Easily Collaborate with External Microsoft 365 Users

Remember what a nightmare it was for the Griswolds when Cousin Eddie came for a visit? Microsoft Entra ID (formerly known as Azure AD) administrators might feel the same way with the options and headaches that come with managing external identities. The Griswolds were gracious hosts– Directory and data managers can also be gracious hosts by following some emerging trends for managing guest access.
Problems Hosts Can Have with Visitors
In Microsoft 365, significant challenges when providing access to External Identities:
Common Needs and Current Solutions for Guests
Organizations have several reasons to provide an external person with access to their apps or data. A contractor may need a full AD account and a VPN to access on-premises or cloud services. A vendor may need access to a SharePoint site to upload data. An external project team member may want to collaborate within another organization’s Microsoft Team environment.
A traditional solution was to create new directory credentials for external users. However, if the external person left the other company, how would the host organization know to clear the account? Active Directory Federation Services could span organizational boundaries, but is complex and coarse, with little control of access or visibility into the apps or data being accessed.
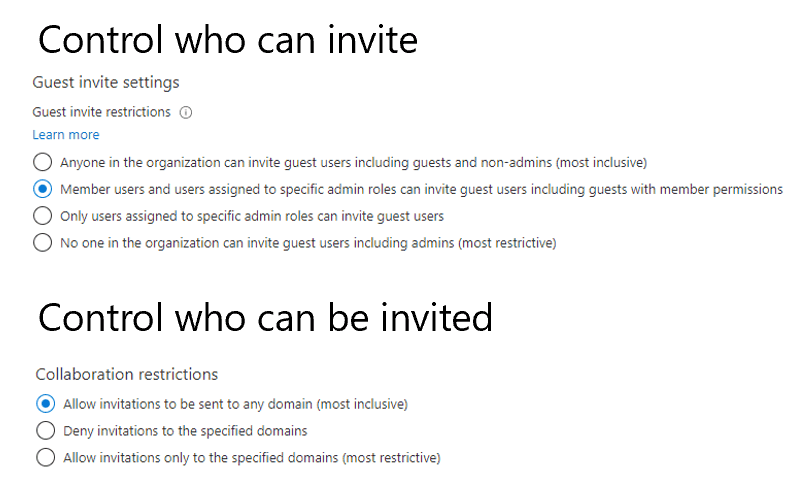
Thankfully, more flexible options are emerging, steadily trying to solve these challenges. This blog will outline some of the technical and user experience differences and provide some decision-making logic between three emerging models:
Three Modern Options
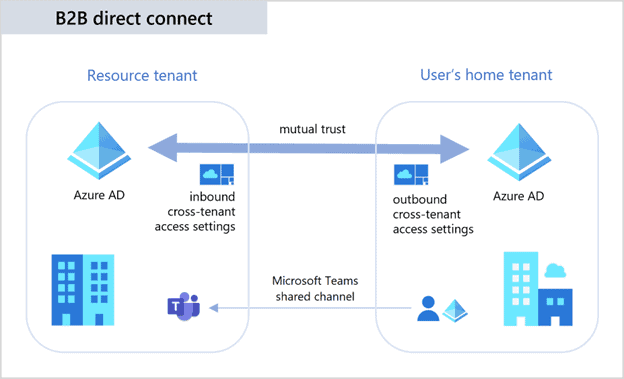
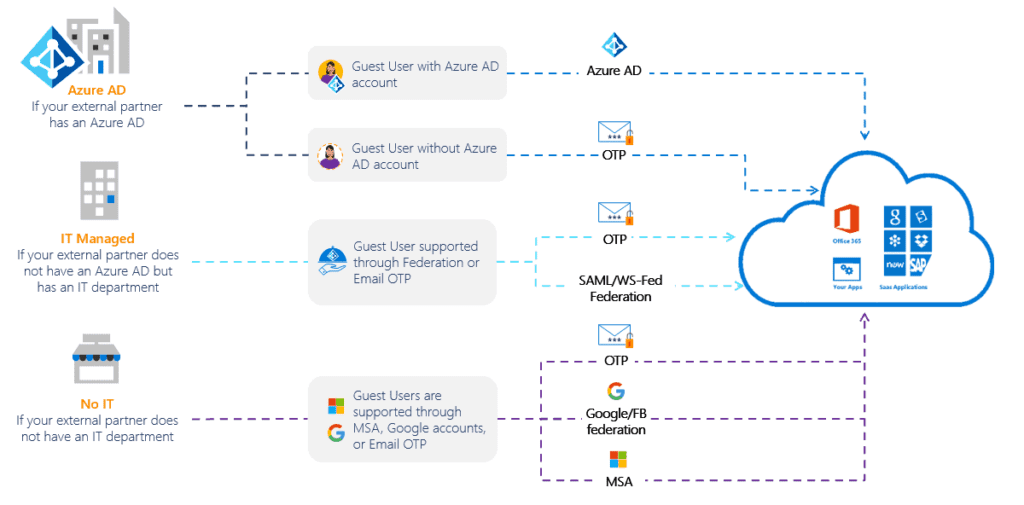
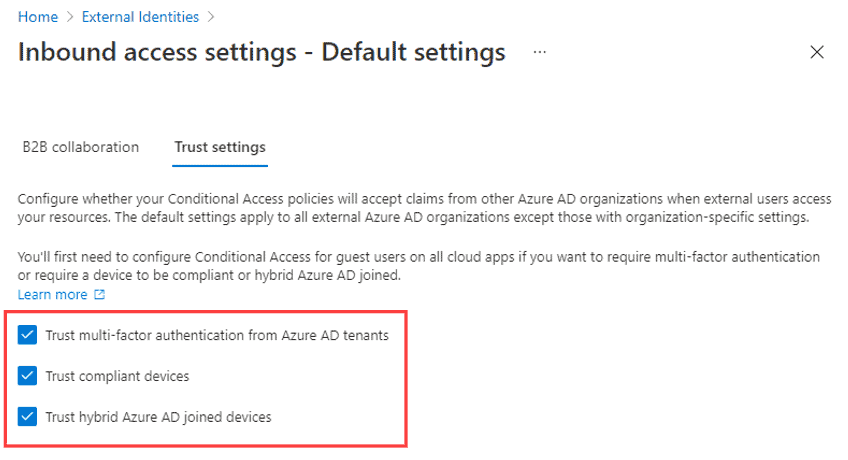
If relying only on B2B collaboration (or Cross-tenant Sync), an external user appears as a ‘Guest’ in Teams.
