How Government Institutions Can
Manage Cyber Insurance Increases

Growing trends and recent news have shocked the cyber insurance system. With cost and coverage changes, government institutions are simply seeking to attain reasonably affordable cyber insurance. This blog summarizes a spirited debate amongst subject matter experts on the topic in January 2023. Contributors include a former .gov insurance negotiator, Mehran Basiratmand, a cyber insurer, Doug Schulkin, and cyber security expert David Branscome.
The trends and shocks include:
Each topic is explored by our experts in turn below.
Managing Rising Rates
Cyber insurance rates increased 28% in Q4 2022 and 48% in Q3 in the USA (Marsh). While some correction is expected as new entrants to the market increase capacity, insurers will continue to hike rates until attacks subside and organizations adequately improve defense and detection.
To keep rates in check, experts advise to
Insurance industry executive Schulkin advises to communicate early and often, first during broker negotiations and then, once the policy is active. “Cyber insurance is not a lot like other insurance,” Doug began. “There’s high incentive to report all the time,” which defies the stigma of a demerit system where customers opening too many claims are dropped or see rates spike. “In fact, it’s quite the opposite,” he continued. “Good underwriters and carriers look at that situation and say, ‘OK, these people are very cognizant, they’re very aware of their data risk management,’ and note in their file to make sure that they don’t lose them as a customer.”
Basiratmand agrees that strong communication with a broker is part of a four pronged approach, with a strong internal team (or Managed Security Services Provider) handling Extended Detection and Response (XDR) as the second leg. Continuous improvement, often involving a third-party health check of security posture, is a third pillar. “Your staff are wonderful,” he said, “but they are only going to report what they can report, so getting a third-party company to come in that basically has no skin in the game has been extremely valuable.” Finally, the insurance broker itself rounds out the four important aspects.
Speaking of health checks, Branscome asserts that Microsoft tools embedded in Microsoft 365 and Azure Secure Score will call out much of what a cyber insurer will look at. “It’s going to look at MFA, it’s going to look at privileged access management, things like that, so you can use these free tools and start on that journey before you decide about cyber insurance.”
Doug stressed David’s point for organizations make a plan to inform the financial decision about insurance. “The first step in this process is to make yourself safe, with good cyber hygiene,” he began. He advises using the resources of insurance brokers, cyber lawyers, and technical companies to help. “Then, once you assess how vulnerable you are,” Doug continued, “you can compare the risk you’re willing to take against your budget.” Making an insurance purchase without knowing your relative risk is backwards.
Managing Stricter Requirements
As risks evolve, so do insurers’ requirements. Schulkin debunked a major myth. “MFA isn’t the silver bullet everyone thinks it is. It is still a very good mitigation tool and a great benchmark for insurance carriers to see how safe you are.” To that end, some carriers are asking questions about MFA in very specific situations, rather than a single catchall question of ‘Do you use MFA?’
Doug continued to explain the thought process and importance of the cyber insurance questionnaire. “Insurers evaluate single question quite carefully and they go into an equation. It’s mostly science, a little bit of art, on the part of insurance carriers.” He stresses that “When you fill these out and C-level signs off, you are saying ‘If we ever have to go to court, I’m promising that these things are in place.’ Insurance carriers have every right to deny payment if it’s wrong.’”
He admits, “That sounds bad, but it’s not, if you just take the time with your insurance broker and take the questions seriously.” He also advises to be honest about your gaps. “People feel they need to be perfect, but there’s no such thing as perfect, and at some point you have to take a risk.”
Factoring Nation State Risks
Lloyd’s of London is the most public cyber insurer to begin “excluding liability for losses arising from any state-backed cyber-attack.” Assessing the likely ramifications requires a look back before looking forward.
Think back to the SolarWinds supply chain attack, attributed to Russia after many months of deliberation. Would the recoveries of the approximately 18,000 affected public and private sector customers have been covered? Add to that Russia’s creation and widespread damage of NotPetya in 2017, the largest cyber incident in history at $10B in damages. Would NotPetya’s drive-by victims outside of Ukraine (like Maersk, Merck, state hospitals, etc.) have been covered?
