The Pros and Cons of Threat Hunting

Assuming Breach
Stealthy supply chain attacks like Solorigate and Log4j have shined a light on the importance of assuming breach. When these attacks hit the news, vendors and analysts often suggest to “hunt for Indicators of Compromise.” IT and security pros spend nights and weekends determining the extent of the risk within their organization, then come up with a plan to isolate, patch, or otherwise remediate the issue. That’s easier said than done, especially for small security teams. It’s even harder to keep up with the near-constant, less-publicized threats, like the one that CISA advised to hunt for last week.
This blog outlines what it really means to be a threat hunter, provides realistic advice for organizations with limited means to do so, and highlights how the automation of Microsoft’s security suite makes threat hunting more scalable.
What Does Threat Hunting Entail?
Threat hunters discover unknown or stealthy attacks that might have bypassed existing security measures. Threat hunting is especially crucial in supply chain attacks, which evade traditional detection systems because their patterns appear “normal” and don’t trigger an alarm.
Threat hunting is a Security Operations Center (SOC) function. It’s rare that an IT Pro or individual security pro has time to proactively search for, analyze, and identify potential security threats, especially in hybrid cloud environments.
Hunting starts with a hypothesis. A hunter may generate a hypothesis based on internal (i.e. one VIP Is breached, so they’ll check on others) or external information (such as threat reports, blogs, and databases of Indicators of Compromise (IOCs)).
Like with log4j, the security community is the best source for what to hunt for. Vendors, industry, and researchers (eventually) publish IOCs. CISA’s article includes IOCs for threat hunters to follow up on. Separately, a SANS analyst advised that “You should be checking for installations of any remote management software.”
Hunting tools and techniques involve the analysis of logs, network traffic, and security alerts to identify patterns of behavior that may indicate a security breach or attack. The goal is to detect, prevent and respond to security incidents before they result in a breach or significant damage.
Microsoft’s Threat Hunting Tools
The key tool in Microsoft’s threat hunting arsenal is Sentinel, the Magic Quadrant-leading Security Information and Event Management (SIEM). Sentinel provides the most robust way to scan for threats across the broadest set of IT systems. The Defender suite also has hunting capabilities along with Kusto Query Language (KQL) capability, if it’s not possible to use Sentinel.
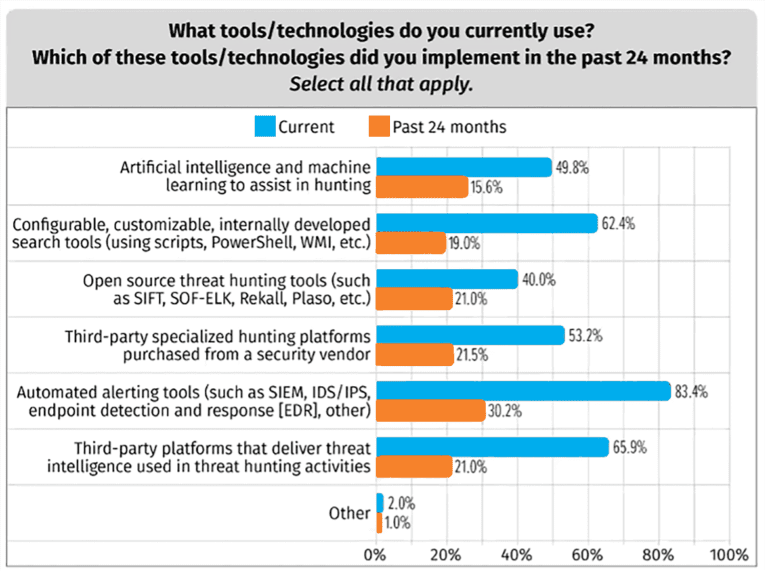
SANS survey in 2022 confirmed that most (83.4%) hunters are using SIEM technology to hunt.
