In this blog post, I will show you how to create Intune Endpoint Security Windows Firewall Policy and Firewall Rules to block outbound traffic using reusable group settings. This is a useful scenario for organizations that want to restrict the network access of their devices to specific top-level domains. By using Intune, you can manage the firewall settings of your devices remotely and apply them to different groups of devices based on your needs.
What are Endpoint Security Windows Firewall Policy and Firewall Rules?
Endpoint Security Windows Firewall Policy is a feature of Intune that allows you to configure the Windows Defender Firewall settings of your devices. You can create policies that define the firewall profile, the default action, and the notifications for inbound and outbound traffic. You can also create Firewall Rules that specify the conditions and actions for allowing or blocking specific traffic based on the protocol, port, application, or IP address.
By using Endpoint Security Windows Firewall Policy and Firewall Rules, you can control the network access of your devices and protect them from unwanted or malicious traffic. You can also create different policies and rules for different groups of devices based on their roles, locations, or security requirements.
Deployment
In Microsoft Intune, we will first create an Endpoint Security Firewall Reusable group. Then we will create a standard Firewall policy, and create Firewall rules to block top-level domains using the reusable group. I highly recommend testing this with a test device before rolling out to pilot groups and production.
How to Create Reusable Settings for Endpoint Security
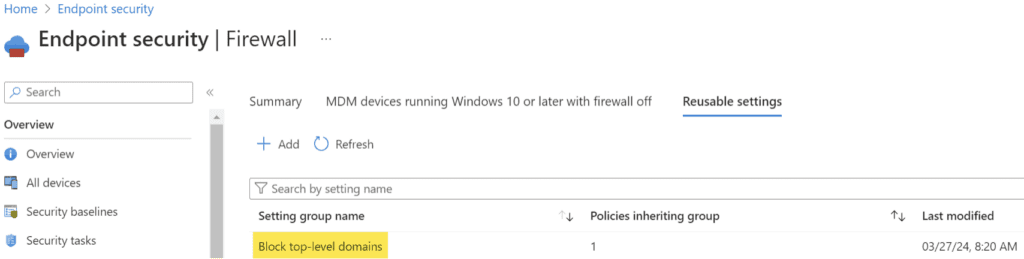
One of the benefits of using Intune to manage your firewall settings is that you can create reusable settings. Reusable settings are a collection of settings that you can apply to multiple policies or rules without having to configure them individually. For example, you can create a reusable settings group that defines the IP addresses of your trusted network and apply it to multiple firewall rules that allow traffic from those addresses. In this article, we will use a reusable settings group to block top-level domains.
To create a reusable settings group for Endpoint Security Windows Firewall, follow these steps:
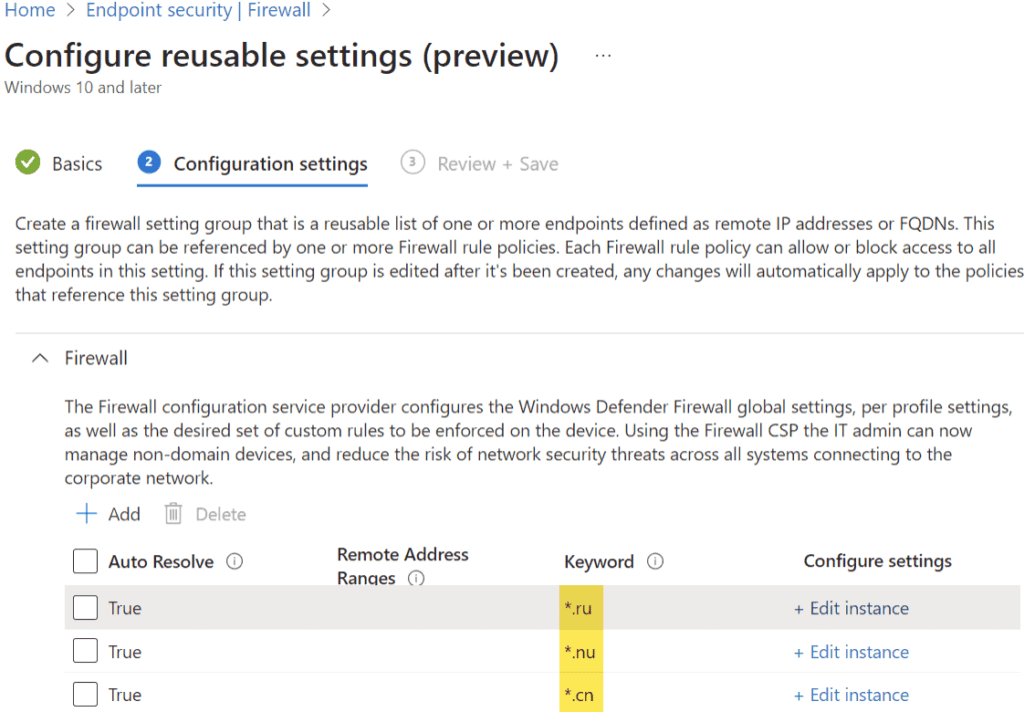
- Go to Endpoint Security > Firewall > Reusable Settings > Add
- Name: Blocked top-level domains
- Add: Select “edit instance:”
- Auto Resolve: True
- Keyword: *.ru
- Add additional required rules (if needed), then click Save
