This is the second article in this series. In the first part, we discussed the need to properly configure your Intune settings and policies for Teams Android devices. Here we will go over a few more items related to settings in Intune. We will also go over configuring Conditional Access Policies for these devices. Finally, we will talk about Teams Configuration profiles and testing your devices.
Detailed Configuration Steps (Continued)
Check the Intune and Azure Active Directory Device Limits
- Three objects are created when a new Teams Phone is enrolled in Intune:
- Intune Device Object
- Azure Active Directory Device Object
- Teams Device Object
- Intune and Azure Active Directory have definable limits on the number of device objects that can be associated with a user account.
- Microsoft recommends that the device limit for Intune Device Objects should match or be greater than the limit for Azure Active Directory device objects.
- The recommended limit for Azure Active Directory device objects is 20. The maximum limit of Intune device objects is 15.
- Navigate to the “Azure Active Directory admin center,” portal.azure.com.
- Click on “Azure Active Directory.”
- Click on “Devices”
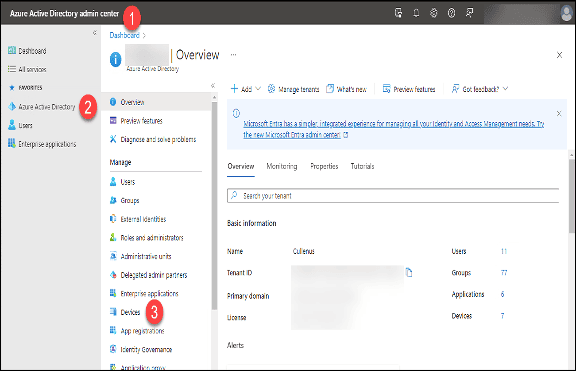
4. Click on “Device settings.”
5. Note the number of devices in the “Maximum number of devices per user.
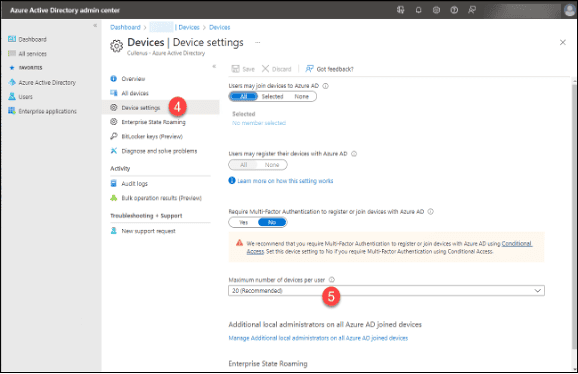
6. Switch back to the “Microsoft Endpoint Manager” and click on “Devices.”
