Zero Trust FAQs – Summary of Three Webinars with Microsoft
eGroup | Enabling Technologies and Microsoft completed a trilogy of webinars on Zero Trust. Several questions were covered live, but due to time constraints, this blog reviews and answers all that were asked. The blog also reviews the survey data from our attendees, which show a significant dichotomy between what IT pros think about ransomware risk, and what their business leaders think about the risk.
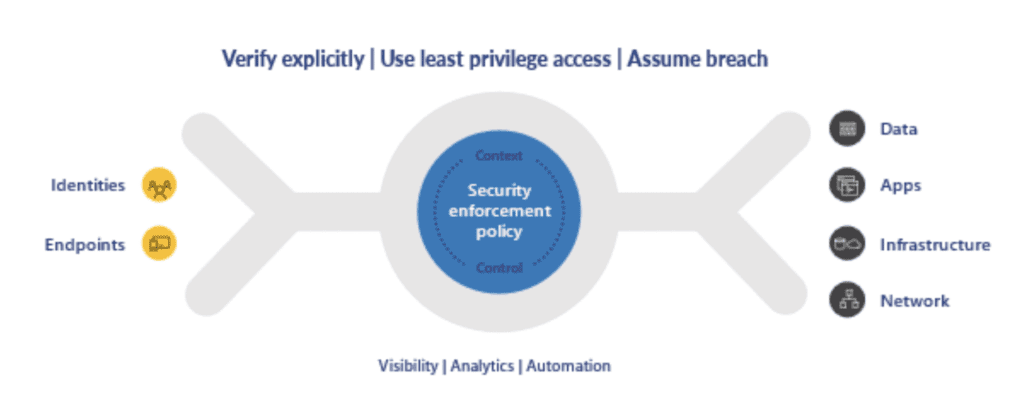
To review, Microsoft defines Zero Trust based on three principles.
- Verify explicitly
- Limit privileges
- Assume breach
The span of zero trust must cover identities, devices, apps, data, infrastructure, and networks, as shown below:
Webinar Topic #1 Protect:
Caiden Scherer from Microsoft keynoted our first webinar covering Zero Trust all-up, and how Microsoft’s tools can Protect organizations from catastrophic incidents. We covered how reducing the surface area of out of the box PCs can protect from fileless and ransomware attacks, and the importance of consistent deployment and patching (using Intune and Autopilot). We discussed Microsoft 365’s capabilities for information protection and data loss prevention. And since identity is today’s perimeter, we outlined how conditional access rules can reduce phishing and identity compromise by considering the status of the (un)managed device and its health into the block/allow access decision. But we also reminded people of the dangers of password spray attacks when Basic Authentication is left on.
Q1: “This Zero Trust approach is geared to company owned devices. How does this apply to BYOD?”
A1: “The Zero Trust approach applies the same security policies regardless of BYOD or corporate-owned. For BYOD, that looks like managing and securing the apps and data and verifying identity.”
Q2: “How do I know if my tenant is using Basic Authentication?”
A2: Basic (or Legacy) Authentication doesn’t allow MFA or modern identity capabilities, and should be turned off ASAP. Take a look at your Azure AD Sign-In log, as it can help identify ‘unexpected’ usage. Log into your tenant and click on https://aka.ms/PillarEXOBasicAuth to get a set of tools that can help ID basic auth. MSFT is also going to start sending Message Center posts to tenant admins summarizing their usage (or lack of). Microsoft is turning off Legacy Auth in all tenants (except SMTP relay) in Oct 2022. Be ready by reviewing our blog End of Life of Legacy Auth on ExchOnline – Easier said than done!
Q3: “What if service / automation accounts use Basic Authentication?”
A3: Such identities can be better protected by creating a cert for automated powershell accounts, per https://docs.microsoft.com/en-us/powershell/exchange/app-only-auth-powershell-v2?view=exchange-ps
Q4: “How can I prepare for password spray or phishing incidents?”
A4: Turn off Basic Auth and enable MFA. Assuming they’ll get through somehow, Microsoft publishes a set of steps to respond to each. https://docs.microsoft.com/en-us/security/compass/incident-response-playbook-password-spray Enabling recommends a more comprehensive Incident Response Tabletop Exercise to evaluate the efficacy of your ability to respond.
Webinar Topic #2 Detect:
Corey Lee from Microsoft provided expert commentary in our second session. When “assuming breach,” one admits that no amount of protection will make an organization completely secure. As such, it’s necessary to put tools in place to detect breaches, or better yet, anomalies that could lead to breaches, both reactively and proactively.