- Next, go to Endpoint Security > Firewall > Summary > Create Policy
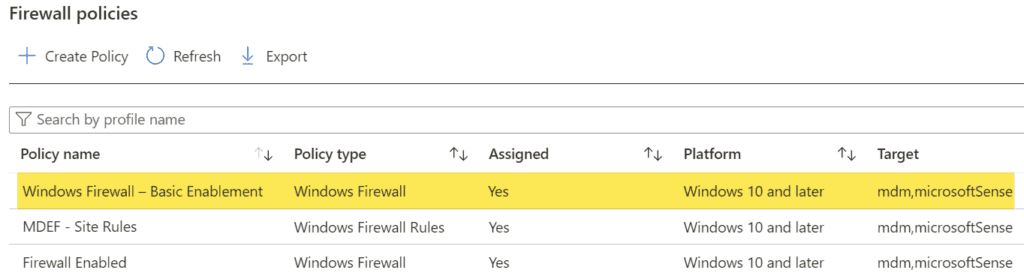
- Platform: Windows 10, Windows 11, and Windows Server
- Profile: Windows Firewall
- Name: Windows Firewall – Basic Enablement
- Configuration Settings:
- Enable Domain Network Firewall: True
- Enable Private Network Firewall: True
- Enable Public Network Firewall: True
- Assignments: Assign your test group of users/devices
- Save the policy
- Next, go to Endpoint Security > Firewall > Summary > Create Policy
- Platform: Windows 10, Windows 11, and Windows Server
- Profile: Windows Firewall Rules
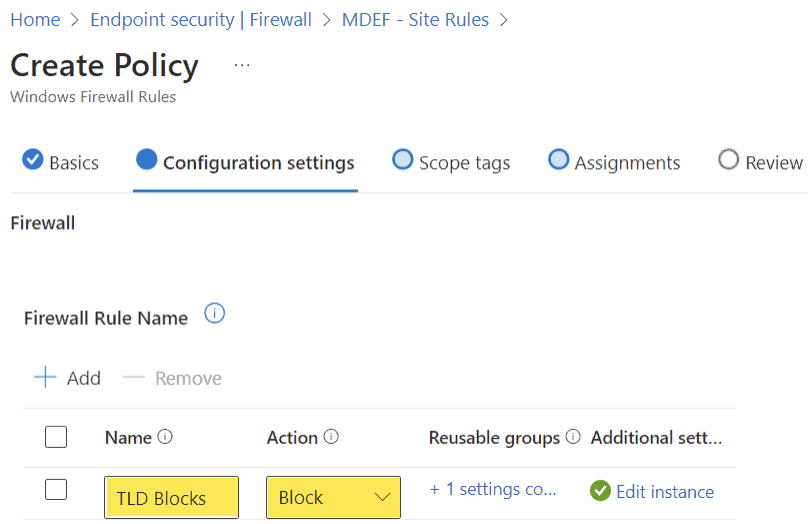
- Name: Block specific TLDs
- Configuration Settings > Firewall:
- Firewall Rules: Select Add
- Name: TLD Blocks
- Action: Block
- Reusable Groups: Click on the “+ Set reusable settings” hyperlink and add your “Block top-level domain” reusable settings group.
- NOTE: If your reusable settings group(s) are not showing up, zoom out on your browser window to see them!
- Click Save
- There is no need to configure anything under “Additional Settings” to get this to work. (You can configure additional settings such as interfaces, network types, port ranges, etc.).
- Firewall Rules: Select Add
-
- Assignments: Assign your test group of users/devices
- Save the policy
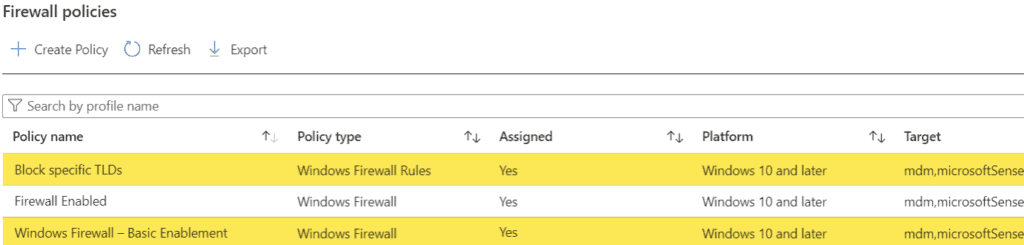
End-User Experience
Once the policies are applied, when trying to access websites containing the “wildcarded” top-level domain, users will experience “web page not available.”
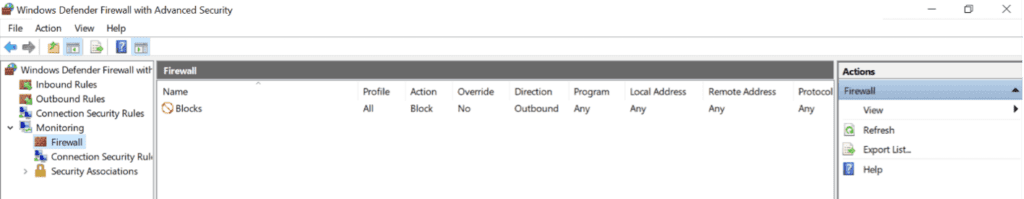
On the device, Firewall Advanced, you will see a blocked rule under Monitoring -> Firewall.
Conclusion
In this blog post, we have shown you how to use Microsoft Intune to create an Endpoint Security Windows Firewall Policy and Firewall Rules to block top-level domain access using reusable settings groups. This is a useful way to manage the network access of your devices and prevent data leakage or unauthorized connections. By using Intune, you can create and apply different firewall settings to different groups of devices based on your needs.
We hope you found this blog post helpful and informative. If you have any questions, feedback, or require assistance, please contact us here or complete the form below. To learn more about our Microsoft Intune services, and how we help our clients with their Modern Endpoint Management strategy read more here.
Thank you for reading!
Learn More About Microsoft Intune
Contact our team today to get started with Microsoft Intune or get your questions answered by our experts!



