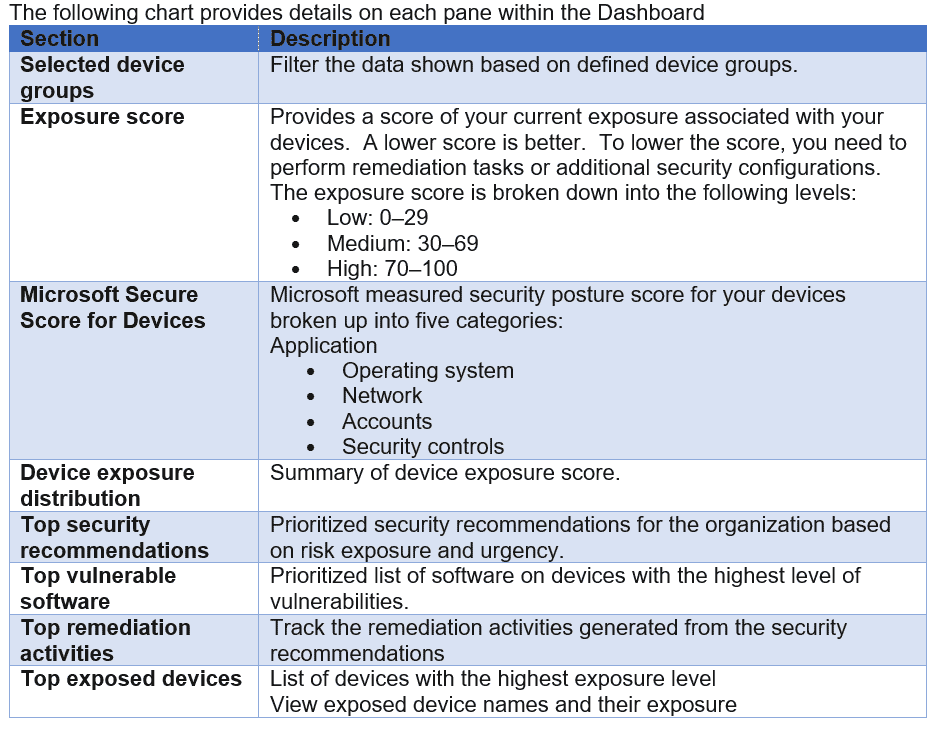
The Dashboard provides a high-level view of overall environmental insights regarding the active devices within the environment.
Microsoft Defender for Endpoints Threat & Vulnerability Management

Microsoft Defender for Endpoints Threat and Vulnerability Management (TVM) is one of my favorite MDE modules. It has constantly updated knowledge bases that are connected to Microsoft to provide insights and recommendations on the latest threats available. TVM is essentially assessing your environment at real time to provide details on what you should do. With TVM, you should never have to wake up and ask yourself what I should do to improve my security posture. If you are asking yourself that, you are not taking full advantage of MDE TVM, there is always something to remediate or improve.
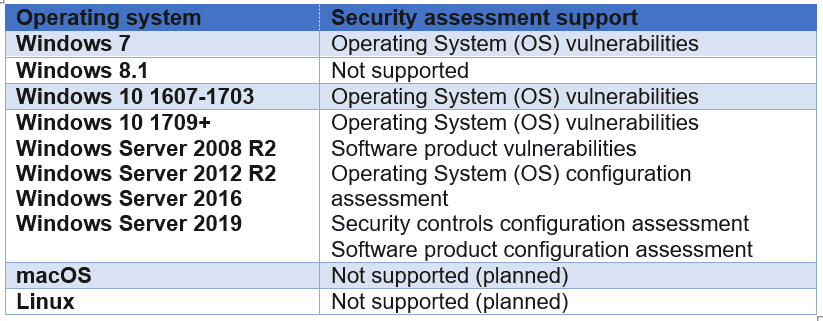
TVM Supported OS
MDE TVM only supports certain security assessments based in the Operating System connected to MDE. The following chart lists the current supported OS platforms for TVM assessments:
TVM Components
There are six primary components to MDE TVM. Each are listed below with complete details in the following sections:
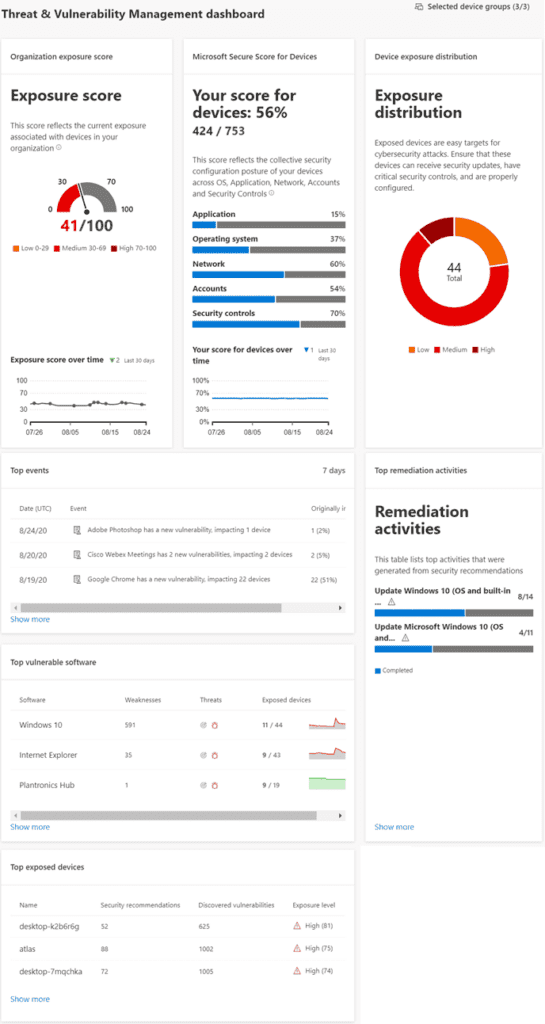
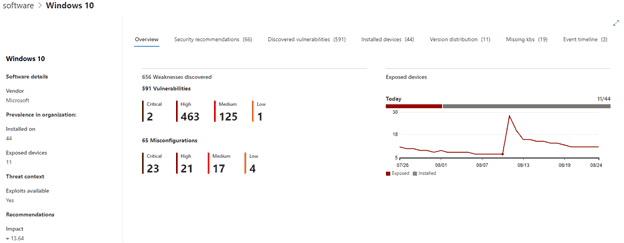
TVM Dashboard
The Dashboard provides a high-level view of overall environmental insights regarding the active devices within the environment.
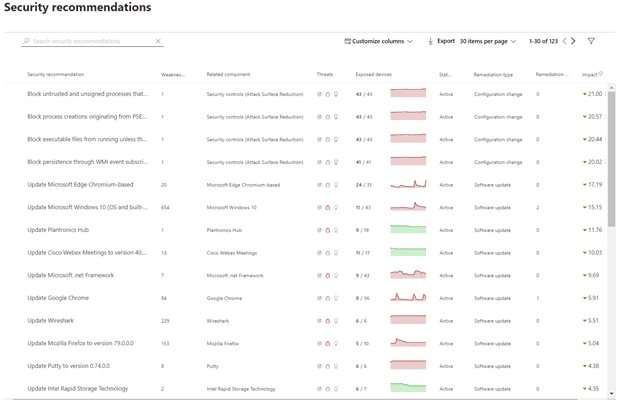
Recommendations
Weaknesses identified in your environment will show up and be mapped to an actionable list of recommendations. Security Recommendations provides a list of real-time actionable recommendations based on the devices in the environment. You can view the weakness score, threats and impact, related components, and other details from the list:
Threat options include:
If you select any of the recommendations, you are provided with greater details on the specific recommendations. You can take action directly from this pane including:
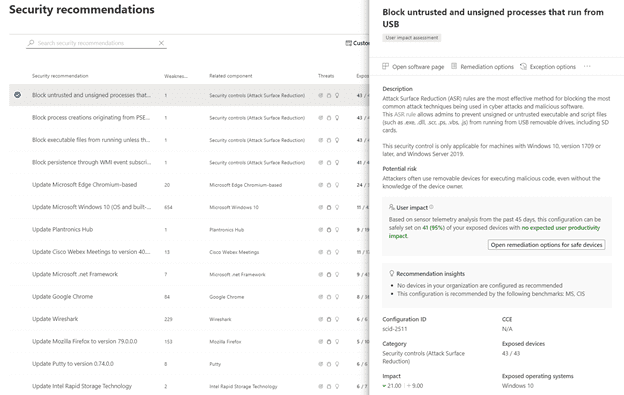
Another valuable use case for the Security Recommendations page is End of Support (EOS) Software. You can use the filters option and select any of the three current EOS options to see if your environment contains any recommendations for EOS software.
