Purview Data Loss Prevention:
The First Step to Data Governance
As I discussed in my previous blog, data governance is top of mind in most organizations, as it probably is in yours too. Today I am going to continue covering Purview features that can help you get started with data governance. In this installment: Data Loss Prevention!
As I mentioned last time, your organization is almost certainly covered by a state or national regulation that requires you to disclose a data breach of personally identifiable information like social security numbers, credit card numbers, bank account information, or medical data. If your organization has a payroll or a Human Resources team, then it is almost certain that this kind of data lives in your environment somewhere. Again, data governance isn’t just for banks or government agencies anymore.
Data Loss Prevention (DLP) is often the gateway to data governance. It is the easiest feature to start using and make effective in a short period of time, even if you have not configured other Purview features. Further, the out-of-the-box data types and policies are easy to use, and comprehensive, so you are able to get started quickly.
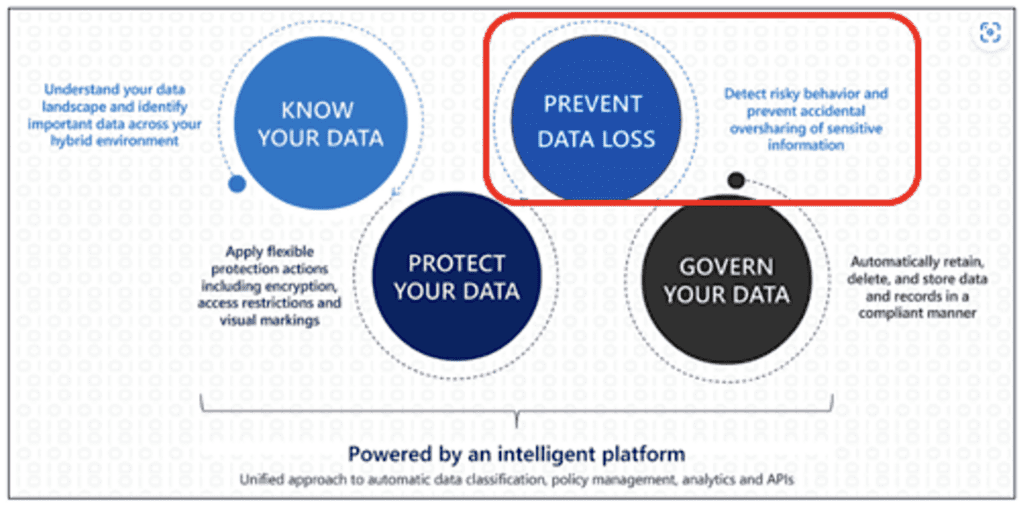
I introduced one of Microsoft’s Purview diagrams below last month, and I will refer to it again now for reference. You may recall last time I highlighted “Know Your Data”. Today, let’s talk about “Prevent Data Loss”. (For now, I skipped over Protect Your Data since you can set up some features of DLP without labeling files. Again, the goal is to get some protection working quickly with default settings.)
Purview Templates
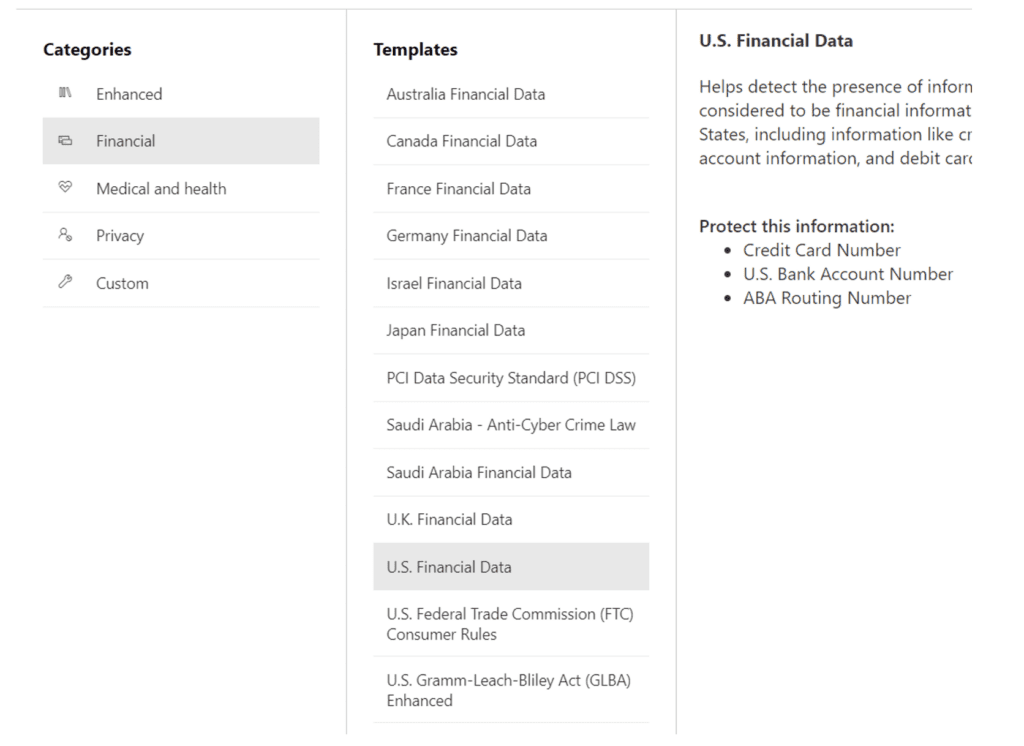
Purview DLP comes with pre-defined templates of sensitive data types that are designed to detect the common confidential data types listed above. These templates correspond with regulations like HIPAA, PCI, or the Patriot Act. The one that I find useful in many general scenarios is called “U.S. Financial Data” and includes the following data types:
These data types cover several of the common data elements that any organization would need to protect from unauthorized disclosure. Many more specialized templates are available for financial services, healthcare, or other