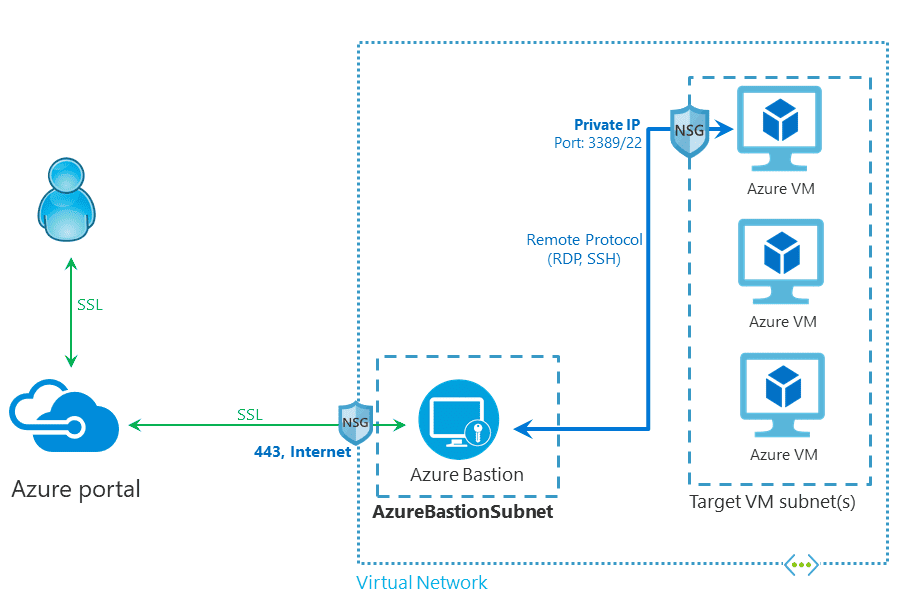
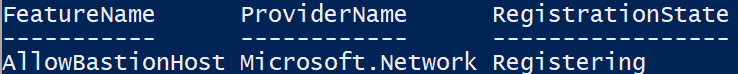
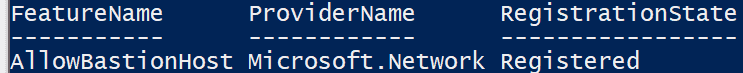
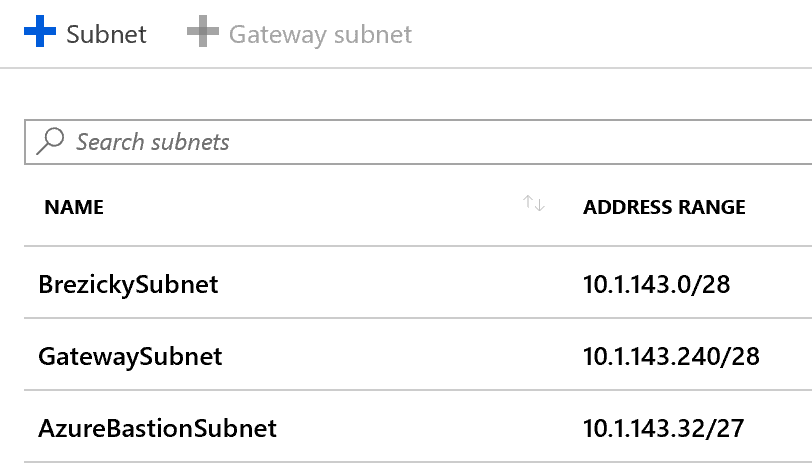
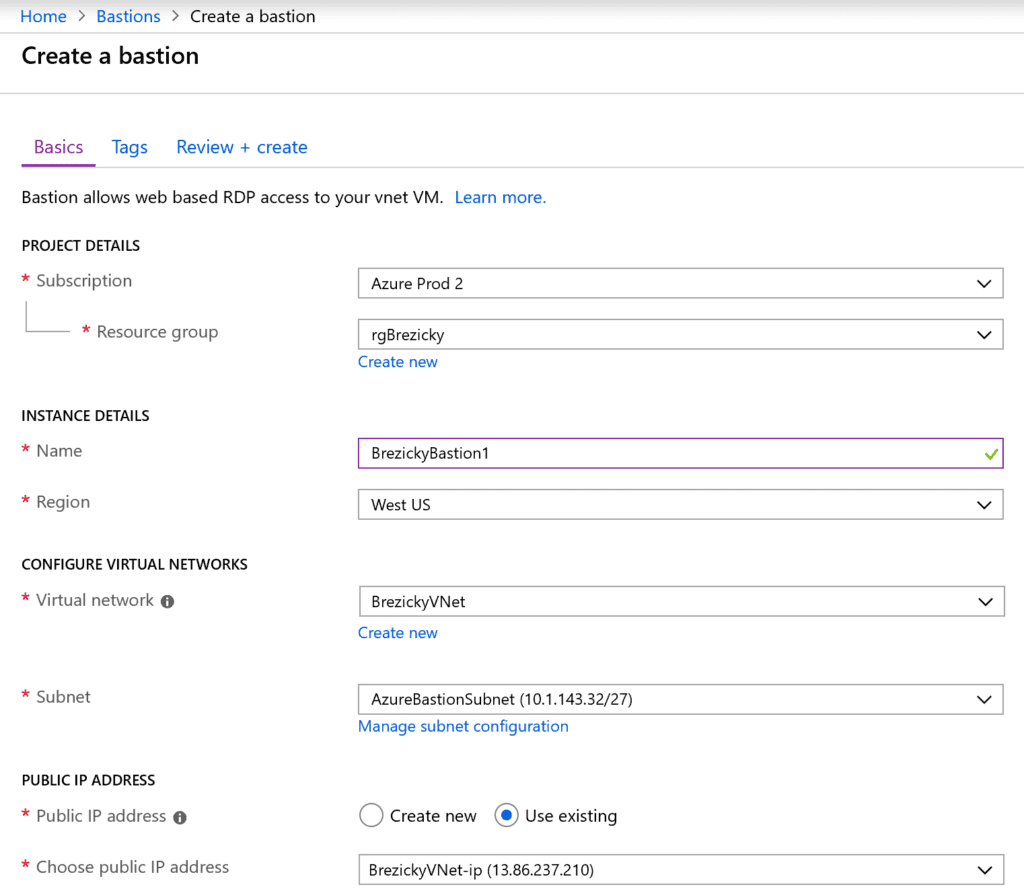
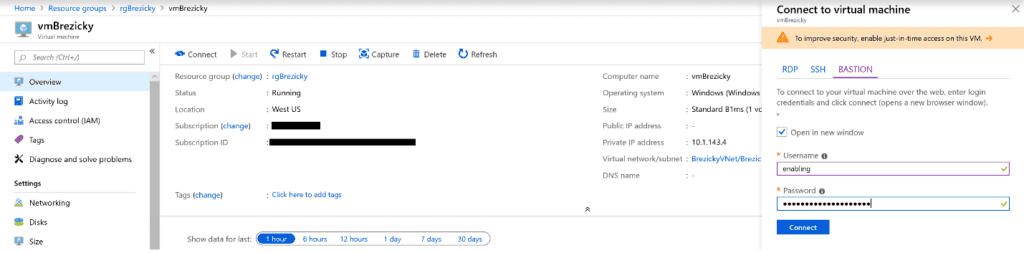
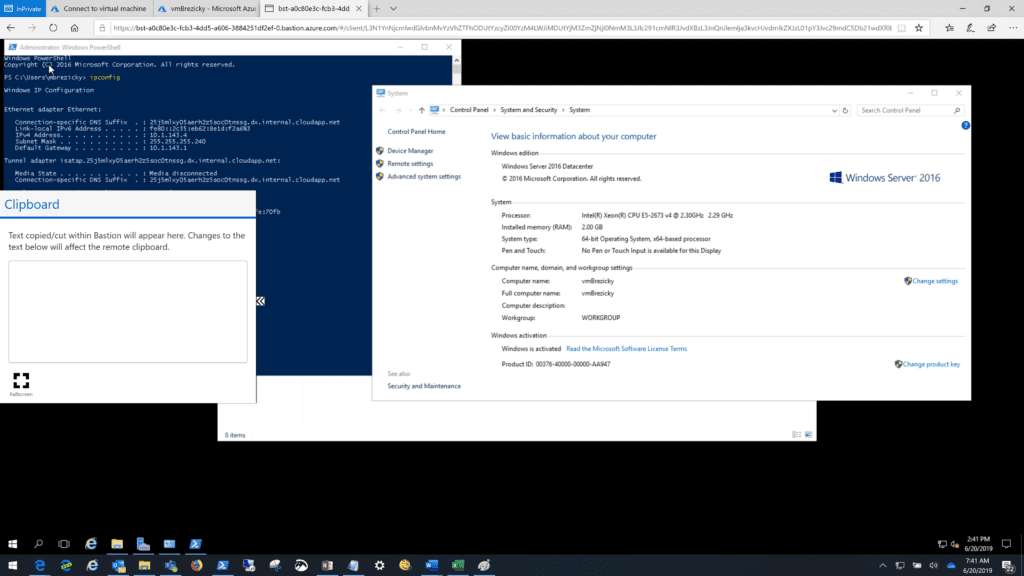
Azure Bastion is quick, easy, secure, and cost effective way to provide connectivity into Azure resources that you do not want direct connections to. It is an agent-less solution and a true replacement to jump box servers as a PaaS solution. You can configure a dedicated Network Security Group (NSG) to lock down access to Azure Bastion for ingress and egress connections. While only in public preview, Microsoft is still working on extending its capabilities to integrate with Microsoft Entra ID (formerly known as Azure AD) as well as work with traditional RDP and SSH clients to connect to the service.
eGroup | Enabling Technologies can help you properly prepare for moving to Azure based on Microsoft Best Practices. You can check out more in the Azure section of our website.