Conclusion
There’s no panacea to fully address the needs of end-users, system administrators, and CISOs when it comes to external collaboration. However, the emerging options are showing positive momentum.
Typically, decisions like this must balance the tradeoff between security and productivity. For instance, to approach the concept of zero trust, B2B Collaboration (Option 2) is the best choice. Option 1 (shared channels) is the best choice if the user experience is paramount, but only works for Teams.
You can mix and match. For instance, you might need to use B2B Collaboration if the external entity is a sole proprietor (contractor) using Gmail, or if the external org is too small to have an IT department. In the meantime, sister companies or agencies can also set up Cross-Tenant Synchronization. Expect improvements over time – one can envision each technique leveraging some capabilities of the others, since AAD is the common backplane.
CISOs and CIOs should make policy decisions that guide a system administrator’s implementation choices. External entities are another vector to take into close consideration. Decision matrices for unique organizations would be prudent.
Finally, you can view the comparison between the 3 methods, and keep an eye on this blog for announcements and updates.
Still unsure as to what options are right for your organization? Needing help auditing and implementing some of these processes within your current environment? Complete the form below to set up some time with our team to further discuss your specific business needs.

CTO & VP of Strategy - eGroup | Enabling Technologies
Interested in seamlessly collaborating with external Microsoft 365 users?
Contact our team of experts to get started today!
Last updated on August 6th, 2023 at 04:44 pm