Securing What Really Matters


Chris Stegh
CTO and VP of Strategy
The Problem is the Perp, Not the Victim
When a hospital is victimized by ransomware, patients whose care is disrupted due to postponed or relocated appointments have a right to be angry. When the prices of gas or meat spike because of a cyber incident, consumers are right to demand action. When a government agency or school system loses the data of its citizens or students, they’re justified in asking, “Why!?” (If they’re polite in their choice of words.)
These incidents are not only illegal, but also immoral, and unjust. They’re initiated by nation-states, their proxies, or criminals who attack from all corners of the globe. Occasionally, they target specific victims, but mostly, adversaries indiscriminately search and attack any vulnerable victim.
It’s like planting a garden to feed a community in need, only to have someone constantly uproot the seeds before they can grow. Imagine that in the physical world—no one would stand for it! We shouldn’t stand for it in the cyberwar arena, either.
Step One: Hire Motivated People
Some of us are so irked that we direct our energy for 50+ hours a week to cybersecurity. Dedicated cyber pros won’t stand by while innocent people are affected. Protecting and hunting valuable systems and the people that count on them is why we do what we do.
At eGroup Enabling Technologies, we believe in taking a proactive approach to protecting, detecting, and responding to incidents for our customers, and this article shares some of those practices.
Step Two: Be Clear About Responsibilities
In organizations with large security teams, the concept of a RACI chart is needed. Often, different priorities and unclear roles between CISO organizations and IT operations slow the time to respond to new threats or implement new protections. This excerpt of the RACI chart below shows the groups involved, and which groups are Responsible, Accountable, Consulted, and Informed for the planning and the decision-making of the security lifecycle. Additional pages cover implementation, monitoring, red team exercises, and the like.
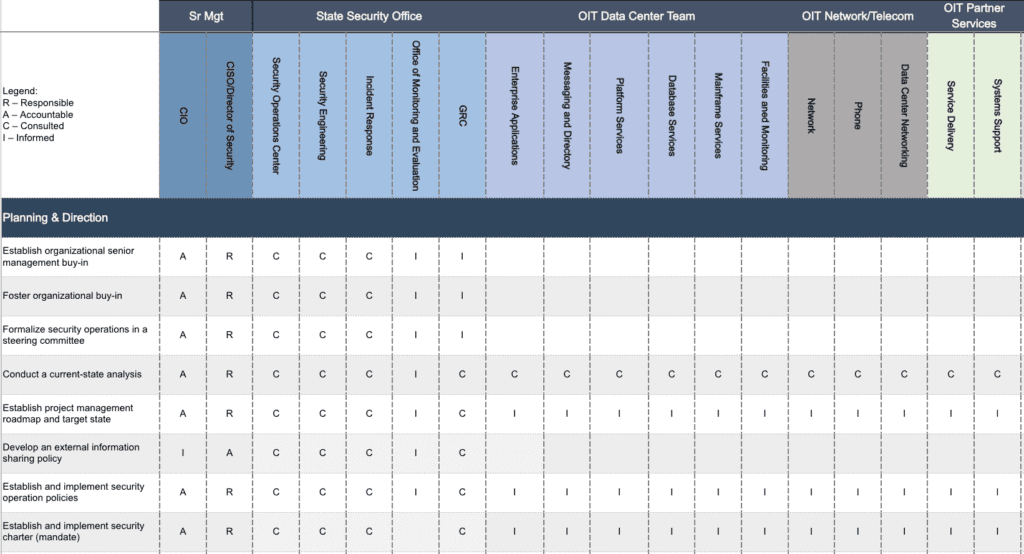
For smaller security teams, especially where security and IT are managed by the same people, internal RACIs are less necessary. Clearly, those teams need more external assistance to manage and hunt for threats.
Gartner Group predicts that by 2026, 60% of organizations will employ the services of a Managed Security Service Provider, up from 30% today. Gartner recommends that organizations with less than 8 full-time personnel seek out co-managed security services (from “Market Guide for Co-Managed Security Monitoring Services”).
Chances are, if you’re reading this, you are either proactively or reactively exploring such services. Gartner and others are coining the term, “Co-Managed Security Services,” where a partner, “Provides remote maintenance and monitoring of client-owned threat detection, investigation, and response capable products.”
eGroup Enabling Technologies takes a co-managed approach, yielding architectures that resemble the following:
Clients own and co-manage the devices, software, and systems in the left-hand side, and when contracting for ThreatHunter services, benefit from the added layer of proactive monitoring added in green. This architecture is specified as the way all Microsoft Intelligent Security Association members and Microsoft Verified Managed eXtended Detection and Response partners must connect to clients.