We started with a case in point: log4j. No employee or missing configuration created this risk, yet it’s prevalent in most organizations. We demonstrated how to use Threat Analytics to find log4j and other stealthy vulnerabilities. Next we demonstrated how to leverage User Entity Behavior Analytics (UEBA) to scan for anomalous behavior that could tip a SOC off to novel zero day attacks. We outlined the multi-cloud capabilities of Defender for Cloud to detect risk in servers on-prem, in Azure, AWS, or GCP. And importantly, we demonstrated how to sense lateral movement and ransomware attempts against your crown jewels (Active Directory) with Defender for Identity.
Speaking of ransomware, our survey results show a concerning difference between how business leaders feel about their organization’s readiness to deal with ransomware, versus the attendees’ confidence. Check out difference in the charts shown below. The first chart shows how less than 50% of IT and SecOps pros are comfortable with their organization’s protection against ransomware. However, the second chart shows how those same IT and SecOps pros feel about their business leaders’ confidence.
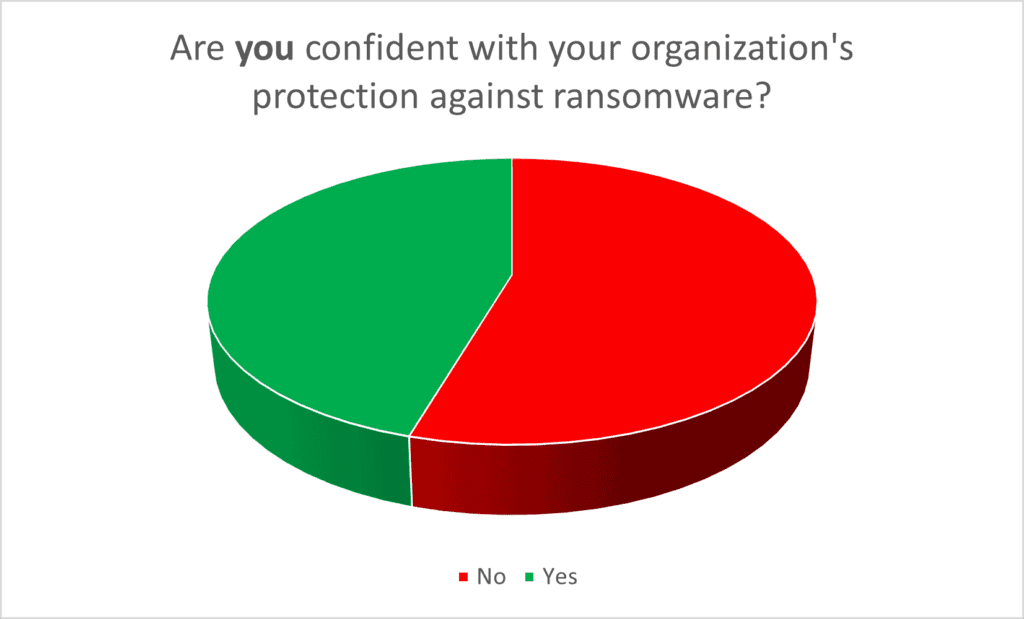
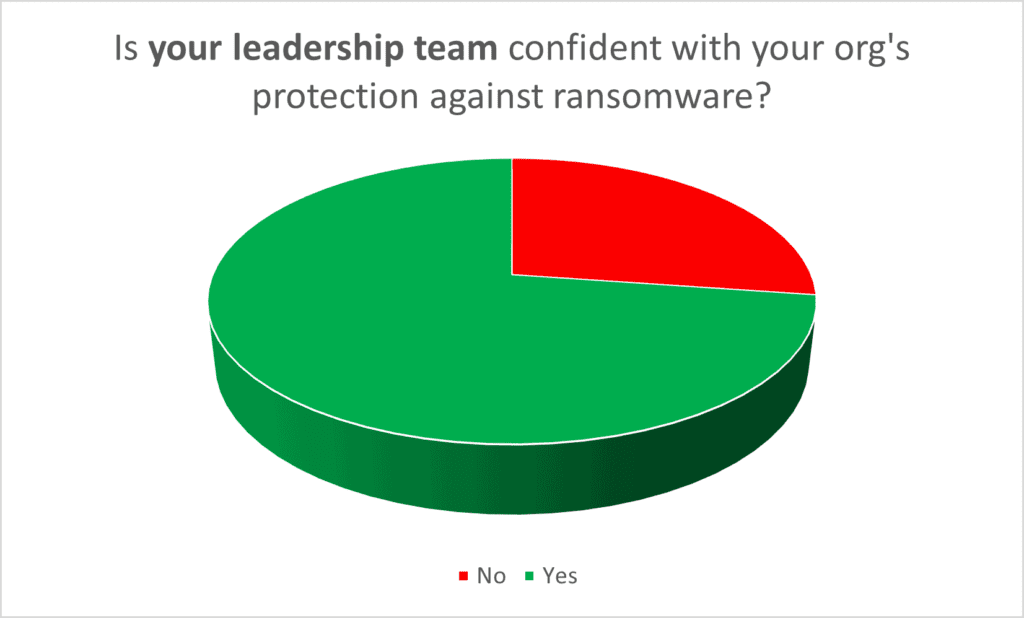
70% of business leaders feel comfortable that their IT departments have things handled. That means 25% of business leaders are more confident than their IT counterparts. Why? Perhaps simply having a discussion with IT (per the White House’s Executive Order) has elevated leadership’s confidence. But unless significant budgets are allotted to people, technology, and training, then IT pro and SecOps pros are still feeling exposed. To those 25% in the gap, overcommunicate before it’s too late, and thoroughly plan your recovery now (just like the 50%+ on the left lacking confidence should be doing).
Attendees again asked some excellent questions:
Q5: “How do I know if instances of log4j exist in my environment?”