privacy regulations, so look through the available templates to see which ones best suit your needs. The process to set up any of the templates is similar to what I show below.
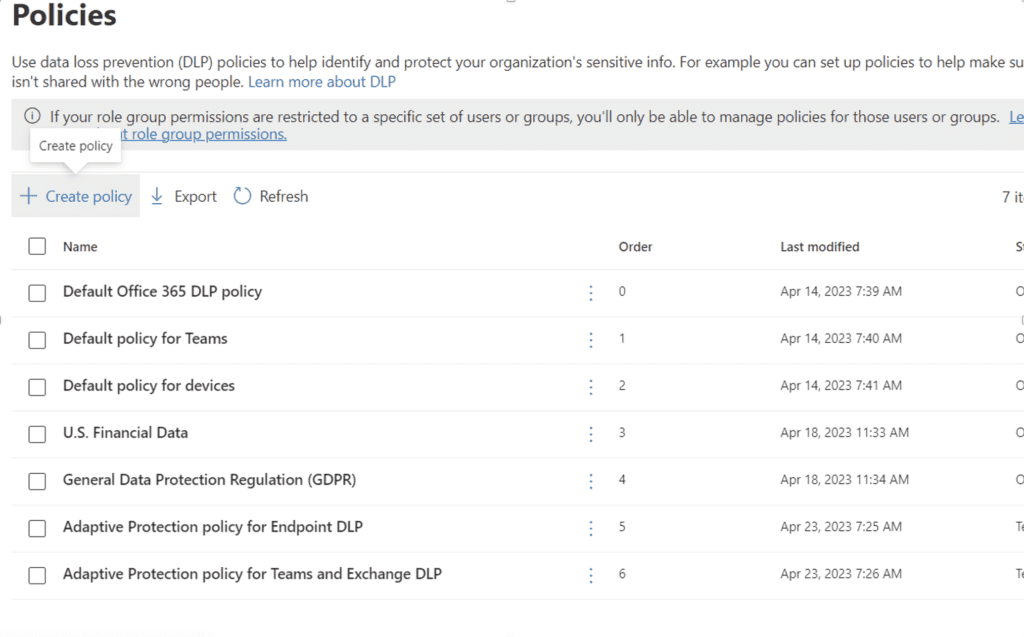
Set Up a Test Policy
First, go to the Policies submenu under Data Loss Prevention form the Purview Admin Console and select Create Policy:
Then, select the U.S. Financial Data template:
Next, name the policy (or stick with the default):
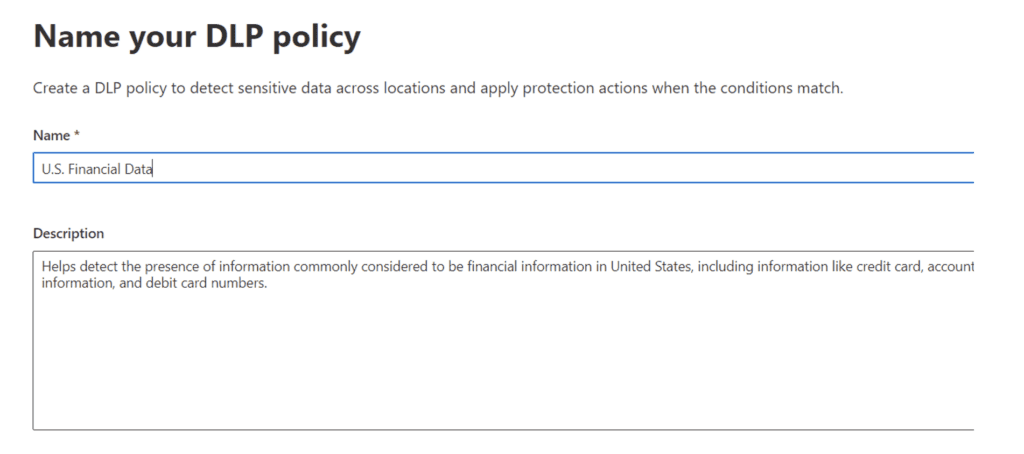
Choose the locations to apply the policy to: I chose Exchange, SharePoint, and OneDrive to start.
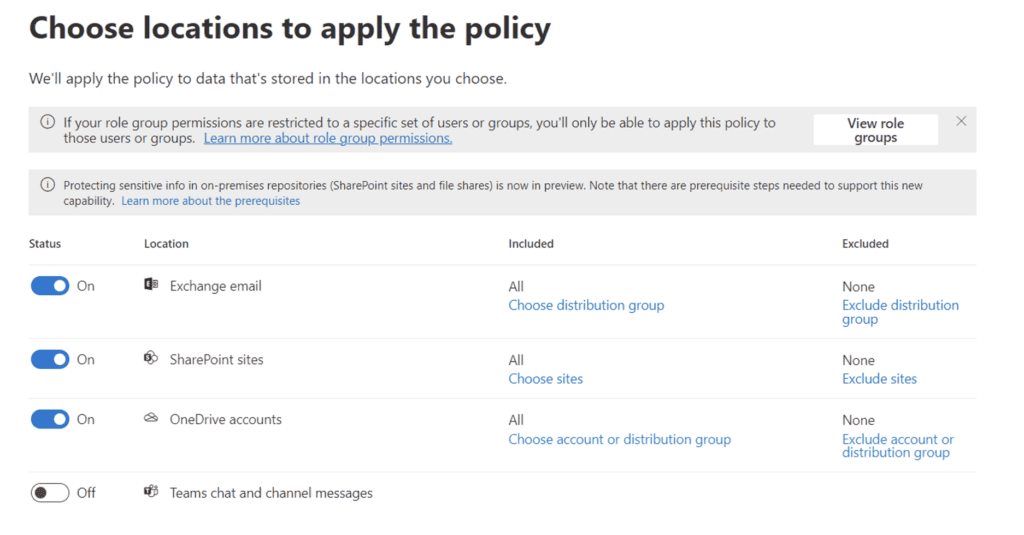
Only external sharing is monitored in this example:
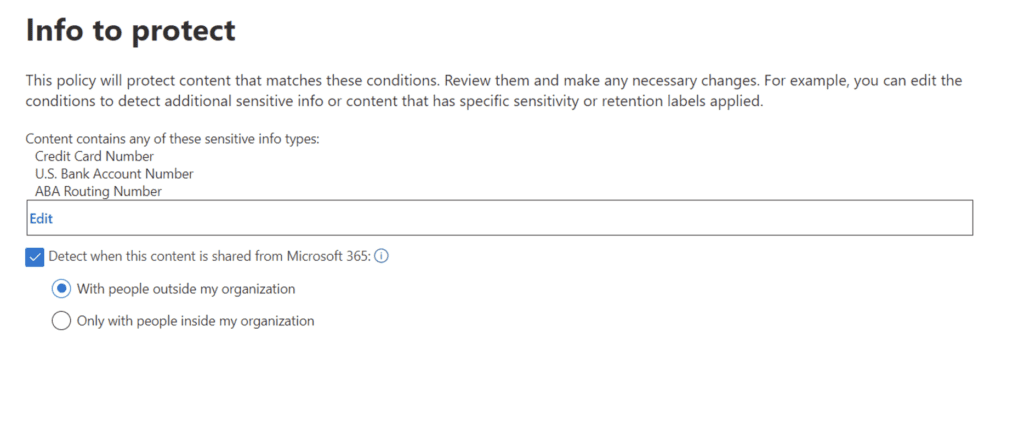
Select what actions should occur if sensitive data is detected:
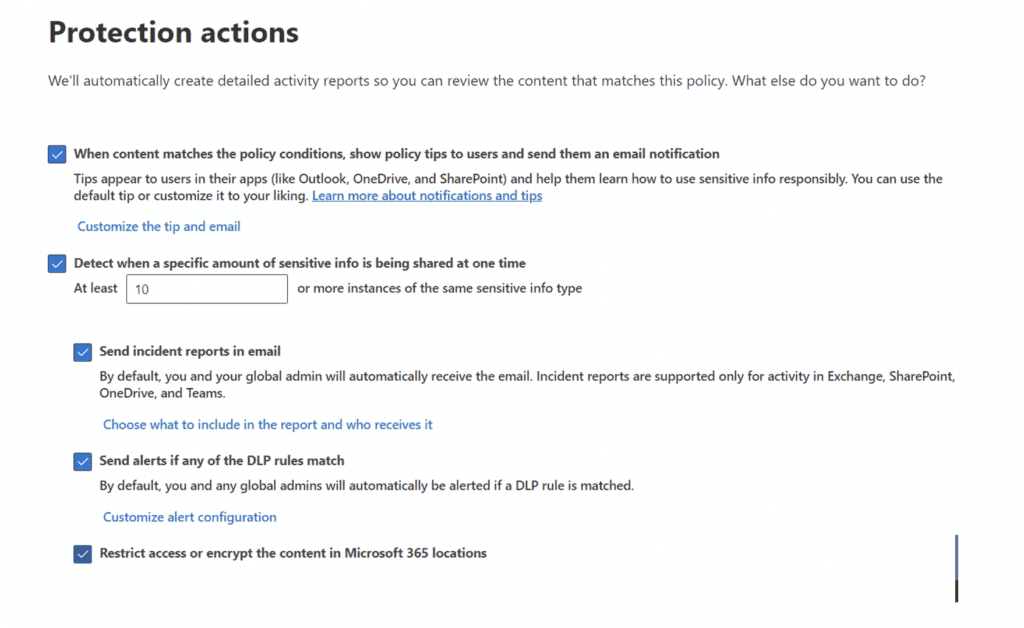
And then decide if you want to block access or allow the user to override:
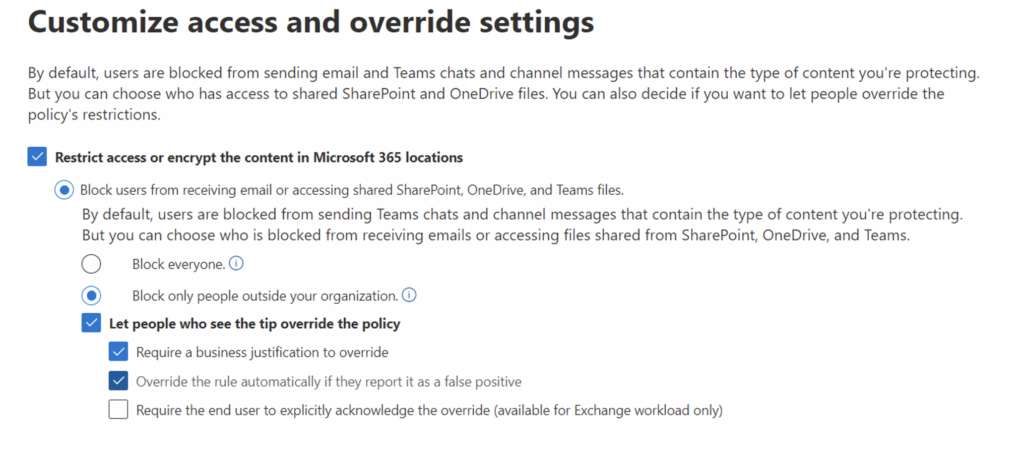
IMPORTANT! First, you should only test this policy so that no users are impacted. Make sure to select the “Test it out first” option and uncheck Show Policy Tips:
