Microsoft Intune LAPS (Local Administrator Password Solution) is a feature that allows you to manage the local administrator passwords of your Windows devices enrolled in Intune. It helps you prevent unauthorized access, pass-the-hash attacks, and lateral movement by generating random, complex, and unique passwords for each device. You can also set expiration policies and view the passwords in the Azure portal.
However, Intune LAPS requires that your devices have the LAPS agent installed and configured, which can be a challenge for some scenarios. For example, if you have devices that are not domain-joined, or if you have devices that have existing local administrator accounts with custom names or passwords, you may need to perform some additional steps to ensure that Intune LAPS works properly.
In this document, we will show you how to deploy Intune LAPS using a remediation script that can handle these scenarios. We will also show you how to use an endpoint security protection policy that leverages app protection to prevent unauthorized access to the LAPS passwords.
Prerequisites
- A Microsoft Intune subscription.
- Admin account that has global administrator or Intune administrator permissions.
- Windows 10/11 devices enrolled in Intune (Entra ID or hybrid Entra ID joined devices).
- A remediation script that can detect and remediate (example provided).
- Use of remediations requires Windows license verification to be enabled. Additional info can be found here.
- An app protection policy that can enforce LAPS passwords (example provided).
Steps
- In the Intune Admin Portal, ensure Windows license verification is enabled. To enable Windows license verification, your tenant must have E3/A3 or above licenses. You must be a Global Administrator or an Intune Administrator.
-
- To enable Windows licenses verification via the Intune Admin portal:
- Tenant administration -> Connectors and tokens -> Windows data -> Windows licenses verification: On
- To enable Windows licenses verification via the Intune Admin portal:

2. Create a remediation script(s) that can detect the existence of the local admin account, and if not, create the account and add it to the local administrators group. The following are examples you can use to detect and remediate:
-
-
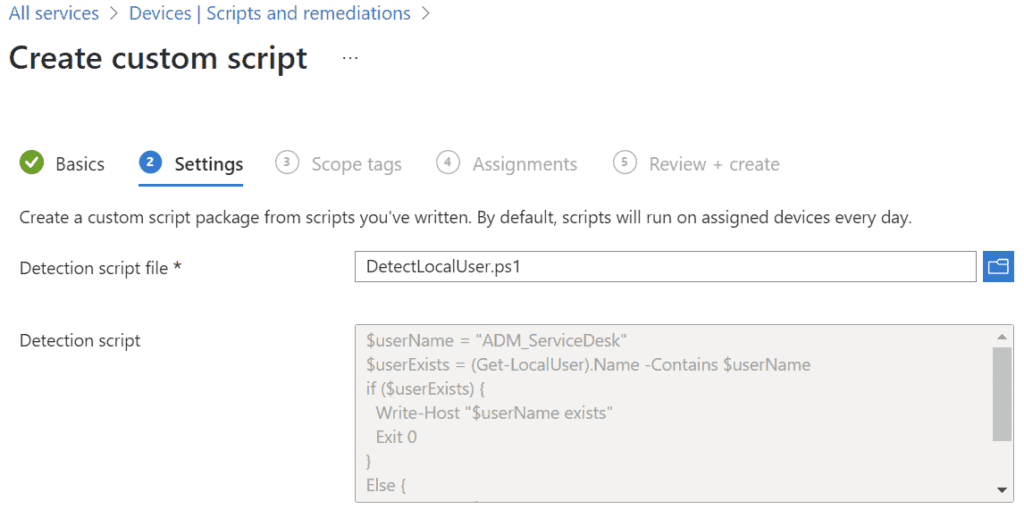
- Detect:
$userName = “ADM_ServiceDesk”
$userExists = (Get-LocalUser).Name -Contains $userName
if ($userExists) {
Write-Host “$userName exists”
Exit 0
}
Else {
Write-Host “$userName does not exist.”