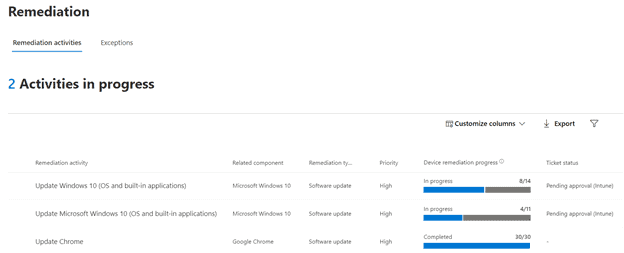
Remediation
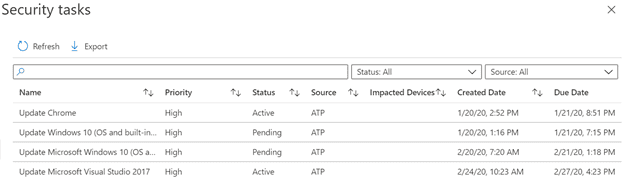
Remediation provides a place to keep track of requested actions or exceptions. This feature requires a connection to Microsoft Intune. You can keep track of progress for each task including description, due date, type, and status. Remediation activities are synced over to Microsoft Intune Security Tasks for your Intune administrator (if separate delegation exists in your environment) to perform the requested updates to the application.
Exceptions can also be created for security recommendations. There can be a variety of reasons to create an exception, just as accepted business risk, false positive, or 3rd party protection. Exceptions can be created with a limited time frame and can automatically expire and become a valid security recommendation once again.
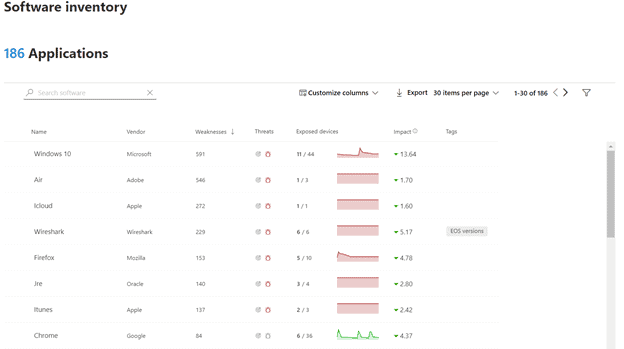
Software Inventory
Software Inventory is exactly what it says with added benefits. You can see an extensive list of all software installed on the devices in your environment. In addition to inventory statistics like how many devices have the software installed, each entry provides extensive details about current weaknesses, threats, updates, versioning, and security recommendations.
New applications are discovered in real-time along with their respective vulnerability information.
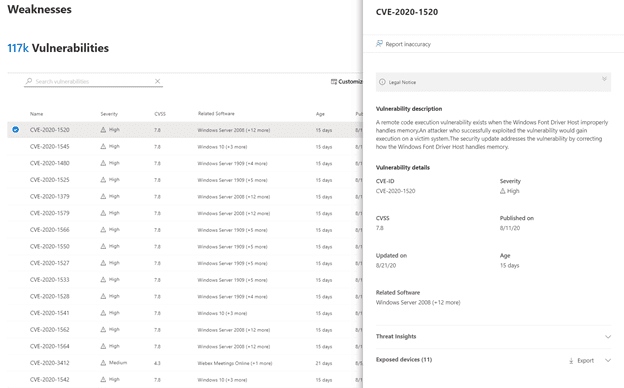
Weakness
Weaknesses keeps an extensive knowledge base of any Common Vulnerabilities and Exposures (CVE) found in software installed on your devices. As you can see from the screenshot below, there is quite an extensive list, all managed by MDE.
For each CVE, you can see the common vulnerability scoring system (CVSS) V3 score, vulnerability details, threat insights, and exposed devices.
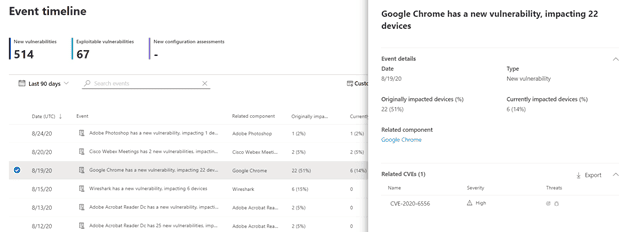
Event Timeline
Event Timeline is the latest addition to TVM. It is like a news feed only specifically focused on new risks that are associated with your environment. You can drill down into each event and see the details of the risk, related CVEs, and devices that are impacted. With the Event timeline, you can stay abreast to ever evolving changes and keep up to date with security vulnerabilities affecting your environment.
MDE TVM is a one stop shop to monitoring your device vulnerabilities and keeping track of activities that should be performed in your environment. You should always have insights and information on what needs done to keep up with old and new threats in the world.
For each CVE, you can see the common vulnerability scoring system (CVSS) V3 score, vulnerability details, threat insights, and exposed devices.
Contact our team of experts who have years of experience and know all of the “minefields” to prevent missteps.