Sentinel can be integrated with threat intelligence from various sources, including Microsoft Threat Protection and third-party STIX/TAXII systems feeds. STIX (Structured Threat Information eXpression) and TAXII (Trusted Automated eXchange of Indicator Information) are open standards for exchanging cyber threat intelligence. Leading examples include AlienVault and PickupSTIX. Integration with STIX/TAXII systems allows Microsoft Sentinel to receive threat intelligence from a variety of sources, including internal threat intelligence platforms, third-party threat intelligence providers, and community-based threat intelligence feeds. This information can be used by hunters in a more automated way, rather than them having to import and custom-create their own hunting code every time (using KQL).
Pros of Threat Hunting
Threat hunting enables:
- Early detection of attacks, identifying incidents before they cause damage.
- Improved security posture, by identifying and mitigating weaknesses in their security systems.
- Increased visibility into the network environment, allowing better understanding of the baseline behavior and the differences when attackers are present.
- Better resource allocation, by proactively reducing recovery and remediation time.
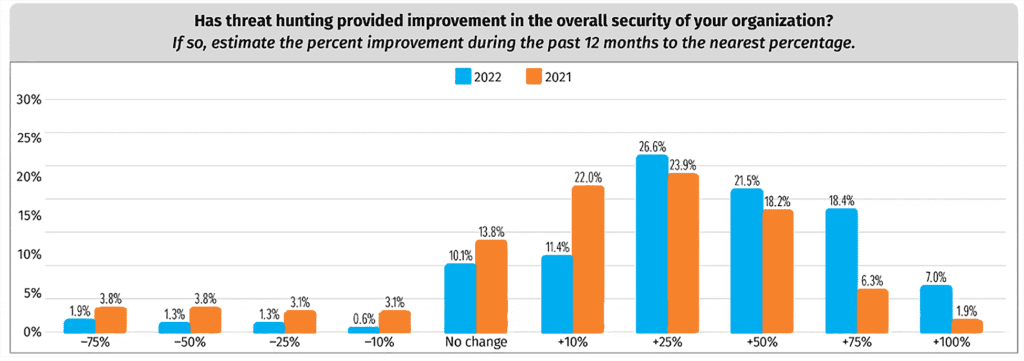
In SANS 2022 Threat Hunting survey, improvements from hunting are well above 25%.
Challenges of Threat Hunting
So why doesn’t everyone take the CISA directions, and act? There are many factors on why it’s difficult.
- Threat hunting requires specialized skills, knowledge, and tools to effectively identify and analyze.
- That requires a deep understanding of the network and systems being monitored.
- Hunters need an understanding of attacker behavior and tactics.
- Hunting can result in a high number of false alarms, which can be challenging to manage and could lead to a decreased level of confidence in the security team’s findings.
- Threat hunting requires significant time and effort, and may require additional staffing or specialized tools and expertise. People who wear multiple hats struggle prioritizing proactive tasks.
Finally, threat hunting can be a rabbit hole. CISA’s recent advisory suggests that “The authoring organizations strongly encourage network defenders to review the Indicators of Compromise (IOCs) and Mitigations sections in this CSA.” The CISA post included a list of five (observed) Malicious Domains and IP addresses observed by CISA, but not how to check if an environment has been exposed by said domains. They also link to a more thorough blog from security researchers, which included a much lengthier list of IP addresses and phishing domains. Which list should be used, practically? How does a SOC decide, and ensure that a thorough check is completed?
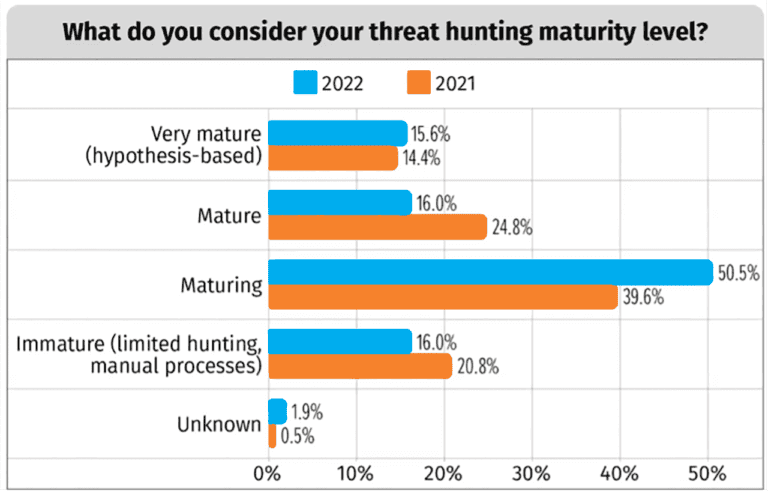
For all of those reasons, only 15.6% of SOCs surveyed by SANS had personnel dedicated to a “very mature” hunting process.