7. Click on “Enroll devices.”
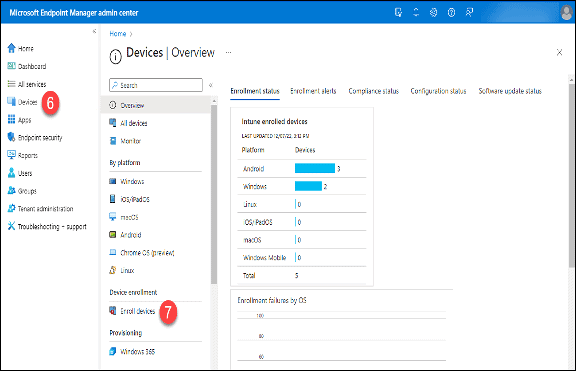
8. Click “Enrollment device limit restrictions.”
9. Click on the name of the Device Limit Restriction Policy.
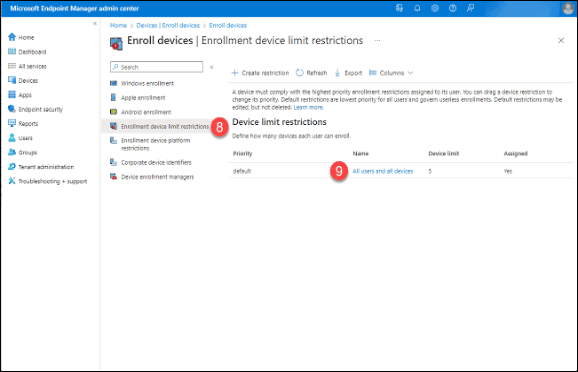
10. If the device limit is less than that of the Azure Active Directory devices, click on “Properties.”
11. Click the “Edit” button.
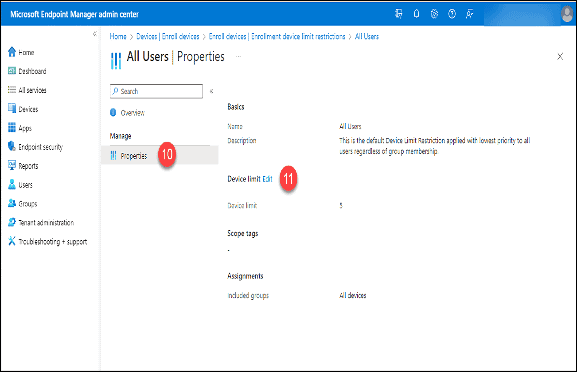
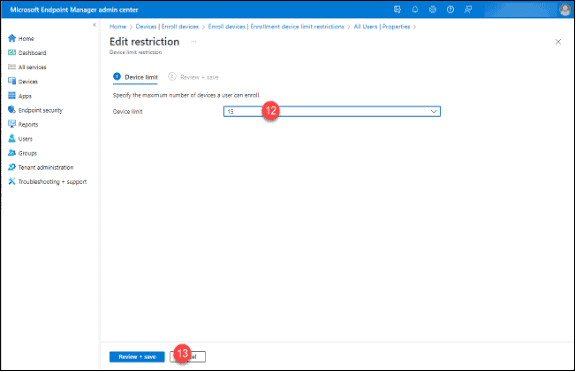
12. Change the value of the “Device limit” to something that matches or exceeds the Azure Active Directory device limit or the maximum, 15, whichever is greater.
13. Click the “Review + save” button.
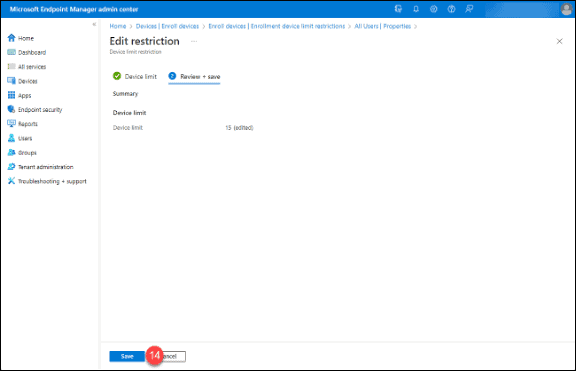
14. Click the “Save” button.
Exclude Android Device Administrator Devices from App Protection Policies for the Android Platform
- Apply these steps to all policies defined for the Android platform.
- In the Microsoft Endpoint Manager Admin Center, click on “Apps.”
- Click on “App Protection Policies” in the “Policy” section.
- Click on the first policy defined for the “Android” platform.
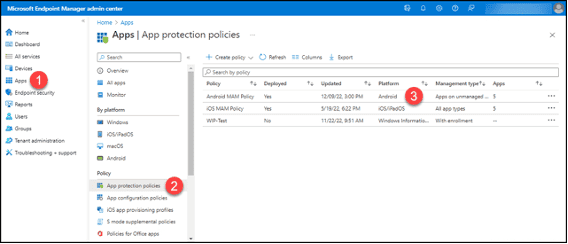
4. Click on “Properties.”
5. Click the “Edit” button for the “Apps” section.
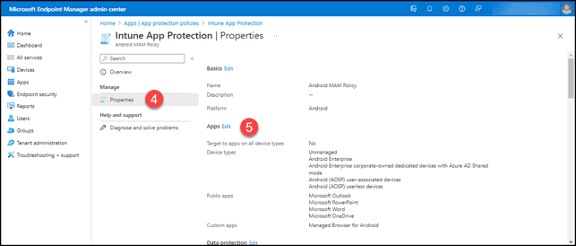
6. Set the “Target to apps on all device types” switch to “No.”
7. Click the “Device types” drop-down. Select all the types you want this policy to apply to except for “Android Device Administrator.”