A5: Hunt for them using MSFT tools like Threat Analytics. https://www.microsoft.com/security/blog/2021/12/11/guidance-for-preventing-detecting-and-hunting-for-cve-2021-44228-log4j-2-exploitation/#TVM
Q6: ”Is Threat Analytics updated with the latest CISA BOD directives re: vulnerabilities to patch?”
A6: Microsoft closely follows CISA and other federal and industry benchmarking bodies at all times. The Threat Analytics reports are created by Microsoft security experts to ensure the recommendations follow required directives. Additionally, other recommendations are provided within Defender for Endpoint Threat and Vulnerability Management using all known CVEs.
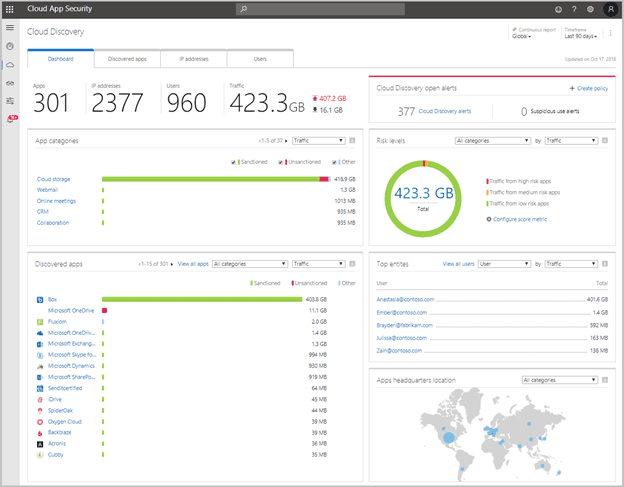
Q7: “In Defender for Cloud Apps, we see tons of usage of third party SaaS, very frustrating at times when trying to see what tripped the alert. Are these all apps? They appear to just be links or websites in our instance – not truly an app.”
A7: In Defender for Cloud Apps’ Cloud Discovery Report (ex. shown below), the elements that appear SaaS services, so they may appear as just websites, but they are all a form of application. The list you see shows any users or device that accesses that cloud service, whether from a browser or a thick app.
Webinar Topic #3: Respond
In session three, we were joined by cybersecurity attorney Melissa Ventrone from Clark Hill LLP. She outlined what to do (and not to do) during an incident to minimize legal fallout that might follow. She highlighted the importance of a well-practiced Incident Response Plan which engages colleagues outside of Infosec & IT. Having corporate counsel, communications, and executives involved facilitates quicker decisions and better preserves the time of the IT and SecOps teams to eradicate the issue.
As Ms. Ventrone stressed, when assuming breach, response plans become mandatory. The challenge is that when SecOps and IT pros are too busy responding, they can’t step back to do a better job protecting and detecting. A solution to this vicious cycle? Automation.