Exit 1
}
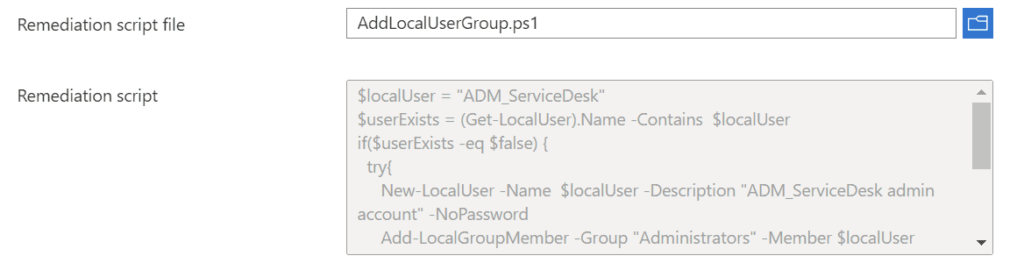
- Remediate
$localUser = “ADM_ServiceDesk”
$userExists = (Get-LocalUser).Name -Contains $localUser
if($userExists -eq $false) {
try{
New-LocalUser -Name $localUser -Description “ADM_ServiceDesk Admin Account” -NoPassword
Add-LocalGroupMember -Group “Administrators” -Member $localUser
Exit 0
}
Catch {
Write-error $_
Exit 1
}
}
- Detect:
-
3. Create the Intune remediation script package as follows: (NOTE: I recommend you test this package with some test users and devices prior to rolling out to the masses.)
-
- From the Intune Admin portal, go to Devices -> Manage Devices -> Scripts and Remediations -> Remediations.
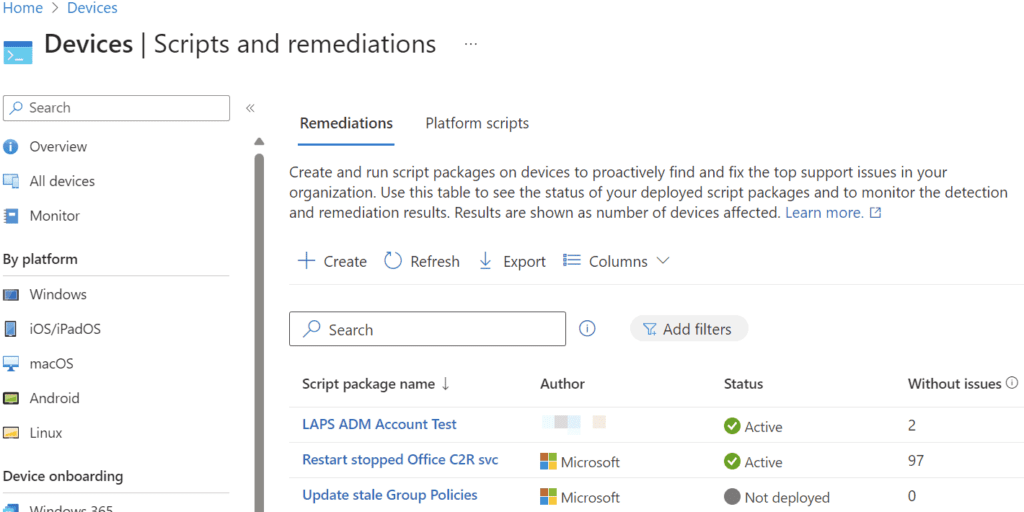
-
- Create a new Remediation package by providing:
- Display name, description, detection scripts, and remediation scripts.
-
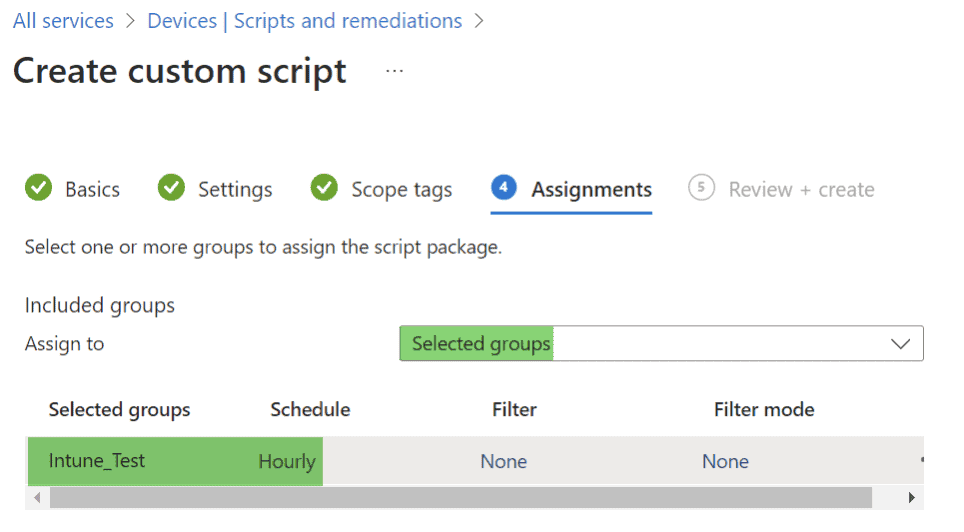
- Assign scope tags and users/groups. Once you add the group(s), you can configure the schedule for which the remediation script should run (hourly, daily, etc.). Once your groups are configured, save the script.