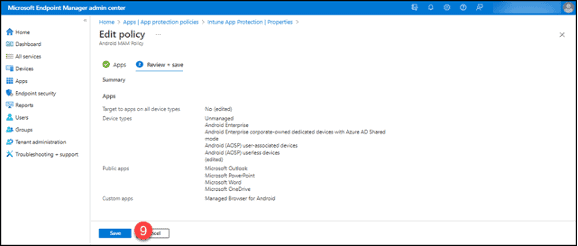
8. Click the “Review + save” button.
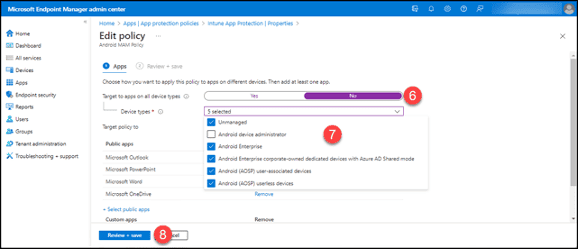
9. Click the “Save” button. Repeat for the rest of the policies written for the Android platform.
Add the Teams Phones Exclusion Query as a “Filter for Devices” Condition on Existing Conditional Access Policies including Terms of Use Policies that have Unsupported Teams Phones Settings
- There are many Conditional Access Policy settings that are incompatible with Teams Phones and other devices managed by the Android device manager. These are the Conditional Access Policy settings and their supportability on Teams Phones as of September 14, 2022:
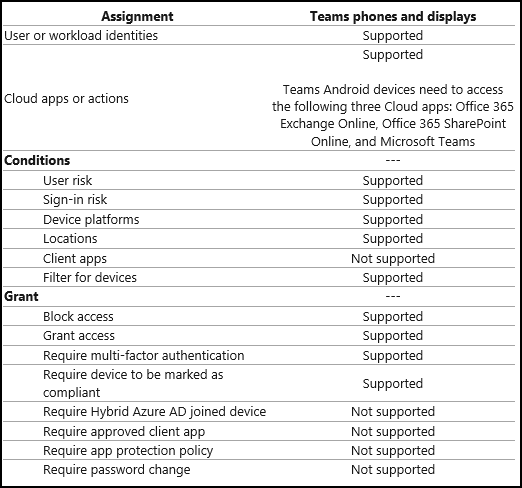
- Teams Phones only need to access the Microsoft Teams, Office 365 Exchange Online and Office 365 SharePoint Online “Cloud Apps.”
- If “Cloud Apps” is selected from the “Cloud apps or actions” setting and is not set to only include these apps, Teams Phones may not work with the Conditional Access Policy.
- According to Microsoft, you can also use “Office 365” as the selected application in a Teams Phone compatible policy.
- “Client apps,” under “Conditions,” and “Conditional Access App Control” under “Session” are also not supported.
- Conditional Access Policies that enforce a “Terms of use” can cause problems for Teams phones.
- While “Sign-in risk,” under “Conditions,” is supported, it can cause problems for Teams Phones. E-Group | Enabling Technologies recommends treating “Sign-in risk” as an unsupported condition for Teams Phones.
- If a sign-in is determined to be “high risk,” an authentication token will only be issued once then revoked when the user signs out.
- A user signs on to a Teams Phone in the office.
- The sign-in is flagged as “high risk” the authentication token is issued but will be revoked when the user signs off the phone.
- The user unplugs the phone to take it home.
- When the user plugs the phone in at home and signs on, the user will likely be prompted to sign back into the phone. This will cause a new Azure Active Directory device object for the phone to be created under the user’s account. This can cause problems with the user’s defined device limit.
- “Sign-in frequency” under the “Session” section in the Conditional Access policy is also supported. However, it can cause problems for Teams Phones. Once signed in a Teams phone will usually perform a periodic silent re-authentication to stay signed in.
- If a “Sign-in frequency” requirement is applied to a Teams Phone, the user will be signed out by the policy. The phone will need to be manually signed back in.
- This is a health and safety issue because emergency calls cannot be made from a signed-out phone.
- If a sign-in is determined to be “high risk,” an authentication token will only be issued once then revoked when the user signs out.
- Add an exclusion for your Teams Phones to each of your Conditional Access Policies that have at least one section with at least one incompatible setting:
- Contain one or more unsupported settings in the “Cloud apps or actions”, “Conditions” or “Grant” sections listed in the Supported Conditional Access and Intune device compliance policies for Microsoft Teams Rooms and Teams Android Devices The list can also be found in the previous “Implementation Notes” section.
