You run IT for your organization. You have a small team, maybe not in management’s eyes, but certainly in yours. It’s you, an infrastructure specialist, somebody managing the network, and another body managing your Office 365 tenant. You find that you are just keeping up with moves, changes, and deletes on O365, keeping Teams in order, dealing with user complaints around calling and meetings, replacing devices, keeping your domain-joined devices in order and up to date, managing backups, providing your user community with tips and tricks on new features, some application support, managing content on network file shares, supporting the migration of content into SharePoint online. Whew! You are stretched thin, but you’re keeping up. What keeps you up at night, though, is security.
It seems that every day there is another breach – the Colonial Pipeline shut down, for example. $5 million in ransom to restore operations. Every day one of your staff members might be clicking on that email link that could bring you down. Departing staff could be emptying out the crown jewels to a flash drive before they walk out the door. Customer data scattered throughout your tenant and suddenly compromised. Who’s fault? Maybe not necessarily yours, but you have exactly one guess whom the organization is going to come to for an explanation when that day dawns in your tenant.
You know you are responsible for securing content and access to that content across the tenant, but you are already stretched so thin. Who has the time to read up on Microsoft’s latest advancements with Security and Compliance. It’s clear that getting smart about these tools is going to require a major investment of your time or the time of someone else on your team. You may need to bring in consultants to show you the way, and they’re not free. Something has to give. There are literally only so many hours in a day, and the problems you are facing each day are that day’s problems. How do you position yourself and your team so you can avoid what could be catastrophic damage to your organization’s financial and / or reputational status?
Where Are Your Priorities?
The answer for most folks is a change in priorities. When you’ve been running IT for a while, you get used to “keeping the lights on.” And so does the rest of the organization. Your CFO anticipates a budget that looks a lot like last year’s budget. Staffing is frozen at current levels. Now, if the organization was rolling out a new ERP, you’d see more resources become available: technical assistance, 3rd party software, temporary, maybe even new permanent positions. Why? Because the broader organization agreed this new ERP was necessary to help, the organization achieve its goals and objectives. Once the organization had a consensus on the need for that investment, the resources freed up. It became a priority. Your job is to convince the organization that, in the same way, security and compliance will help the organization achieve its goals and objectives, that it should be a priority.
While that blog explored how IT should align with the business strategy, in this case, your job is to get the business to align with yours. How? Communication is the starting point. Think of it as a campaign. You’ve got to convince the organization that securing your organization is worth the investment. You can probably quickly define the explicit costs (i.e., new software, technical assistance, classes, even new headcount), but what are the benefits to the organization? That’s what you have to convey to your audience. And what are those benefits? Avoidance. Avoidance of the compromise and the damage resulting from that compromise.
Your strategy then is to get your organization worried, even scared. It’s a typical messaging strategy for certain situations: get your audience scared and then reveal the solution. Everyone breathes a sigh of relief and, in a perfect world, you have the resources you need. So, what is to be done? Tell them a story.
First, tell them about content, about data. If your organization has spent any time on the O365 tenant, there is probably data of all kinds across that tenant. Your user community knows there is a lot of content there, but you can describe how large that population of content is and where it all resides. You should already know what kind of data is where in terms of sensitive content. Describe that data, where it is, who has access to it. Get them to understand how many places sensitive content might be found. If controls are lacking, call that out. Be clear, so they begin to understand the risks.
Describe the difficulties your organization faces in keeping up with that content. You have staff uploading new content, creating new content, content that has been shared with your organization by trusted business partners. Hundreds, maybe thousands of emails coming in and going out. Avenues for data loss, whether it’s via email, downloading to a flash drive, printing, sharing via OneDrive for Business or SharePoint. Be specific about those avenues. Convey those risks in real terms. Give examples of what that would look like. Maybe you have some situations that have already occurred. Remind your audience of what happened or what might have happened if things had taken a darker turn.
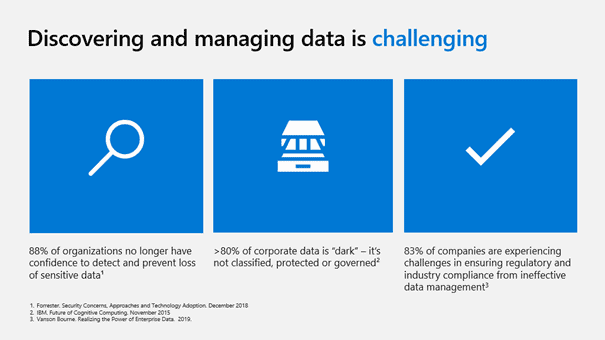
Hopefully, by now, your audience has a sense of the magnitude of the problem. The magnitude of that problem should also communicate that it is too large for you to manage with the resources you have. The implication is while you are aware of the problem and understand it. You simply don’t have the ability to solve it with the tools you have. But you’re not done yet. Next, you need to make this more than just IT’s a problem. You need to make it the organization’s problem. What are the risks of data loss or compromise? What’s the downside? Should it happen? What’s the worst possible outcome? This needs to be dramatic but not far-fetched. Your audience has seen enough news about breaches and the consequences to responsible organizations, so you shouldn’t have to try too hard. Real examples that could affect your organization are the way to go.
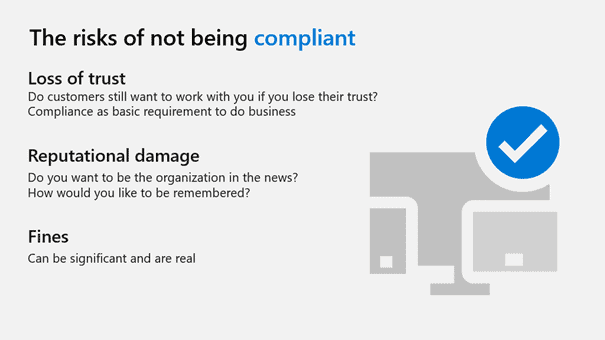
By now, they should have a sense of the magnitude of the problem and a new or refreshed sense of the challenges and risks the organization faces. Check for understanding. If they’re not there yet, return to risks with more examples of firms that have suffered damage. Paint a picture of scenarios that reflect your organization’s actual risk. What if this happened? What about that? When they understand the problem and the risks, describe the solutions.

You may already be licensed for relevant Microsoft solutions but just lack the bandwidth to apply them. Or perhaps you need to upgrade. But you probably still need the extra help, whether consulting, training, or additional headcount. Or all the above. Be specific about what you need to solve the organization’s problems. You can’t promise that these scenarios will never happen. We know there is no fool-proof level of protection. But you can say that with the steps you have outlined, you can minimize the risk and help to reduce the likelihood of the worst happening.
When you’re ready to take this on, contact our team of Cloud Computing Consultants. Not only can we help you with the implementation of solutions that will secure your tenant, our Strategic Advisory Services team can help craft your message to your management team. In fact, we’ve even delivered those messages to the C-suite.