It’s frustrating for a security pro to know what to look for, but not how– and equally so for a CISO who’s invested in a SOC, who’s not sure if the investment is paying off.
What Can a Short-Handed Team Do?
Organizations without a dedicated Security Operations Center (SOC) and limited personnel can still be proactive by:
- Prioritizing resources: Focus on the most critical systems and data, and prioritize resources accordingly. For instance, start with threats that would impact domain controllers, ERPs, or other critical infrastructure.
- Implementing basic security measures such as conditional access/MFA, firewalls and Endpoint Detection and Response (EDR), patching servers and PCs, and ensuring privileged access controls are in place and up to date.
- Using automated tools to collect and analyze data from various sources, such as network logs and security alerts. These tools can help automate the detection of potential security incidents, allowing the limited personnel to focus on more complex tasks.
- Collaborating with peer organizations in sharing threat intelligence and best practices, as well as participating in threat hunting exercises.
- Leveraging third-party security services, such as managed security service providers like eGroup | Enabling Technologies, to supplement the limited in-house resources.
Having limited personnel can make it challenging to hunt threats effectively, and organizations may still need to consider using outside resources or outsourcing some of their security operations. For those looking to build in-house hunting capability, SANS has a nice outline.
How eGroup | Enabling Technologies Hunts for Threats
For organizations who find value in threat hunting but lack the time or resources, eGroup | Enabling Technologies can be a resource. Our team has experience with the processes, tools, attack vectors, and remediating steps of threat hunting.
As an example of the automation and proactivity of the ThreatHunter team, I sought to understand how our team was responding 24 hours after the CISA alert.
The team monitors IOCs in several ways, including:
- AlienVault, a feed of open threat intelligence community data with 20 million threat indicators contributed daily, which connects directly into Sentinel as a LogicApp.
- PickupSTIX, a TAXII service that uses three public feeds and distributes about 100 new pieces of intelligence each day.
- RSS feeds of news into a Teams channel which is monitored by hunters.
- Manual tracking of news posts, blogs, and threat hunting forums (which is how the CISA alert was picked up).
Either by direct feeds or manual inspection, the IOCs (be they IP, URL, File hash, or process) are entered into a gold list of IOCs in Microsoft Sentinel. The IOCs act as a sort of watchlist for a set of analytic rules.
That gold list of IOC’s gets synchronized to all of our ThreatHunter Managed Security Service (MSSP) clients via a LogicApp, which is monitored for any failed runs. If any of the IOCs (of which there are thousands at this point) are seen in customer environments we’re monitoring, the automated analytic rules will catch them and report an incident, prompting our hunters to investigate deeper to validate or resolve. Often the resolution can be automated (i.e. a phishing email from an offending domain can be deleted by Defender for Office Automated Investigation and Response), but if necessary, manual intervention and remediation are provided.
Summary
Hunting for threats is an important aspect of an organization’s security posture, especially to counter the growing trend of stealthy supply chain attacks. Organizations can hunt for threats on their own by utilizing various tools and technologies, including SIEMs like Sentinel, threat intelligence platforms like AlienVault and PickupSTIX, and extended defense and response solutions like Defender. Organizations with the staff have a unique advantage – they can combine the tools, knowledge of in-house systems, and awareness of their business to analyze data and identify potential security incidents.
Meanwhile, organizations without the resources, including personnel and technology, to effectively hunt for threats, can consider using eGroup | Enabling Technologies MSSP. Built on Microsoft technology, we provide the necessary tools and expertise to effectively detect and respond to security incidents, automate the threat hunting process, reduce the time and effort required to detect and respond to security incidents, and allow your organization to focus on its core business operations.

Chris Stegh
CTO & VP of Strategy - eGroup | Enabling Technologies

