Zero Trust has evolved, and so should your security strategy. With the latest updates in Microsoft security solutions, organizations can streamline access, enhance compliance, and eliminate security gaps. Discover the 2025 Zero Trust maturity model and the key technologies driving the shift to a modern security framework.
See: Table of Contents
The Journey to Zero Trust
The Zero Trust concept has been around for a while now, and the rise of remote work during the COVID-19 pandemic supercharged the Zero Trust conversation. Many organizations had to scramble to enable employees to work remotely but did not have technology environments prepared for it. As a result, IT teams quickly implemented a mix of VPN, BYOD, VDI, and other solutions to keep people productive.
Now, in 2025, there is a growing need to streamline and secure these environments while retaining the advantages of flexible, remote access. Zero Trust provides a framework to accomplish this efficiently, but achieving it can feel intimidating.
The Zero Trust Maturity Model
Today, I want to introduce an updated Zero Trust maturity model, which outlines both:
- What the framework includes
- The Microsoft security solutions that address key requirements
This model helps organizations map out their current security posture and identify the next steps to move from Traditional to Advanced or Optimal Zero Trust configurations. Many organizations will have elements spread across multiple stages as they progress.
The most critical aspect of Zero Trust is intentionality—it should be a strategic goal embedded into your technology roadmap. Once an organization adopts Zero Trust principles, every future application and system decision should align with the framework, often leveraging the same tools and approaches outlined in this model.
Updated Microsoft Zero Trust Maturity Model (2025 Edition)
Organizations should evaluate how they are securing each key element (Identities, Devices, Network, Data, etc.) and place their current security technologies and controls in the appropriate stage of the model.
The following updated Zero Trust Maturity Model outlines the key security pillars and how Microsoft solutions map to each stage of the journey.
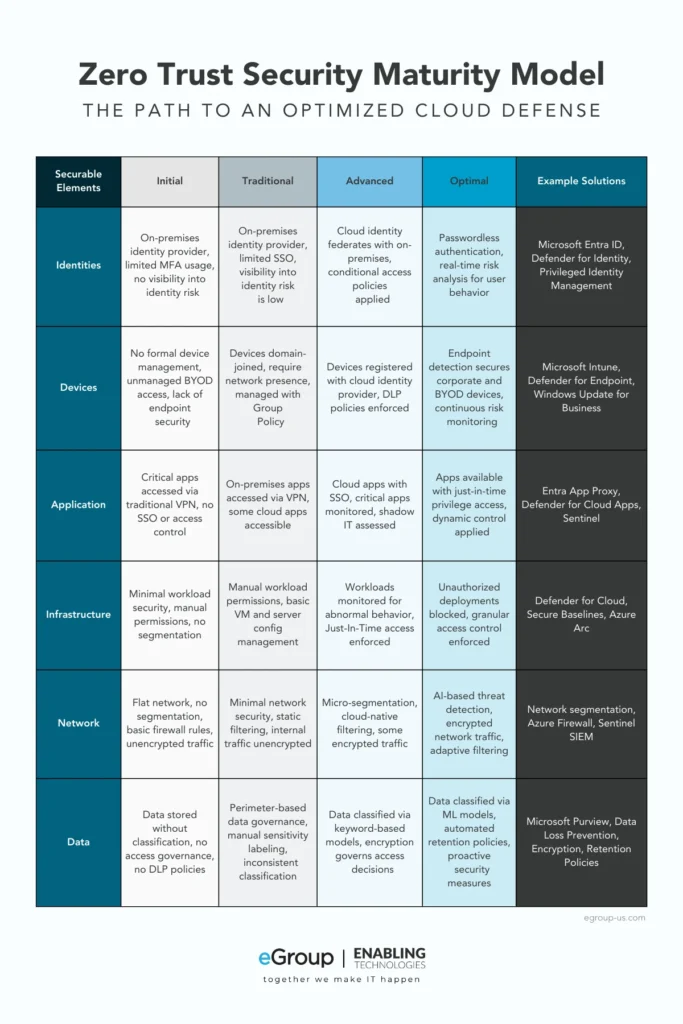
By identifying where your organization currently stands in this model, you can strategically plan the necessary steps to progress toward a fully optimized Zero Trust architecture. If you need help assessing your security posture, our team can guide you through the transition.