Looking forward, the litigation around this blurred line is likely to be thick. Attribution to state actors has been slow if nonexistent. Insurers who are asked to make payments immediately may delay payments and require further proof.
As a result, some organizations are electing to self-insure. According to Branscome, “There has been a push by some cyber insurers to get people to self-insure to a certain degree. In other words, they’ll pay out, but only up to a certain level, which would help reduce the premiums that customers must pay.”
A recent government CIO told the author that if his organization were to take the necessary actions to comply with the insurer’s requirements, it’d take millions of dollars, and yet their rate would still increase $1M/year, with a $2M deductible. Putting away a multimillion-dollar slush fund for a safety net is becoming more a palatable alternative for some.
Big Data Illustrates Trending Vectors
What’s likely to happen next? While at a macro level, phishing and identity compromise are still the number one vector, a few trends are on the rise of note. The charts that follow are from metadata from Chubb’s Cyber Claims in the past three years, couple with commentary from the experts.
This first visual shows what instigated most of Chubb’s claims in the last three years (ending in 2022).
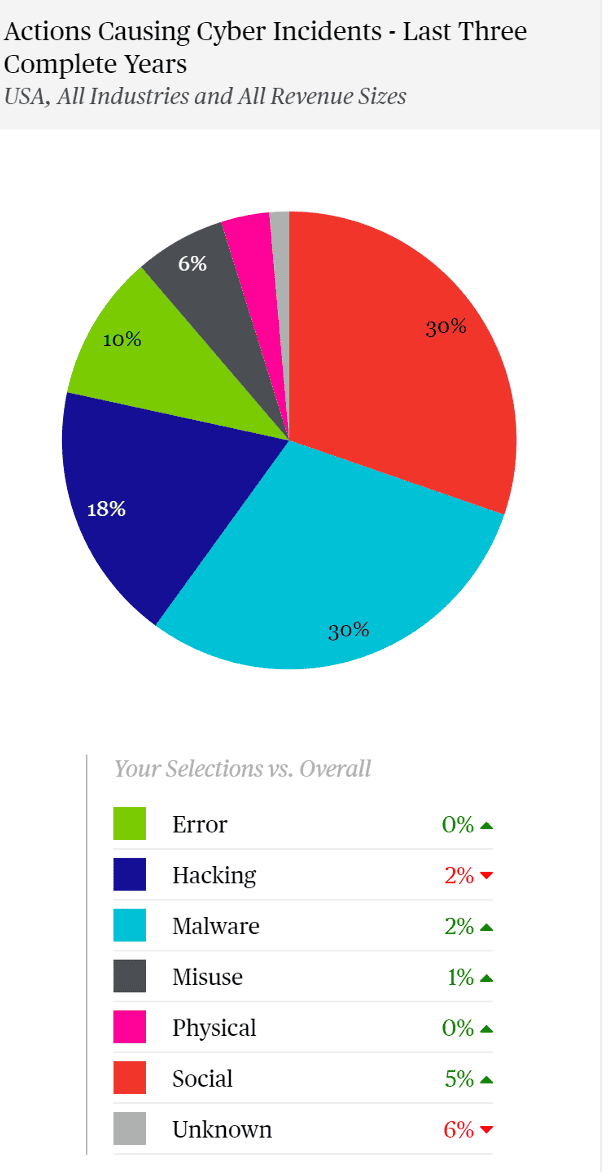
You can see the “people problem” is growing, with social engineering at 30% and a 5% growth. This is more than just Nigerian Prince phishing campaigns. Last year there were a few employees of, in some cases, large notable IT organizations, who were recruited on social media and eventually willingly gave up their credentials for money. In some cases, they even approved the MFA prompt when the malicious actor logged in.
Such LAPSUS$ extortion campaigns clearly bypassed existing edge or front-end technologies like MFA. This reinforced the necessity of a defense in depth strategy, including a focus on insider threats and monitoring end user behavior.