- Have incompatible “Client apps or actions” settings.
- Compatible apps for Teams Phones are “Office 365” or the combination of Microsoft Teams, Office 365 Exchange Online and Office 365 SharePoint Online.
- An enabled “Use Conditional Access Apps Control” setting in the “Session” section of the policy.
- Enforce a “Terms of Use” in the “Grant” section.
- Have a “High Risk” level of “Sign-in risk” condition in the “Conditions” section.
- Use a “Sign-in frequency” setting in the “Session section.
- In the Microsoft Endpoint Manager Admin Center, click on “Devices.”
- Click on “Conditional Access.” ***Do not perform these steps from the “Conditional Access” link in the Azure Active Directory Admin Center. Some of the relevant settings will not “show up” from the Azure Active Directory link.
3. Click on the first policy in the list. (The policies used in the examples were created from the templates provided by Microsoft and are in “Report only” mode. The “Terms of Use” Policy was manually created.)
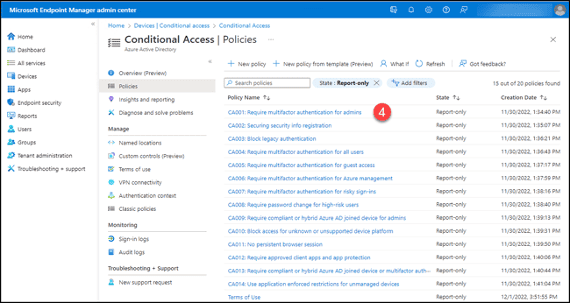
4. In the “Cloud apps or actions” section, if the value is “All cloud apps,” this section of the policy is not compatible with Teams Phones. The example policy, therefore, is not compatible with Teams Phones. You do not need to perform the additional checks for this policy.
- If the value is “1 app included” check to see if it is “Office 365.” If not, the policy is not compatible.
- If the value is “3 apps included”, make sure the apps are Microsoft Teams, Office 365 Exchange Online and Office 365 SharePoint Online. If not, the policy is incompatible.
- If the value is “4 apps included” (or more), the policy is probably not compatible.
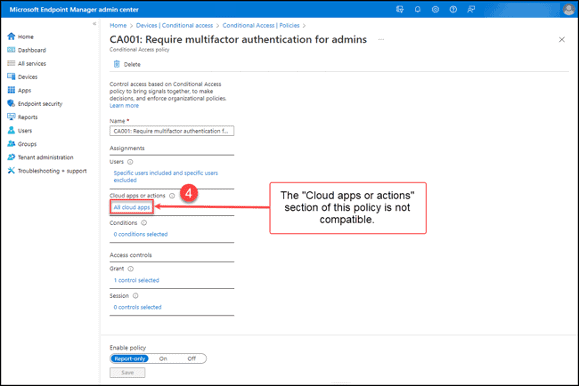
5. The “Conditions” section of the sample policy indicates that there are “0 conditions selected.” The settings in this section are compatible with Teams Phones. Continue checking the other sections of the policy:
- If “Client apps” are configured, the Conditional Access Policy is not compatible.
- A configured “Sign-In risk” for “High” risk sign-ins is supported, but the Conditional Access Policy should be treated as being incompatible.
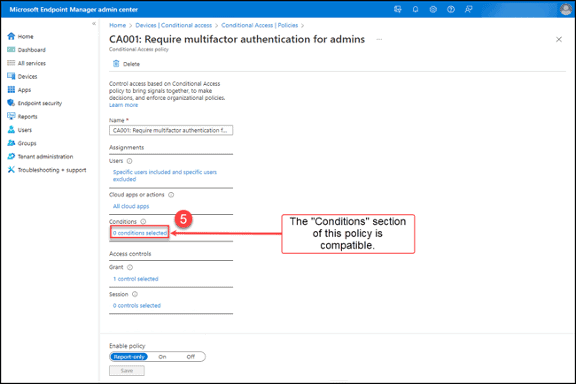
6. The “Require multi-factor authentication” control in the “Grant” section of the policy is selected. The settings in this section are compatible. Continue checking the other sections of the policy.