Key Microsoft Security Solutions for Zero Trust (Updated for 2025)
| Zero Trust Pillar | Microsoft Security Solutions (Updated) |
|---|---|
| Identities | Microsoft Entra ID (formerly Azure AD) for Identity Protection, Conditional Access |
| Devices | Microsoft Defender for Endpoint with Threat Intelligence and Attack Surface Reduction |
| Network | Azure Networking: Virtual Networks, Network & App Security Groups, Azure Firewall |
| Data | Microsoft Purview for Information Protection (DLP, encryption, compliance) |
| Applications | Microsoft Defender for Cloud Apps (CASB for SaaS and Shadow IT protection) |
| Threat Detection & Response | Microsoft Defender XDR (formerly Microsoft 365 Defender), Sentinel SIEM & SOAR for automated detection & response |
Key Updates from 2025
- Microsoft Entra ID (formerly Azure AD) is now the official name for identity management.
- Microsoft 365 Defender replaces Microsoft Threat Protection, covering Defender for Office 365, Endpoint, Identity, and Cloud Apps.
- Microsoft Defender for Cloud Apps remains the key CASB solution for securing SaaS environments.
- Microsoft Purview now includes expanded Information Protection capabilities, enhancing data security and compliance.
- Sentinel SIEM & SOAR continue to be essential for centralized security monitoring and automated threat response.
Reaching Your Zero Trust Destination
If an organization has controls fully deployed as described in the blue column (Optimal Stage), they have achieved a complete Zero Trust model.
A few important points to note:
- While the model includes traditional security controls (like Microsoft Defender products, SIEM, SOAR, and MFA), compliance solutions in Microsoft Purview (data labeling, encryption, and DLP) are equally crucial. These extend Zero Trust principles beyond network security into data protection and governance.
- The Zero Trust model heavily aligns with Microsoft’s E5 licensing, which includes advanced automation and security features. Many organizations struggle to fully implement Zero Trust without these tools.
- Azure Networking solutions, including micro-segmentation with Azure Firewall, Virtual Networks, and Application Security Groups, play a critical role in enforcing network-level Zero Trust.
- Azure AD Application Proxy (now part of Microsoft Entra ID) helps secure legacy applications that lack native support for SSO or MFA.
- Sentinel SIEM & SOAR centralize security event aggregation, allowing for faster incident detection and response automation.
- Zero Trust cannot be achieved with identity protection alone—device security is just as crucial. Microsoft Defender for Endpoint helps ensure all devices comply with security policies before gaining access. Check out our Enabled Endpoint and Endpoint Security offers.
Final Thoughts
Given the depth and interaction of these solutions, it is clear that Zero Trust is not a one-time deployment—it is an ongoing security strategy. Organizations must actively work toward it by:
- Assessing their current security posture
- Deploying Microsoft Zero Trust tools strategically
- Making security a core part of IT and business decisions
Once your organization achieves a Zero Trust framework, securing future applications and data becomes much easier, as new systems can be integrated seamlessly into your existing security architecture.
By keeping Zero Trust at the core of your IT strategy, you can future-proof your security posture while ensuring flexibility and efficiency for your workforce—no matter where they work.
Key Takeaways & Next Steps
| Action Item | Why It Matters |
|---|---|
| Update identity security with Microsoft Entra ID | Ensures strong authentication and adaptive access control |
| Deploy Microsoft Defender XDR | Provides holistic threat detection & automated response |
| Implement Microsoft Purview | Secures data through encryption, DLP, and compliance tools |
| Adopt Zero Trust for networking with Azure Firewall & micro-segmentation | Reduces attack surfaces and prevents lateral movement |
| Leverage SIEM/SOAR (Sentinel) | Automates security operations and enhances visibility |
| Educate teams on Zero Trust principles | Drives long-term security adoption & compliance |
By implementing these steps, your organization can accelerate its Zero Trust journey and ensure security at every level.
Need help? Contact us to discuss how we can help implement Zero Trust strategies tailored to your business.