4. Create a LAPS policy via Intune Endpoint Security Account Protection that defines password requirements and backs up the password to Entra ID for the local admin account.
- From the Intune Admin portal, go to Endpoint Security -> Manage -> Account Protection:
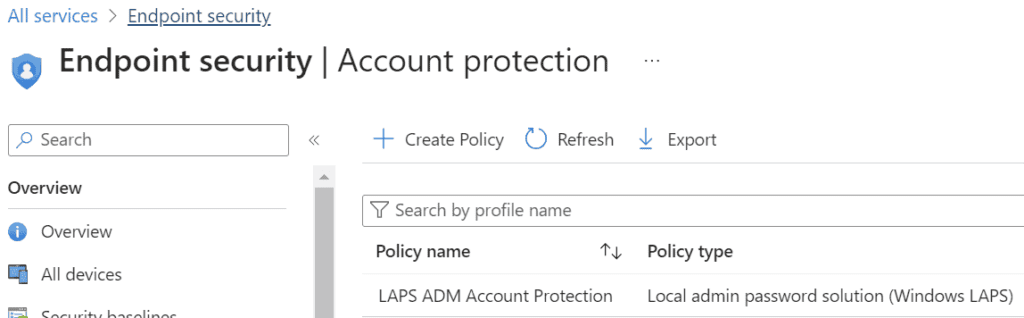
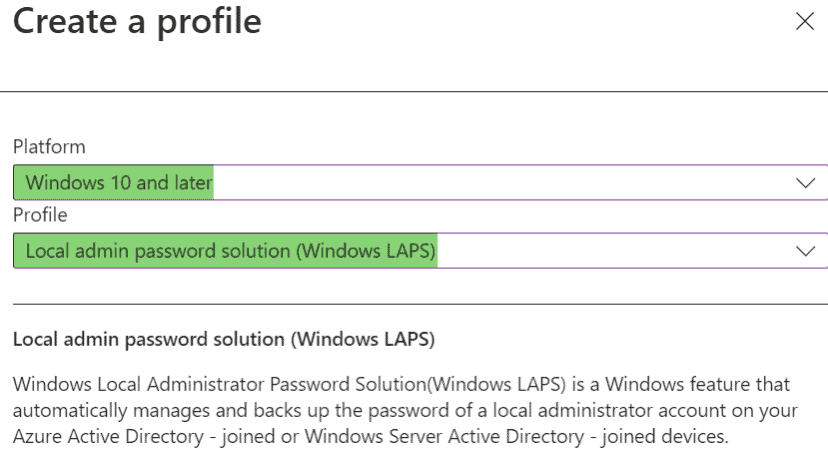
- Create a new profile for Windows 10 and later using “local admin password solution (Windows LAPS):”
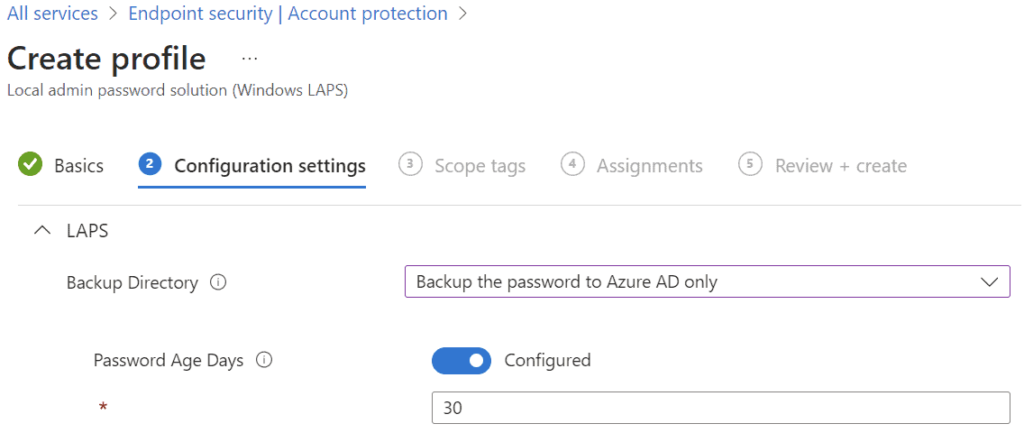
- Configure LAPS backup directory and password age:
- Configure LAPS Administrator Account Name. This will be the administrator account used in the remediation script:

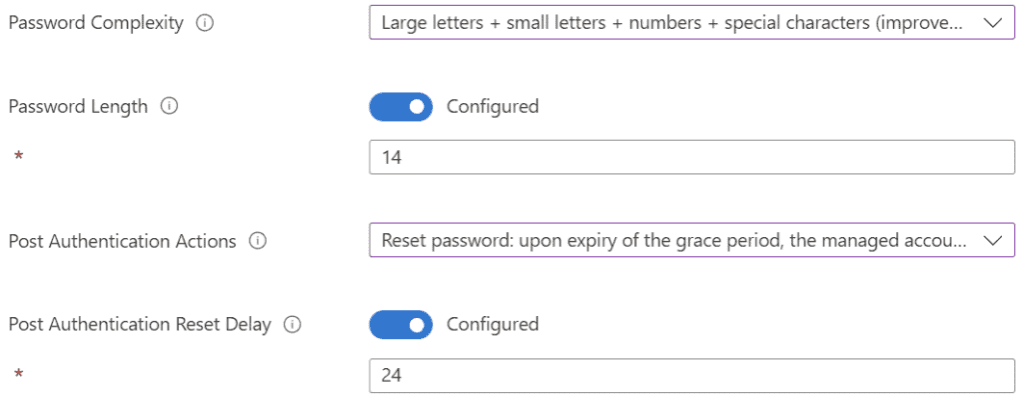
- Configure LAPS password complexity, length, and post-authentication options:
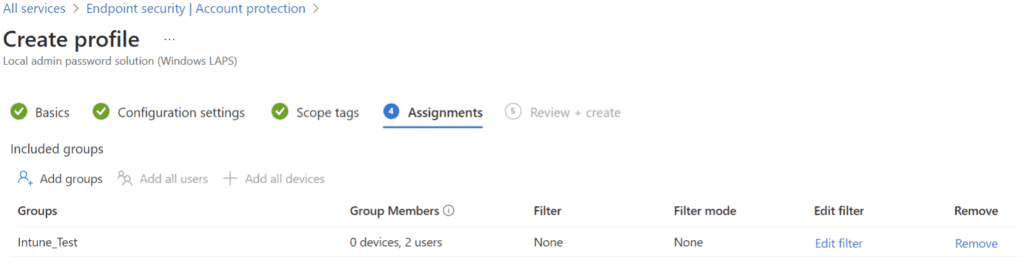
- Assign the scope tag(s) if required, then assign the LAPS policy to a group, and save the policy:
5. Verify the deployment and view the passwords. (NOTE: This will take some time for the remediation script to run and the LAPS policy to assign to the device.)
-
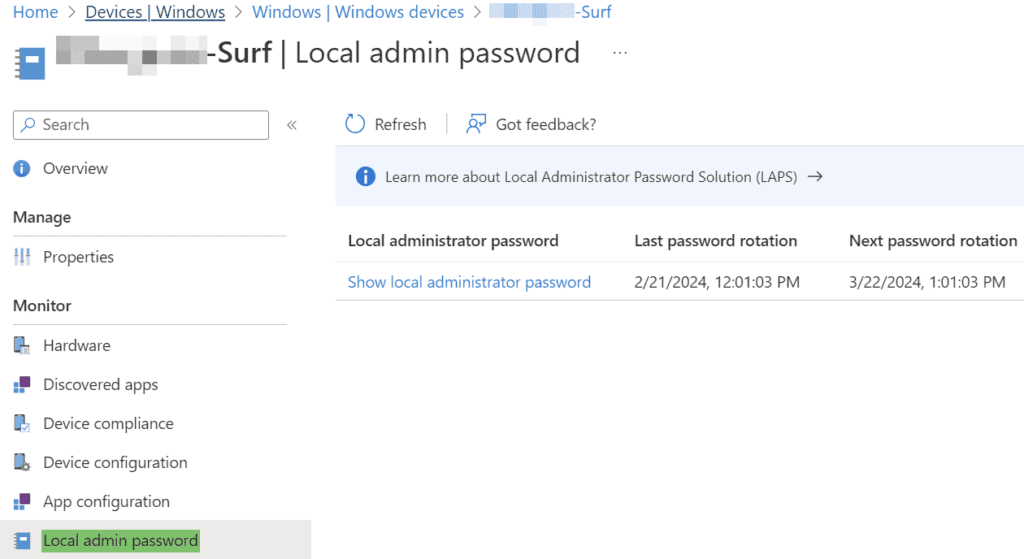
- Intune – You can search for a Windows device in Intune and view the LAPS password and admin account:
- Devices -> Windows Devices and search for a device.