- If one of the documented unsupported controls or a “Terms
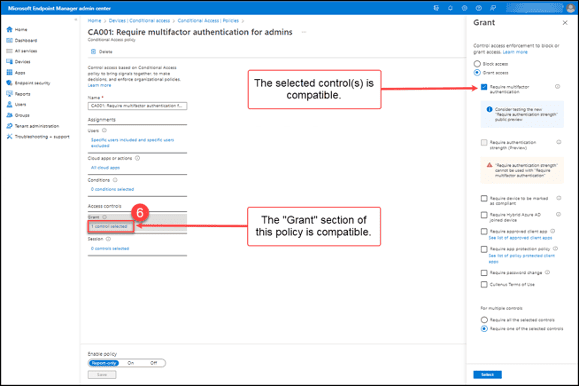
7. The “Session” section of the sample policy indicates that there are “0 controls selected.” The settings in this section are compatible with Teams Phones.
- If “Use Conditional Access Apps Control” had been selected, the “Session” section would not be compatible.
- A configured “Sign-In frequency” is supported, but this section should be treated as being incompatible.
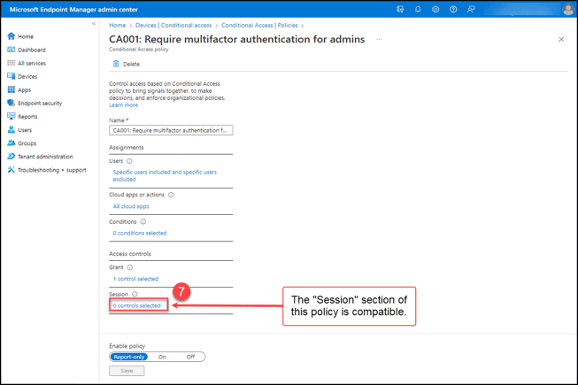
8. This policy has one section that is incompatible. Select and copy the query you used to create the “Teams Phone” filter in step 1 above from the open “Notepad” session. (I told you we would need this later!).
