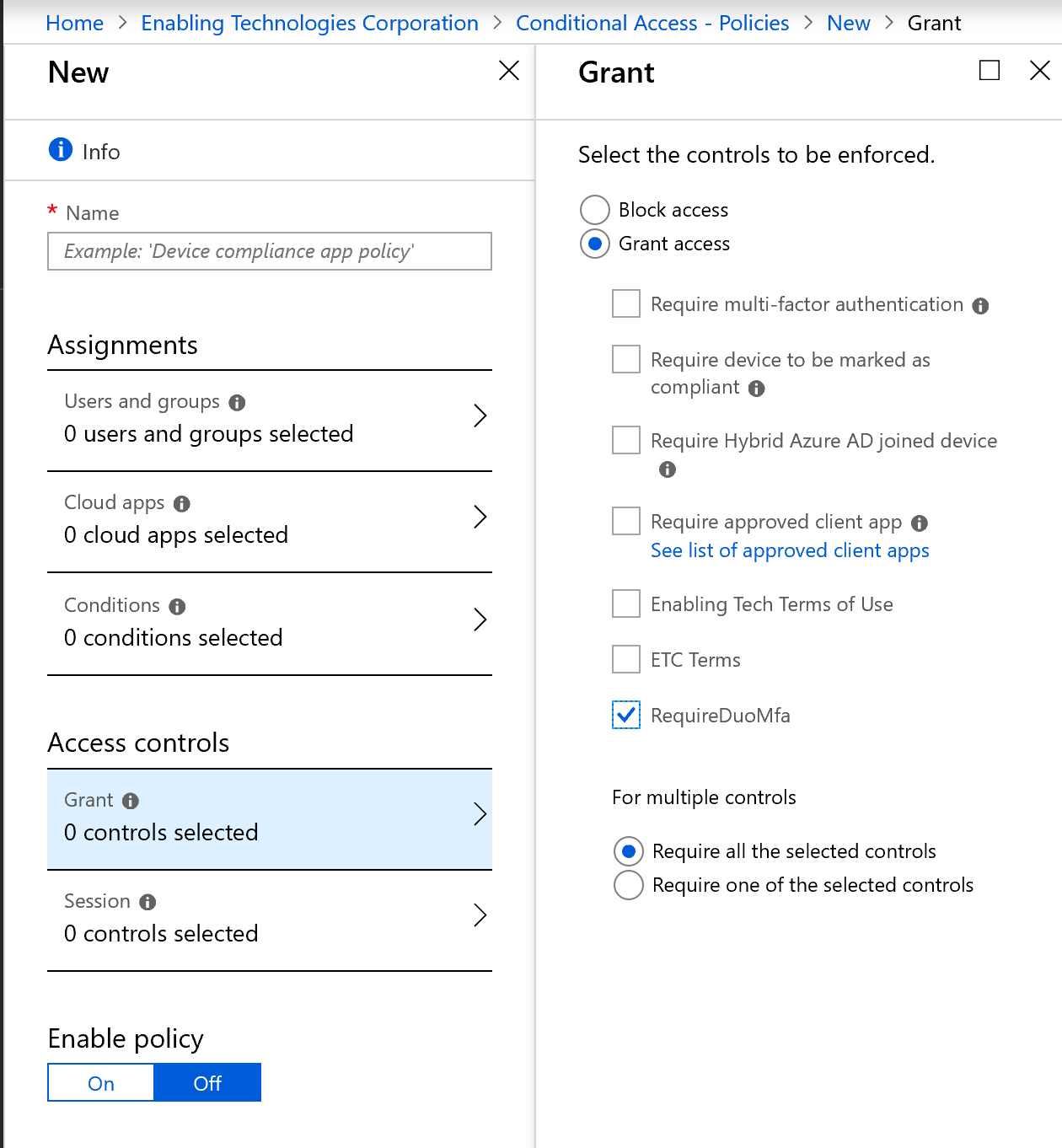
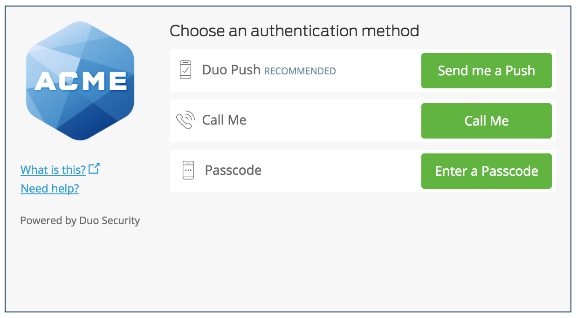
Once complete, DUO Multi-factor authentication can be used to protect the wide range of scenarios that Conditional Access allows for within Microsoft Entra ID (formerly known as Azure AD). Users will be redirected to their selected DUO options to satisfy the Multi-factor authentication prompt after authenticating to Azure Active Directory with their credentials.
Other supported Multi-factor authentication providers should have a very similar process to go through with the key being the custom control. Bear in mind that Microsoft is continuously developing the capabilities of Azure Multi-factor authentication with native integration to Azure Active Directory. That native integration allows for advanced capabilities such as Password-less Sign On, which is not available for 3rd party Multi-factor authentication partner integrations.
Using Azure Multi-factor authentication to protect against specific Office 365 apps, such as Exchange Online, will also enforce an Multi-factor authentication prompt during login to the Office 365 Portal (portal.office.com). However, with 3rd party Multi-factor authentication providers, this does not work. Users can still log into the Office 365 Portal without an Multi-factor authentication prompt and will only be prompted when accessing the specific application being protected.
If you already have a supported 3rd party Multi-factor authentication Provider deployed and are looking to expand upon your current protection capabilities into Microsoft Entra ID (formerly known as Azure AD), contact us to see how we can assist with your security goals.
You can also check out other security offerings at our Security page on our website.
Work with our team of Cloud Computing Consultants who have done this so many times they know all of the “minefields” to prevent missteps.