Microsoft Defender for Endpoint Service Adoption

Microsoft Defender for Endpoints (MDE) is an endpoint security platform feature designed to help customers prevent, detect, investigate, and respond to threats. Combined with Microsoft Defender on clients and a leader on Gartner Magic Quadrant, it provides a true enterprise grade solution to help proactively identify and stop threats as well as expedite reactive forensic investigations. Part of Microsoft Threat Protection, MDE seamlessly integrates with the entire Microsoft 365 ecosystem.
Chances are that you already have an existing endpoint protection solution deployed in your environment. The nice thing about Microsoft Defender and Microsoft Defender for Endpoints is that it can be deployed entirely side by side with your existing solution. This will allow you to evaluate the solution within your environment without creating vulnerabilities that you were not ready for. When ready, you can slowly transition endpoints fully over to Microsoft Defender for Endpoints without any gaps in protection.
Microsoft Defender for Endpoints provide a tremendous depth of capabilities to implement. However, the entire product is modular and can be deployed in phases. In fact, this is the preferred approach. Implementing everything at once is bound to cause issues and vulnerabilities. Take the layered approach with Defense in Depth. The following will provide insights to each Microsoft Defender for Endpoints module and the recommended implementation and adoption approach.
Service Adoption Order
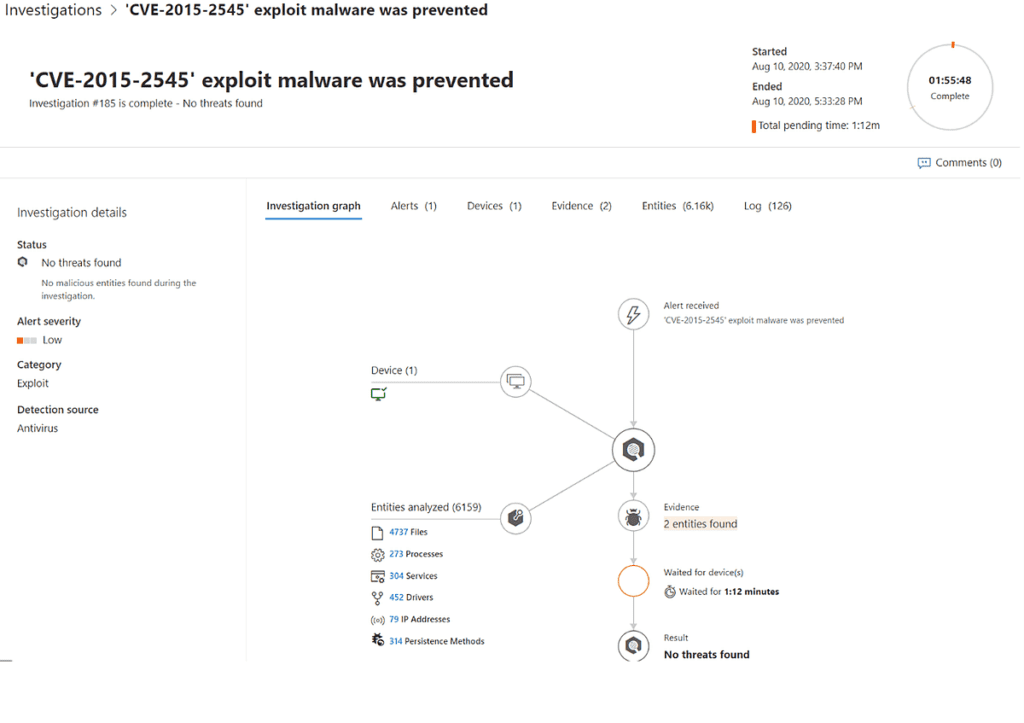
There are six primary modules to architect, plan, and implement for Microsoft Defender for Endpoints. The following list each one in the recommended implementation and adoption order. Following the list is a brief description of what each module provides.
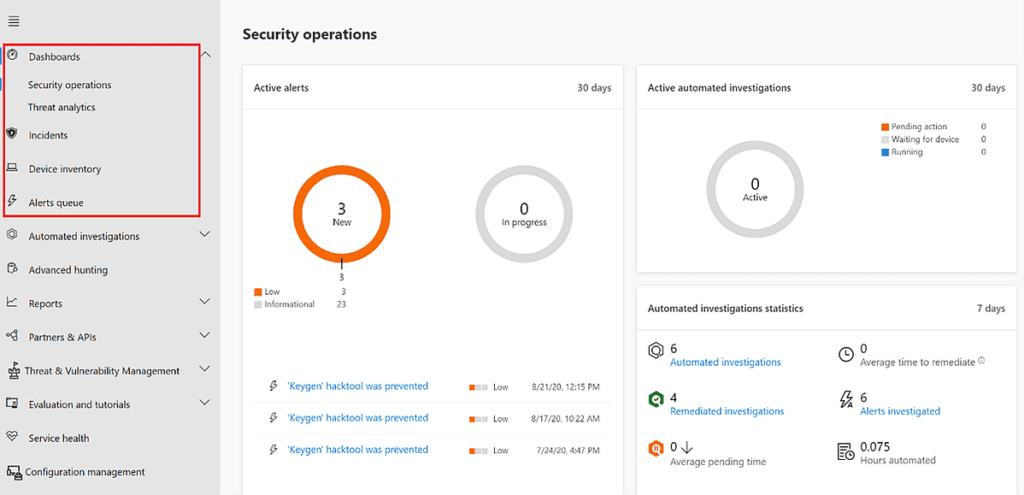
EDR should be the priority and focus when implementing Microsoft Defender for Endpoints. By merely onboarding devices to Microsoft Defender for Endpoints, you have already completed the minimum tasks to start using EDR capabilities. These capabilities help detect, investigate, and respond the threats that occur within your environment. EDR is designed to help fight back threats that get past the front door or first two pillars of the Zero Trust model, Identity and Devices.