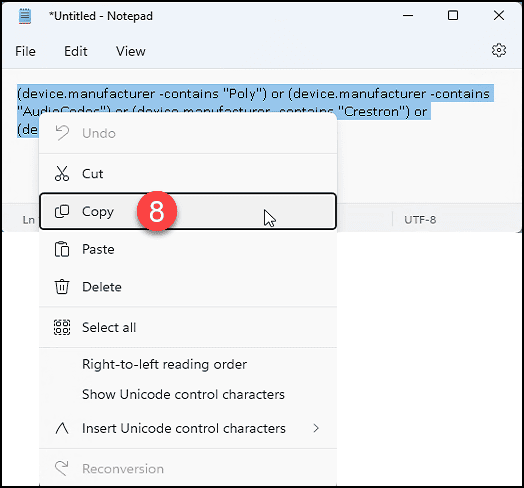
9. Click the “0 conditions selected” button in the “Conditions” section.
10. Click the “Not configured” button in the “Filter for devices” condition
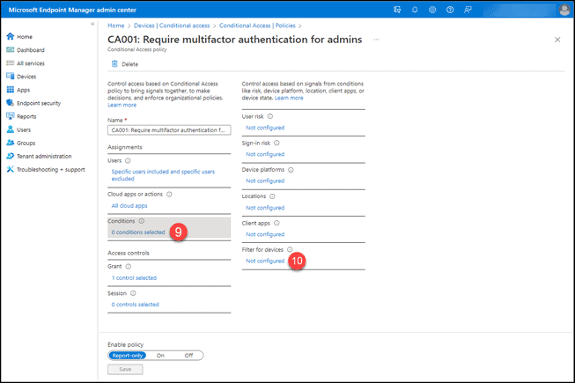
11. Set the “Configure” option to “Yes.”
12. Click “Exclude filtered devices from policy” in the “Devices matching the rule” section.
13. Click the “Edit” button above the “Rule syntax” box.
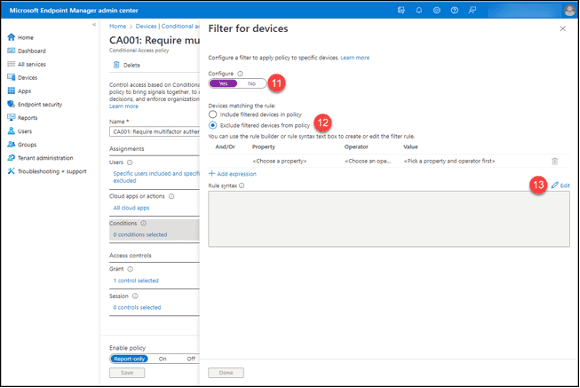
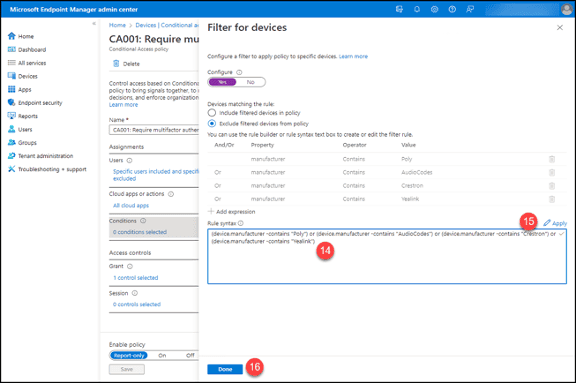
14. Paste the query into the “Rule syntax” box.
15. Click the “Apply” button above the “Rule Syntax” box.
16. Click the “Done” button.
17. Click the policy’s “Save” button. Continue checking the rest of the Conditional Access Policies.
Create a Teams Phones Conditional Access Policy
- Click the “New Policy” button.