- Under Monitor, select “Local admin password.”
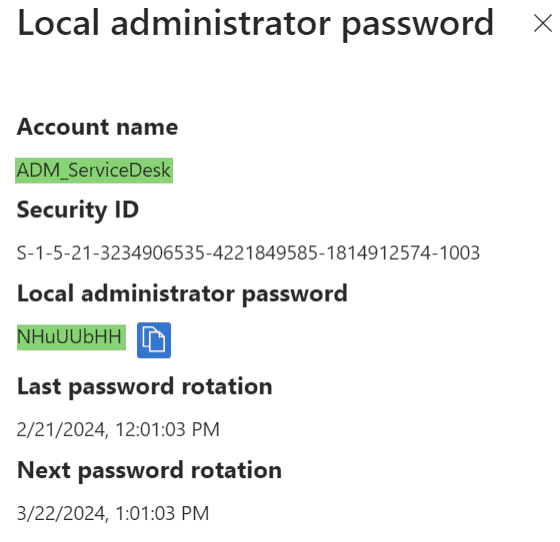
- Select the “Show local administrator password” hyperlink to view the local admin account and password. This menu should flyout from the right. You can now use this combo to log into the device as a local administrator.
- Intune – You can search for a Windows device in Intune and view the LAPS password and admin account:
-
- Entra ID – From Entra ID portal:
-
-
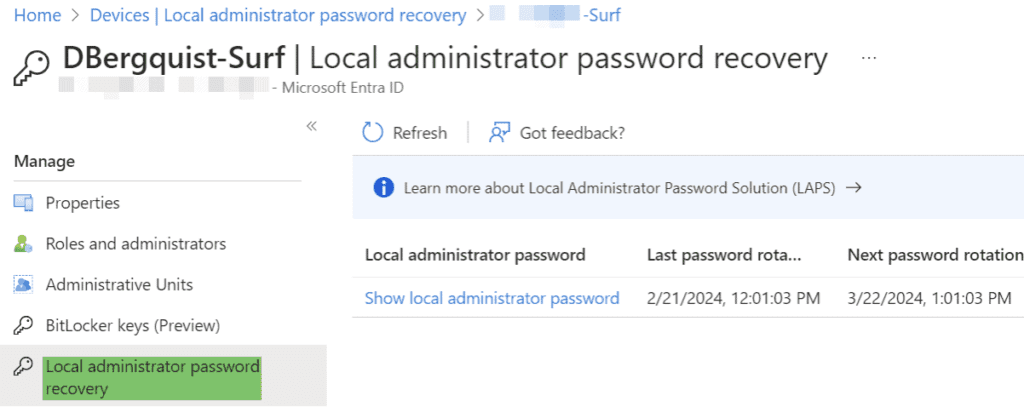
- Select Devices -> All Devices -> Local administrator password recovery.
- Search for a device and select “local administrator password recovery.”