EDR provides the following features:
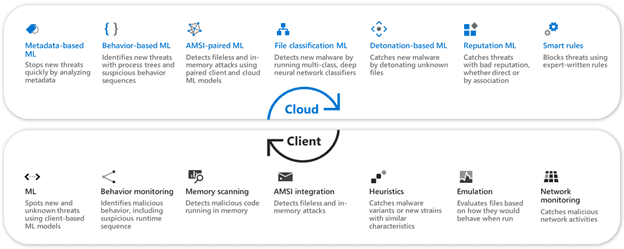
NGP is next in the list. Microsoft Defender is a built-in antivirus/antimalware solution for all Windows 10 devices as well as available for other platforms. NGP, formerly Microsoft Advanced Protection Service (MAPS), is what ties the standalone Microsoft Defender client to the cloud the deliver machine learning, behavior analytics, and real time big data analysis of all threats.
NGP provides the following features:
ASR should come after NGP. Once you have a core foundational operation plan with EDR and NGP, it is time to reduce the attack surface within your environment to lower your exposure. Attack surface consists of all the attack vectors an attacker can try to exploit to enter or extract data from an environment. Microsoft Defender for Endpoints ASR is an umbrella term for a wide range of features that can provide a specific layer of defense. These configuration settings help prevent exploit tactics and attacks on unprotected vectors. The following list shows all the features that are part of Microsoft Defender for Endpoints ASR.
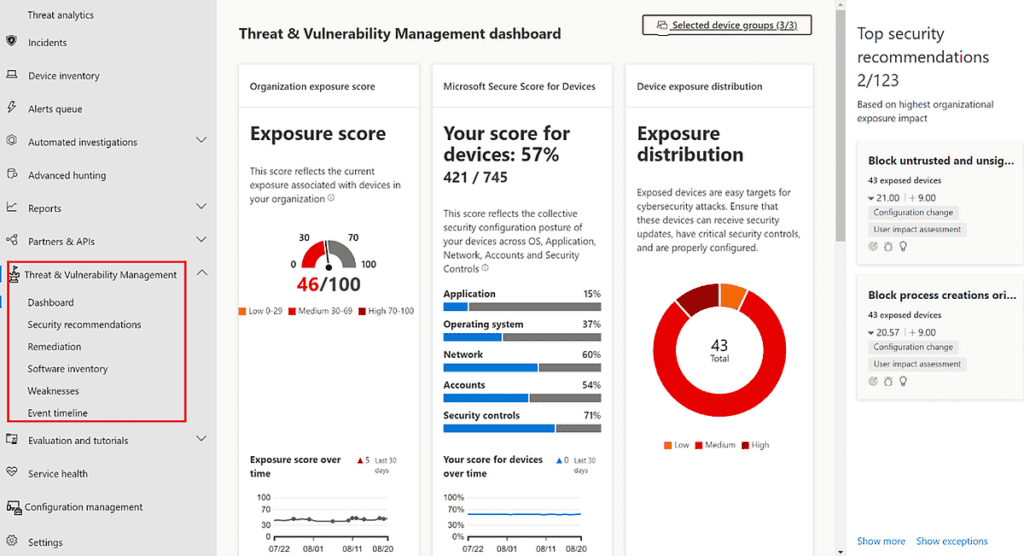
The last essential component is TVM. TVM provides a significant amount if insights into the current state of your endpoint environment. It helps quickly identify, assess, and remediate any endpoint weaknesses found. Exposure and Configuration Secure Scores can provide quick visibility of the overall security posture. The lower the exposure score and higher the configuration score means your environment is more resilient from threats and attacks.
Most of what TVM provides allows organizations to create a unique security operation plan for their endpoint security. I like to think that if you wake up in the morning and have no idea what could possibly be done to improve your endpoint security, visit the TVM dashboard. TVM provides the following features:
When alerts occur, depending on the type and impact, an investigation can be triggered automatically. AIR uses several assessment processes and playbooks to evaluate the alert and determine if remediation is required. AIR provides different levels of automation from selective based on folder type to fully automated remediation. This reduces the manual tasks involved with hunting and performing forensics on each event that occurs, allowing security analysts to focus on higher priority issues.
Implementing AIR falls into an optional, but highly recommended category. Needs and requirements from one organization to another can be completely different.
MTE is Microsoft’s managed threat hunting service. It is their way of providing its highly sophisticated resource team at your disposal to provide expert level monitoring and analysis quickly and accurately. MTE does come at an additional cost not included in Microsoft Defender for Endpoints licenses. You can sign up for a 90-day trial to evaluate its worth.
Because MTE is at an additional cost, the module is completely optional to deploy. However, many organizations do not have the appropriate staffing or budgeting to fully operate their own Security Operations Center (SOC). This service may allow for optimal efficiencies for the current staff available to mitigate threats.
While these six areas of Microsoft Defender for Endpoints make up most features and components of the solution, there are still many more features and components that require sufficient planning and preparation. Also, bear in mind, not all features need to be deployed to provide a secure environment. Security is always a fine balance. Implement too much and end user productivity suffers. So, make sure that the necessary amount of architecture, planning, and design takes place before any feature is deployed.
Work with our team of Cloud Computing Consultants with years of experience that know all of the “minefields” to prevent missteps.