The idea of enforcing MFA with conditional access adds another layer to a well-protected environment. If logins are only permitted to legitimate credentials coming from legitimate, trusted machines, they could be provided with trusted access. Then, even if a willing employee approved a bad actor’s MFA prompt, unless the actor also had the willing employee’s machine, the login would’ve been blocked.
Conditional Access with device compliance similarly solves the rising “Adversary in the Middle Attack,” noted in a prior blog.
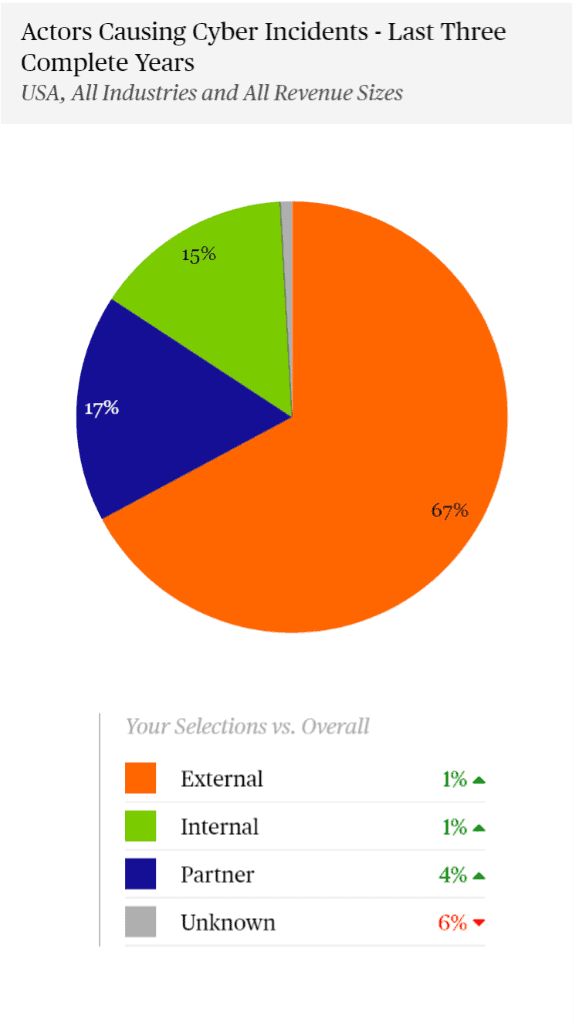
Chubb’s next pie chart shows what kind of actors were the source of their claims, and of note here is a growth in partner attacks.
In part, this rise comes from supply chain software attacks like SolarWinds, Kaseya, and ManageEngine. But it also comes from adversaries hopping from managed services’ provider networks into their downstream customers. That is because providers with access to multiple downstream customers’ systems are bigger targets.
In the wrong way, the average hacker isn’t going after mom and pop anymore. They’re going after the sources of many other downstream victims.
Branscome pointed out that “Gartner predicts that by 2025, 45% of organizations worldwide will have experienced attacks on their software supply chains” (a three-fold increase from 2021). He followed by advising that organizations factor in their vendors’ security practices during the IT procurement stages.
Finally, Chubb reported on the assets that are most often targeted in incidents. Servers are way up at 5% here, the network is up a bit at 2%, and the people are the target in some cases.