2. Enter a name for the policy.
3. Click the “0 users or workload identities selected” button in the “Users or workload identities” section.
4. Click “All user” beneath the “Include” tab.
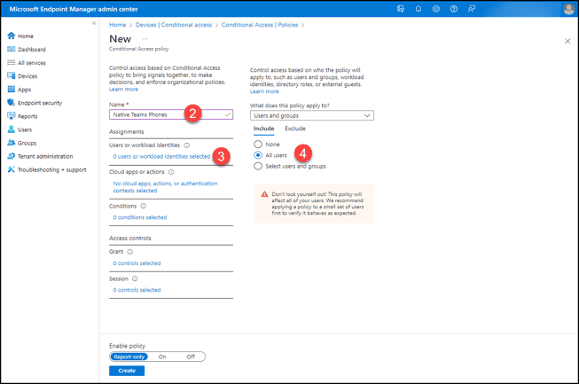
5. Click the “Exclude” tab.
6. Click “Users and groups.”
7. Add your emergency (“break glass”) account.
8. Click “No cloud apps, actions, or authentication contexts selected” in the “Cloud apps or actions” section.
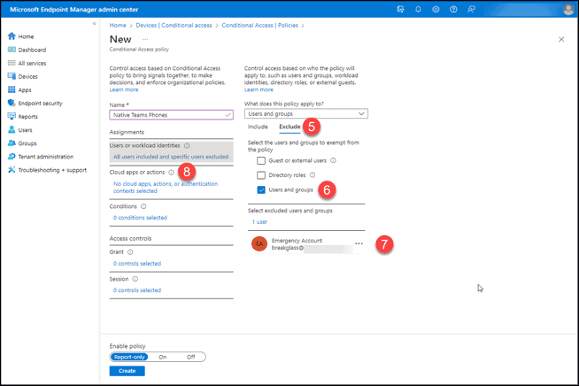
9. Click “Select apps” beneath the “Include” tab.
10. Click the “None” button in the “Select” section.
11. Click the checkbox next to “Office 365.” You could instead choose these applications:
- Microsoft Teams
- Office 365 Exchange Online
- Office 365 SharePoint Online
12. Click the “Select” button.
13. Click “0 conditions selected” in the “Conditions” section.
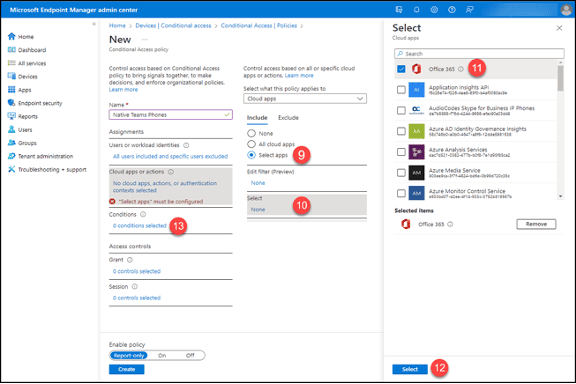
14. Click the “Not configured” button in the “Device platforms” section.
15. Set the “Configure” option to “Yes.”
16. Click on the “Select device platforms” option under the “Include” tab.
17. Click the “Android” checkbox.
18. Click the “Done” button.
19. Click the “Not configured” button in the “Locations”
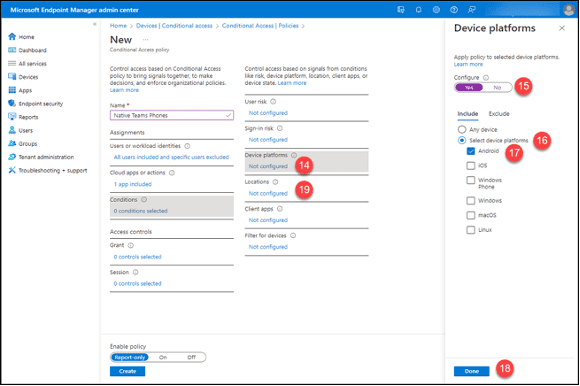
20. Set the “Configure” option to “Yes.”
21. Click “All trusted locations” (or whatever is appropriate for your deployment) beneath the “Configure” tab.
22. Click the “Not configured” button under the “Filter for devices” section
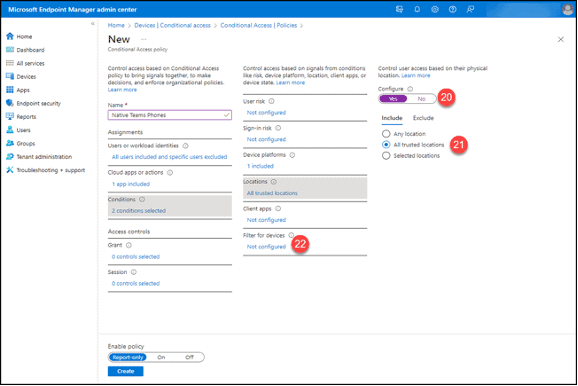
23. Set the “Configure” option to “Yes.”
24. Click “Include filtered devices in policy” in the “Devices matching the rule” section.
25. Click the “Edit” button to the right above the “Rule syntax” box.
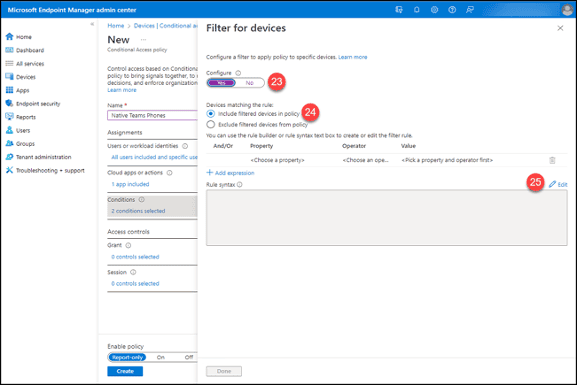
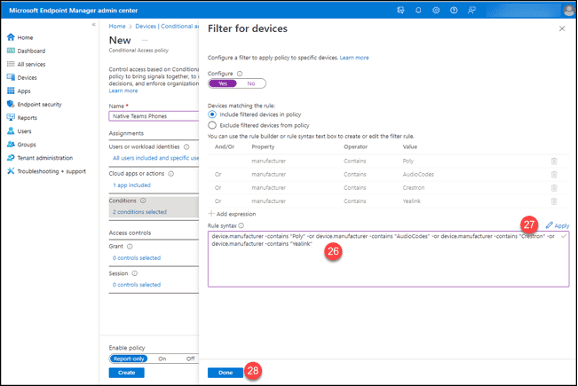
26. Paste the query from before into the “Rule Syntax” box.
27. Click the “Apply” button.
28. Click the “Done” button.
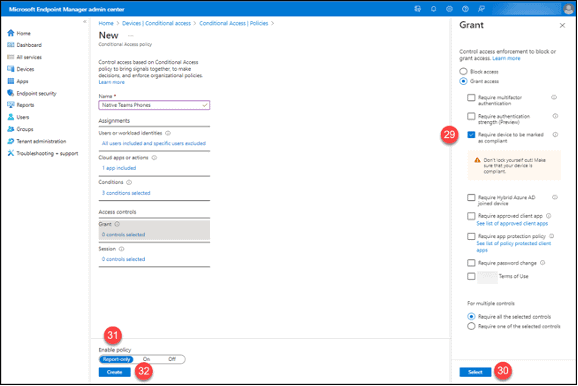
29. Click the “Grant access” option.
30. Click the checkbox for “Require device to be marked as compliant.” Select these options as required by your implementation. Make sure to avoid the unsupported options and Terms of Use requirements.
31. Click the “Select” button.
32. Click “Report-only” under “Enable policy.” Test the policy before turning it on.
33. Click the “Create” button.
Test the Teams Phones
- Identify a user account for testing.
- The user must be licensed for Microsoft Intune and Microsoft Teams.
- Make sure that the user can sign into Teams.
- In the Azure Active Directory Admin Center, navigate to the user’s account then click on “Devices” under manage.
- Clean up any obsolete devices for the user.
- Cleanup the enrolled Android Device Administrator devices.
- In the Microsoft Endpoint Manager Admin Center, click on “Devices” then “Android” then “Android devices.”
- Clean up any obsolete devices running under the “Android (device administrator)” Operating System.
- Take a new phone out of the box.
- Connect to an on-premises network and let the phone start up.
- Troubleshoot any issues that occur during the start up.
- Sign on to the phone as the test user.
- Verify that the logon succeeds.
