The Challenge
Many organizations have data governance on their minds to some degree. Some are actively working on initiatives to apply retention, data loss prevention, and other controls on the data in their tenant. More often, though, IT organizations struggle with where to start, and how to get their arms around data that is owned by everyone in the organization but them. This is often exacerbated by the lack of effective organizational policies around retention and sensitive data protection.
Even if your organization is not a regulated industry like banking, government, or healthcare, you are almost always going to be subject to some kind of state regulation and disclosure requirements in the event of a breach. Often, you may also be subject to another state or country’s regulations if you do business or have customers there. Data governance challenges apply to every organization that has sensitive data stored somewhere.
To help manage the risk and provide protection, enter Microsoft 365 Purview. This is a great data governance tool, and it has a huge and often overwhelming set of features that will require many blog posts to cover. Today, I am going to focus on how Microsoft Purview Content Explorer can be used to help identify where sensitive data is in your tenant (stored in Exchange Online, SharePoint Online, OneDrive for Business, or Microsoft Teams) and how that information can be used to help provide a starting point to build momentum for a data governance initiative.
Knowing Your Data
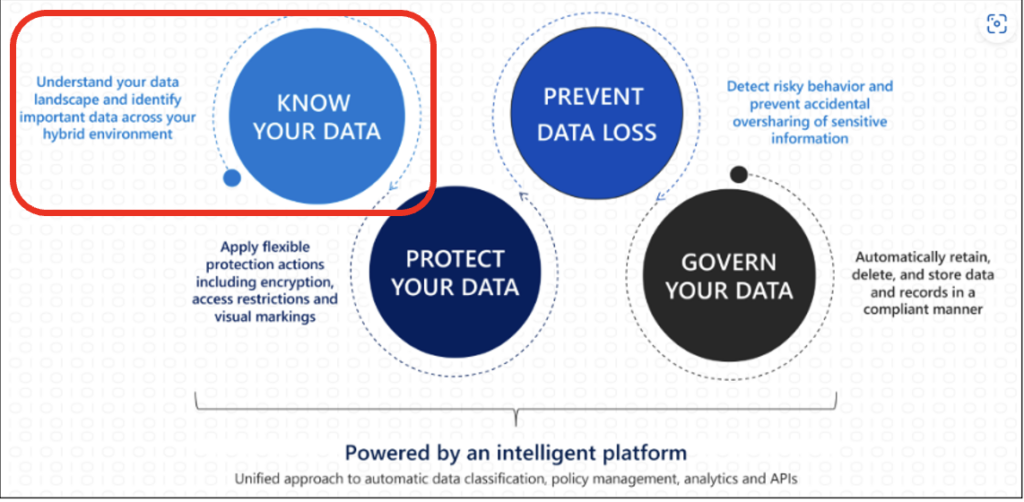
Here is one of Microsoft’s diagrams that I like to reference when talking about Purview and what it does. The Know Your Data step is often the most difficult to achieve, since so many data owners exist in most companies.
Content Explorer makes it easy to start to get to know your data and is included as part of E3 and E5 licensing, so you can probably start using it today to see where some kinds of sensitive data are located. It identifies common types of sensitive data automatically based on hundreds of built-in data patterns like Social Security Numbers, bank account information, or driver’s license numbers. Content Explorer also shows you where these data types are located, and you can even drill down to the file or email message that contains it.
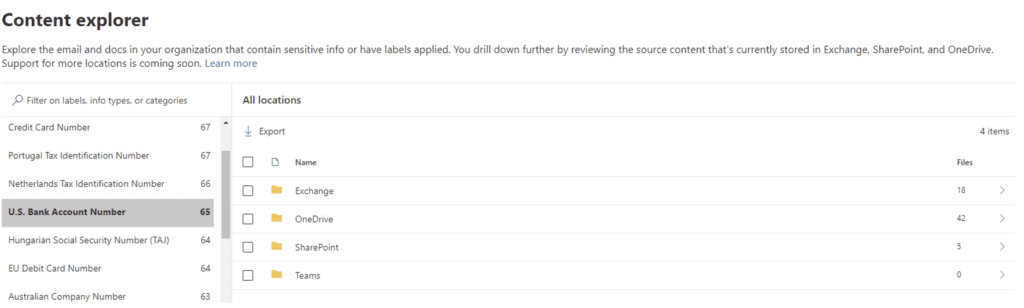
By the way, not just anyone can go to your tenant Admin portal and start browsing confidential data. There are specific Azure Active Directory (AAD) and Purview roles that you must explicitly be made a member of to see any actual data beyond the aggregated metrics shown above. Remember that it isn’t always an “IT” person that needs to do this. Access can be delegated to legal, HR or compliance staff to maintain confidentiality.
Most of the time, organizations find that sensitive data is just…well….everywhere. Both where they expect it, like HR files, and where they don’t, like the marketing manager that has 500 social security numbers in a hidden tab in an email attachment about last year’s employee holiday gifts. (Yes, this happens.)
Using What You Discover
Using the out-of-the-box sensitive data types is a great way to start a data governance conversation with management. It shows that there is indeed a lot of sensitive data out there and the organization is at risk of both bad actors or employees being able to exfiltrate data that would require disclosure, incident response costs, and cause a public relations nightmare.
Even in companies where there is no CISO, there is usually a group that worries about business risks and often they can be a good advocate for information security risks as well. It is critical to engage them (often finance, legal, or HR) to be partners in a data governance effort. If it is only led by the technology team it can be very challenging to get people to listen and act.
Following the start of the conversation, the governance team should drive toward the following:
- Perform a risk assessment to really dig in and understand the exposure and potential costs of a breach. This should include disclosure requirements.
- Decide on thresholds of the amount of data to trigger a restriction or response. It’s probably OK for an employee to have one or two Social Security Numbers in their mailbox that they used in communication to HR about benefits. However, if they have 10 of them, then that should be investigated.
- Create or update data handling policies that you can base retention, sensitivity, and DLP controls on.
- Take actions that will reduce risk over time, starting with the most critical. Often a purge of stale data (especially email) is a great place to start. Stale data only presents risk and has no real value to the business.
- Establish an ongoing data governance program to increase effective controls over time. Establishing governance controls can be hard to get right initially. Leave time to define and tune your data types, restrictions, and to provide plenty of communication and training. Business processes may need to be changed to accommodate new policies or controls. Manage the changes and establish new norms over time.
- Set up access reviews of critical data locations. If you have AAD P2 licensing, set up periodic access reviews of groups that have access to critical data, like HR or finance. This requires the infosec team, or the leader of those groups, to look at who is in the groups providing access and remove anyone who doesn’t belong. This prevents permission drifting as employees move around the organization or close out projects that required temporary access.
Conclusion
Many of the controls and actions I discuss above are other features of Purview that I will explore in more detail in future blogs. Also, I provide a high-level description of some of those features and how they complement your traditional security controls here.
Using Content Explorer to see what common sensitive data types are detected does provide a great starting point, but it is often just the tip of the iceberg. Purview provides robust searching and customization functionality, in addition to all the pre-configured options. Stay tuned for more discussion on this topic in the coming weeks. In the meantime, if you want to learn more, my colleagues and I help clients with Purview and data governance planning, design, and governance programs all the time. Please reach out if you need some help!
Learn more about Microsoft Purview
Interested in learning about the features included with Microsoft Purview and how they can simplify your compliance and data governance efforts?
Contact our team of experts today!