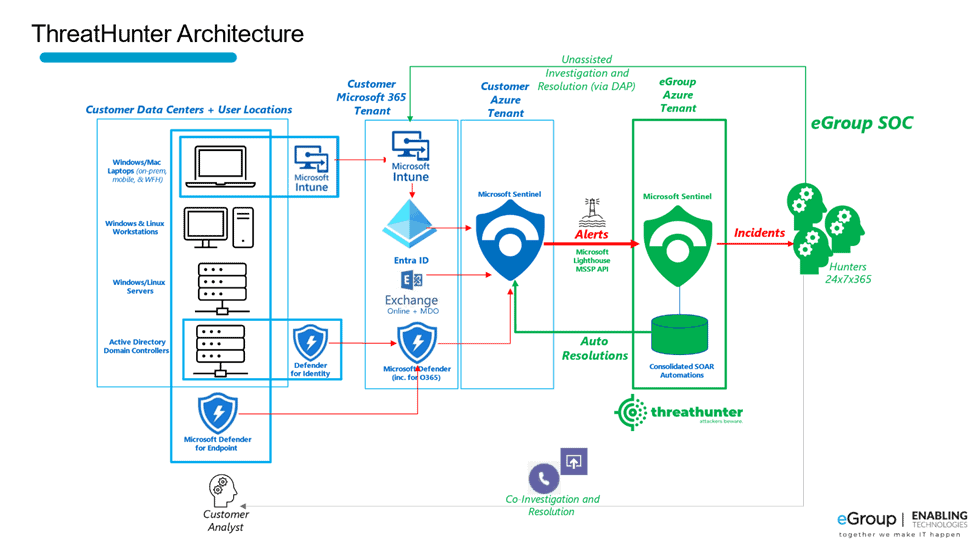
Customers have responded positively. Marcus Ienaro from NYC law firm, Herrick said, “Oftentimes, Managed Security Providers require you to put in their own technology. That was one of those things we’re trying to avoid, not just from a cost perspective, but also from an integration perspective. We had the license and the tool set, we just needed someone to monitor alerts. That’s when we turned to eGroup Enabling Technologies.”
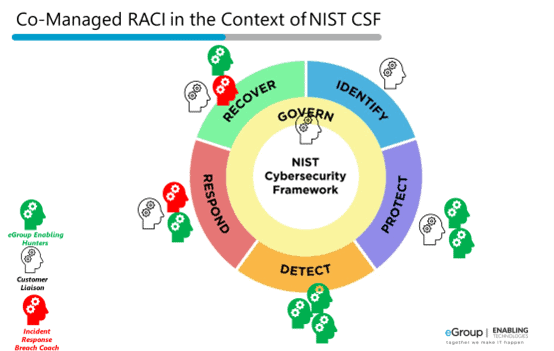
While internal RACIs are less necessary for small IT and security teams, having a RACI with service providers is critical. In co-managed environments, eGroup Enabling Technologies generally works with customers in the construct outlined below. The outer nomenclature refers to the functions within NIST 800-61, Cybersecurity Framework. If you’re unfamiliar with the NIST Cybersecurity Framework, click here to download our eGuide.
Step Three: Get Proactive
Regardless of either self-managing or co-managing the security environment, frequent updates are required for two primary reasons:
- New threat vectors emerge. Our team monitors for Indicators of Compromise (IoCs) using various real-time industry databases.
- Microsoft has added a new capability to their toolset. These new capabilities often address trends or recurring issues (i.e., Adversary in the Middle Attacks). You can see the velocity of Microsoft security changes in our monthly newsletter.
In both cases, many SMBs don’t have the time to stay in front.
Some MSSPs simply configure agents and wait for the incidents to come in. ThreatHunters do that too, but to minimize the number of incidents that occur, the systems need to be periodically tuned for improvements. As result, our ThreatHunters regularly engage to:
- Block email domains that are the source of phishing campaigns.
- Build auto-remediation rules for commonly occurring threats (i.e., to block impossible travel attempts).
- Patch Operating Systems to address new CVEs (Common Vulnerabilities and Exposures).
- Scan all environments that we manage for new IoCs. Where a client is exposed, we alert then help them add protective measures.
- Identify users under persistent impersonation or password spray attacks and add configurations to abate the noise.
- Progress toward zero trust by reducing the surface area of the machines and tenants being monitored, turning off unused services, and allowing no more privileges than necessary.
Fighting Back Together
Whether alone or with a co-managed security partner, organizations must proactively make improvements to account for new threat vectors.
Executives with small security organizations know how challenging it can be to protect assets from the latest cyber threats. With limited resources, time, and expertise in the latest threats, it’s difficult to manage risk.
The CFO of new ThreatHunter customer Carolina Eastern stated, “We were not trying to get hacked. We thought we were doing fine, but we didn’t know. We were hacked, and it was a lot of pain. After partnering with eGroup Enabling Technologies, our outlook now is ‘We are trying not to get hacked.’”
Together we can raise the cost of criminal activity and cease cyberattacks from harming innocent patients, consumers, and citizens from malicious, unfounded, and illegal attacks.
We Can Help!
Does your organization lack the time and bandwidth or specialized skills to deploy and keep security systems updated? We can help! If you have questions or would like some guidance on cybersecurity, please reach out to info@eGroup-us.com or complete the form below.
Looking for Guidance or Assistance with Cybersecurity?
Contact our team today to learn how we can help.