- Review the setting for “Mark device compliant” in the “Teams Phone” Android Device Compliance Policy, it should be set to one (1) day. Wait at least twenty-four (24) hours and verify that the phone has not signed out, locked up or had other issues.
- If you have Teams Phones that you have tried to setup before making these changes, reset them back to the factory defaults! This will be much easier than trying to troubleshoot these phones after you’ve completed the configuration of Intune. Here are some links for resetting Teams Phones.
- Poly CCX
- AudioCodes C450HD See page 27 and following.
- Yealink MP54 and T55A Phones See page 75 and following.
- Crestron Flex
Test the Teams Phones with Applied Teams Configuration Profile
- Verify that the settings in the profile are working as configured on the phone.
Summary
- Integrating your Teams Phones with the Microsoft Security and Compliance suite of products is possible. Special handling is required for several of the components:
- Intune Enrollment Policies
- Intune Compliance Policies
- Intune Configuration Profiles
- Microsoft Application Manager Application Protection Policies
- Azure Active Directory Conditional Access Policies
- Even though they run under the Android operating system, Teams phones and devices need to be handled separately from your Android cellular phones and tablets. The Teams phones and devices use the Android Device Administrator management platform while the rest of the Android based products use the Android Enterprise Manager.
- Teams phones and devices, once installed, tend to not move. In most cases they should be treated as Company owned devices. Their serial numbers or IMEIs must be defined in Intune.
- There are few simple rules of thumb to follow when configuring the policies to work with Android Device Administrator managed devices:
- Create an Intune Device filter. Use the filter’s query to include or exclude the devices from your Conditional Access Policies.
- Make use of the Intune “All Users” and “All Devices” virtual-user groups when assigning the various policies.
- You should only apply the Intune Device Filter to policies that have user type assignments. Do not apply the filter to policies with device type assignments.
- Create specific policies for Android Device Administrator managed devices. Prevent all other policies from being applied to these devices.
- Remember that these policies have some settings that are supported by these devices but should be avoided.
- Test your policies on a subset of your users and devices before applying them globally.
eGroup | Enabling Technologies is available and ready to help you with the integration of your Teams devices into your organizational security and compliance plan. Excluding them from your security and compliance deployment is not advisable. If you need help with your Teams devices or in implementing your overall security infrastructure, please contact us today!
References
- Supported Conditional Access and Intune device compliance policies for Microsoft Teams Rooms and Teams Android Devices
- App protection policies overview Look for the section on Microsoft Teams Android devices.
- Conditional Access and Intune compliance for Microsoft Teams Rooms
- Authentication best practices for Teams shared device management on Android devices
- Known issues in Teams Rooms and devices