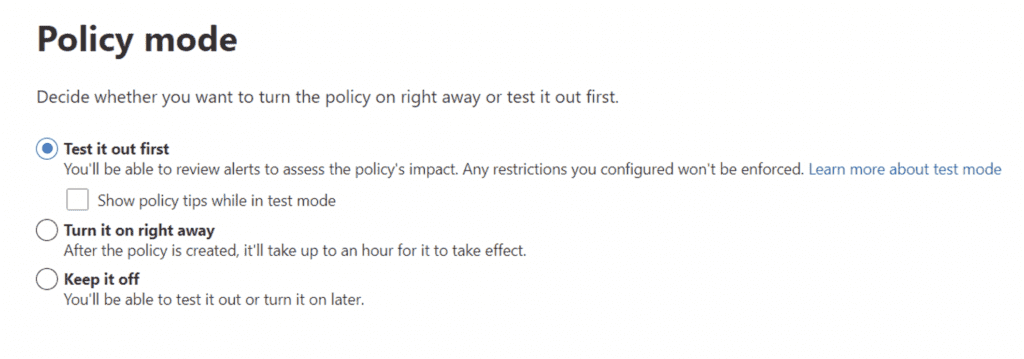
Check the Results
Wait a few days and check the Activity Explorer submenu in the Data Loss Prevention tab on the Purview Admin Console. You can look at the log to see how many times someone has shared data outside the organization.
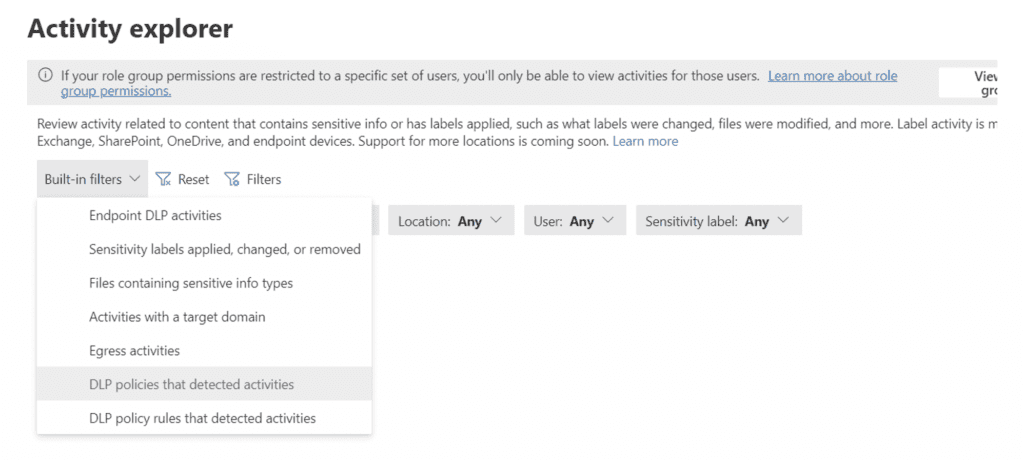
This should give you an idea of how much external sharing or emailing of those types of confidential data is occurring in the organization. Just remember, it is likely that some of the log entries might be the result of false positives or legitimate activities, such as the accounting department sending out an invoice with payment instructions on it.
You can edit and tune the policy in many ways, such as excluding certain groups, or setting thresholds so that only sharing of a large amount of data causes an alert. Once you have tuned the policy and no longer see any false positives, you can turn on the policy and it will start blocking unauthorized sharing of sensitive data.
**Make sure you communicate this change early and often to the employees affected.**
Doing More with DLP
I hope that this demonstrates the power and relative ease to getting started with Purview Data Loss Prevention. It does not take a lot of time to set up some robust policies that will start keeping sensitive data from leaking outside of your environment. There are many more ways to apply DLP to data inside and outside of the organization. Other Purview features like sensitivity labels, custom content types, and override policies can be used by DLP to build very complex and specific rules governing your data.
This was a simple example to demonstrate a way that many organizations get started with DLP. A true data governance strategy needs to not only include DLP, but also sensitive data labeling, data retention policies, custom sensitive data types, and much more.
If you want to learn more, my colleagues and I help clients with Purview and data governance planning, design, and governance programs all the time. Please complete the form below to further discuss how we can assist your organization!

Strategic Advisor - eGroup | Enabling Technologies
Ready to prevent data loss and protect your data with Microsoft Purview?
Contact our team of experts to get started!