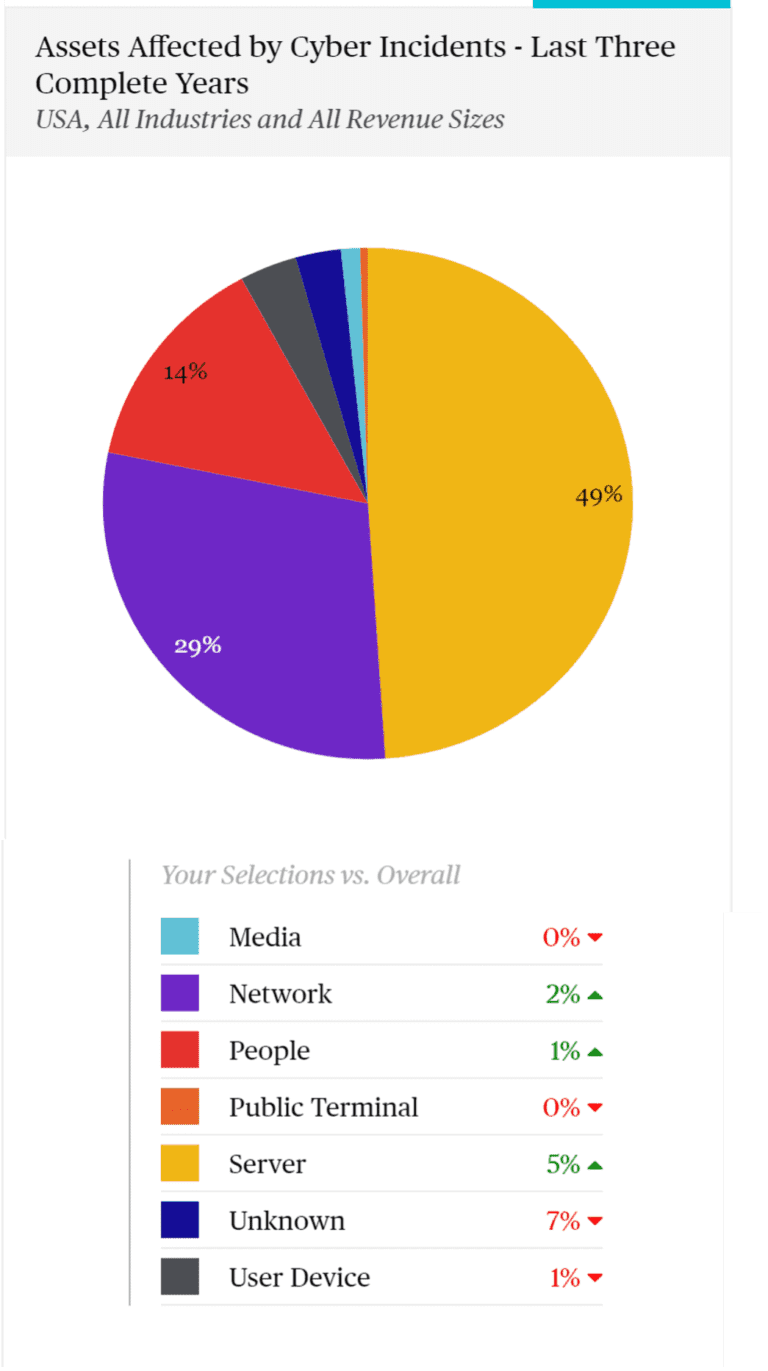
Basiratmand predicted that servers attacked by human-operated ransomware attacks will grow because “There’s still a large number of organizations that have not improved their security posture to the level that is required. It’s surprising to see how many organizations truly have not fully taken advantage of the tool set that is readily available at their disposal. Sometimes it’s funding, sometimes it’s the staffing. Attacks will continue because the bad actor doesn’t have to have a high level of his skill set to deploy ransomware, and there’s a large number of organizations that are still truly vulnerable.”
Schulkin agreed and noted that “The movement towards individuals (people) is interesting. I kind of view those as catastrophic. If an adversary is going do something like that, that person isn’t going to be a low-value target, and that attack isn’t going to be a little one.”
Tips for Making a Risk-based Decision:
eGroup | Enabling Technologies has a set of services that can help organizations prepare for, react to, and remediate cyber insurance and technical initiatives, including MSSP and professional cybersecurity services. Contact our team of award-winning experts today to get started on your MSSP journey or check out our website to learn more about how we can manage your environment from end to end.

CTO & VP of Strategy - eGroup | Enabling Technologies
Interested in learning how to ensure first responders arrive quickly when making an emergency call?
Contact our team of experts to start utilizing a Managed Security Service Provider or professional cybersecurity services today!