We demo’d tools from Microsoft that collate behavior and events into a consolidated and often automated set of tasks. They allow SecOps pros to automatically resolve incidents, rather than manually investigating each. The tools involved included Microsoft Sentinel (Security Information and Event Management) / SOAR (Security Orchestration Automated Response), Defender for Cloud, Defender for Cloud Apps, and Microsoft 365 Automated Investigation and Response (AIR).
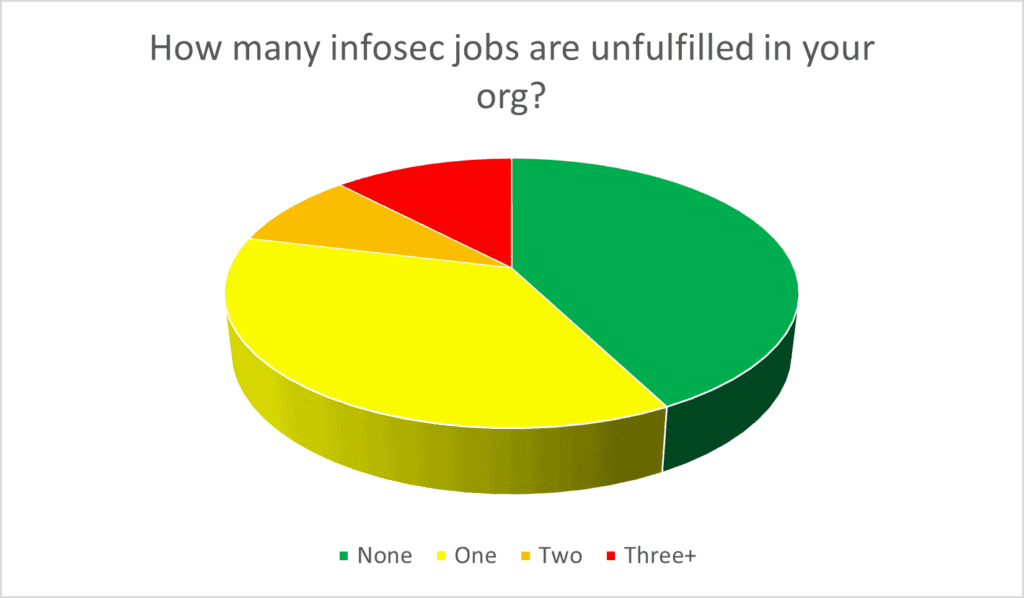
Why is automation so important? Security Operators are in demand, as shown from the survey results below. 60% or organizations have one or more open infosec jobs that are unfilled. Automate or cry!
Another round of excellent questions were posed:
Q8: “Do you have a sample IRP (Incident Response Plan)?”
A8: https://nvlpubs.nist.gov/nistpubs/SpecialPublications/NIST.SP.800-61r2.pdf is the best outline of the necessary components. Many gov’t orgs post theirs publicly. Another solid resource: https://www.sans.org/white-papers/33901/ Enabling has a Pro Service where one of our CIO advisors helps to build incident response plans for customers, then test them against best practices.
Q8: “Is Sentinel is separate additional license on top of the E5 or E5 security add-on?”
A8: Microsoft Sentinel is an additional cost separate from M365 E5 licenses. See https://egroup-us.com/microsoft-sentinel-eguide/
Q9: “Are some (Sentinel) playbooks based on the level of subscription you have?”
A9: Not really, the ones showing are out of the box. Obviously, for some that are orchestrating responses on 3rd party systems (you saw Cisco ASA for ex), you’ll have to pay to have the device onboarded/sending its data into Sentinel.
See eGuide: https://egroup-us.com/microsoft-sentinel-eguide/
Q10: “What fraction of Sentinel consumers take advantage of the automation features?”
A10: 100% take advantage of one or more automations. That could be as simple as automatically opening a ticket in ServiceNow or ITSM. What he’s showing now is also common (pop a screen in Teams). As far as automatic remediation (i.e. blocking a port in a firewall, or blocking an AAD acct), far less. Most want to wait to ensure there’s true positives before automating.
Q11: “What was the free MS access you talked about please?”
A11: FastTrack – ask your MSFT rep or info@eGroup-us.com
Final Thoughts:
This trilogy may be done, but our work never is. We’ll be back in March with more webinars on Zero Trust and Extended Detection and Response (XDR).
Additional survey results are shown below for your benchmarking purposes.