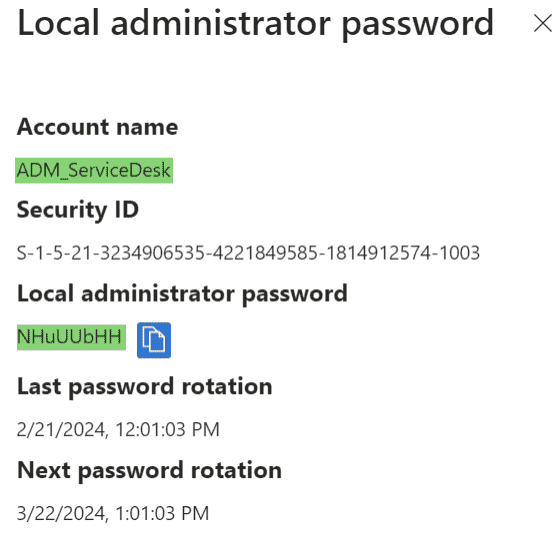
- Select the “Show local administrator password” hyperlink to view the local admin account and password. This menu should flyout from the right. You can now use this to log into the device as a local administrator.
-
6. You can rotate the LAPS Password manually.
-
- From Intune:
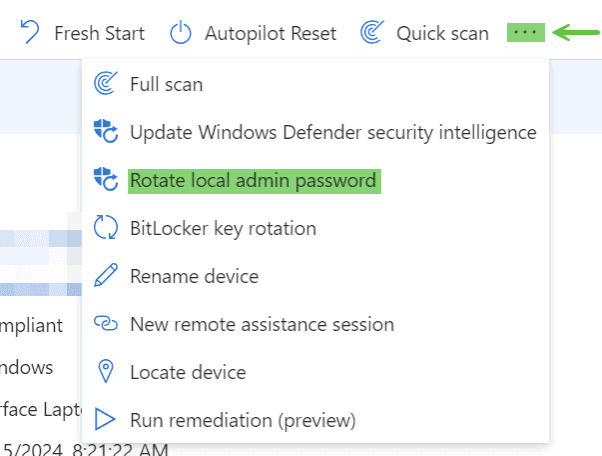
- Devices -> Windows Devices and search for a device.
- Click the 3 dots in the upper right-hand corner and select “Rotate local admin password.”
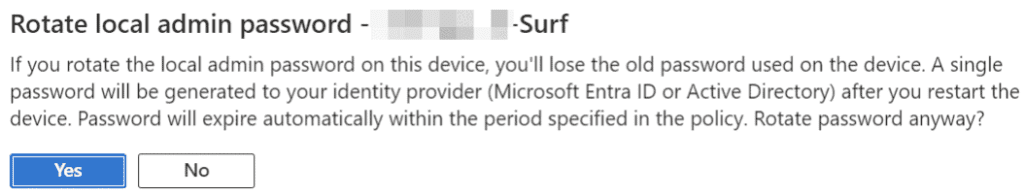
- Click on “Yes” to rotate the LAPS on the device. Once the device is rebooted, a new password will be generated to Entra ID.
- From Intune:
7. Kick off the remediation script per device (if required).
-
- From Intune:
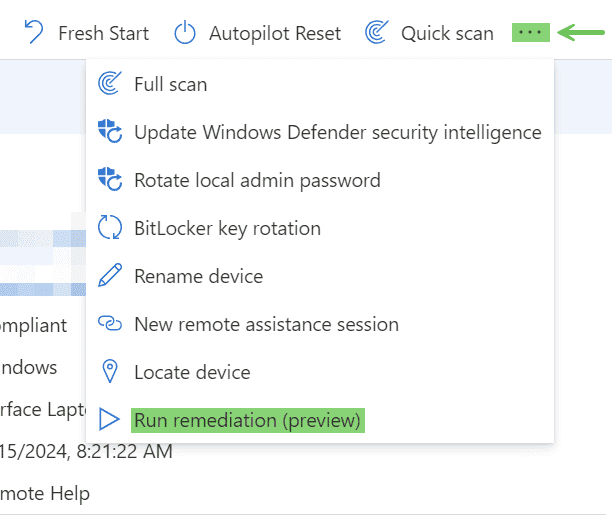
- Devices -> Windows Devices and search for a device.
- Click the 3 dots in the upper right-hand corner and select “Run remediation (preview).”
- From Intune:
Conclusion
By following these steps, you can deploy Intune LAPS with a remediation script and an endpoint security account protection policy that can enhance your device security and compliance. You can also use the Azure portal to view and manage the local administrator passwords of your devices. Contact eGroup Enabling Technologies for all your Microsoft Intune, M365, Entra, Azure needs.
Learn More About Microsoft Intune
Contact our team today to get started with Microsoft Intune or get your questions answered by our experts!