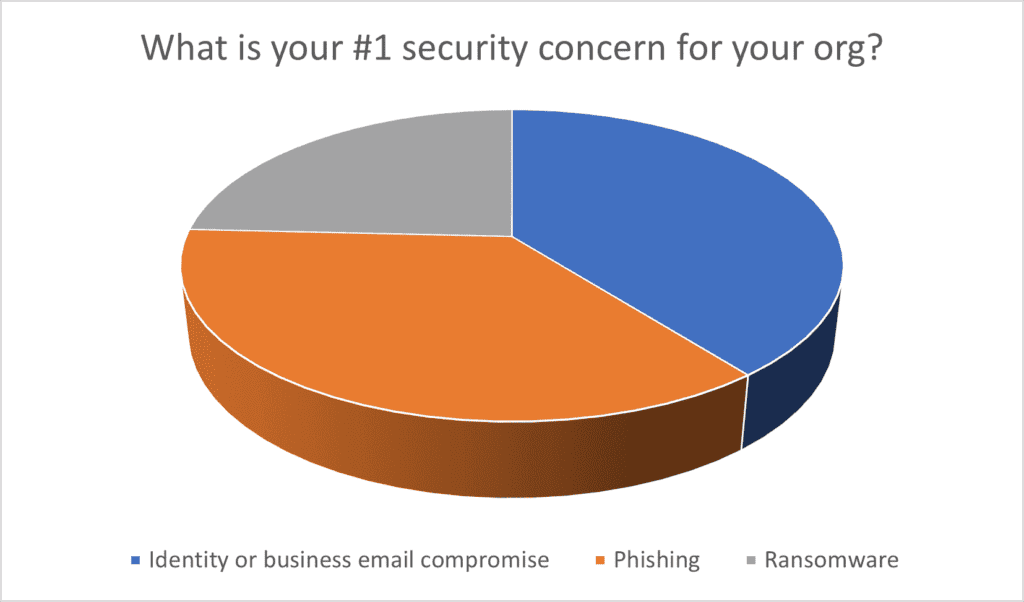
Note: Supply chain attacks and insider threat/theft had zero (0) votes.
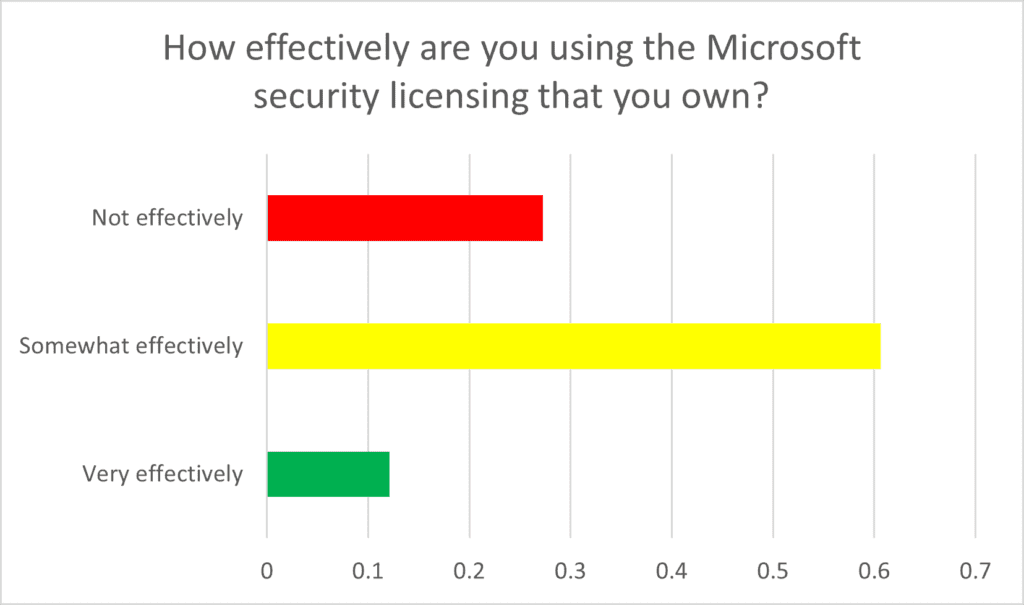
For a rundown of how you can better utilize your Microsoft 365 licensing, follow our blog, where we regularly post ideas and examples.
If you have questions or would like to schedule time with our team to discuss the specific needs of your organization, reach out to info@eGroup-us.com

Chris Stegh
CTO & VP of Strategy- eGroup | Enabling Technologies

