For additional information or assistance securing and configuring your SBC Teams Direct Routing, contact our team of experts today! Our team has years of experience and knows all of the “minefields” to prevent missteps.
Secure & Protect Your SBC: Microsoft Teams Direct Routing

Introduction
I was recently deploying Microsoft Teams Direct Routing with IntelePeer SIP trunks and an AudioCodes Session Border Controller (SBC). Not long after the public interface was turned up, and before the Teams and IntelePeer configuration was completed, I could see significant amounts of SIP traffic coming in from various unknown sources. It started with OPTIONs requests, then INVITE and REGISTER requests soon followed.
Upon further review of AudioCodes traces, I could see attempts coming from IP addresses all around the world by means of known malicious SIP scripting and scanning utilities. The user-agent, to, and or/ from headers would contain hints such as “friendly-scanner”, “SIPVicious” and “PPLSIP”. Variations of the incoming SIP requests were without user-agent headers, contained various letter and number combinations, or even router names!
Here are some examples of the SIP messages encountered:
Examples of SIP Messages
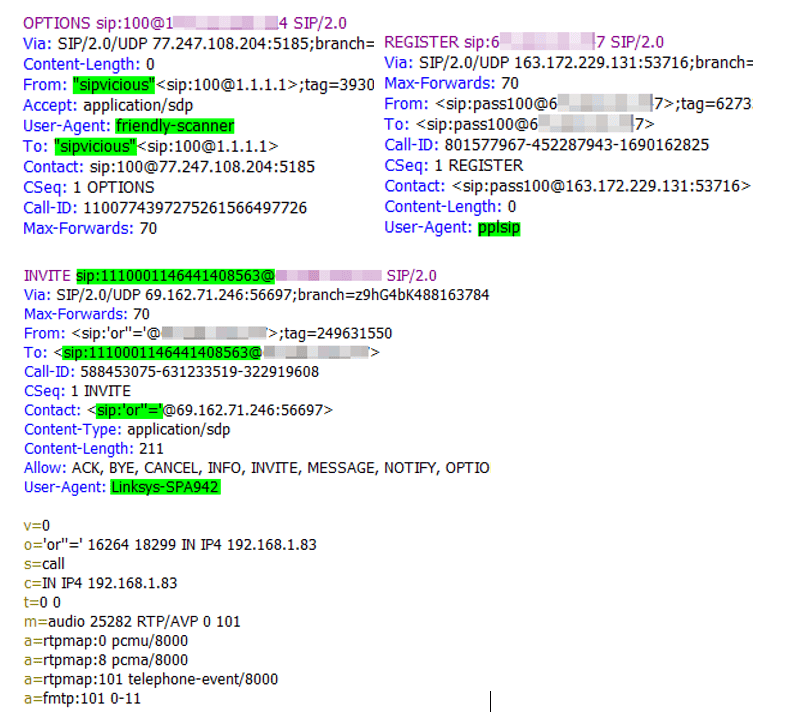
The SBC was being actively scanned in attempt to hijack calling capabilities. This was the perfect opportunity to configure and test my security rules in the AudioCodes SBC!
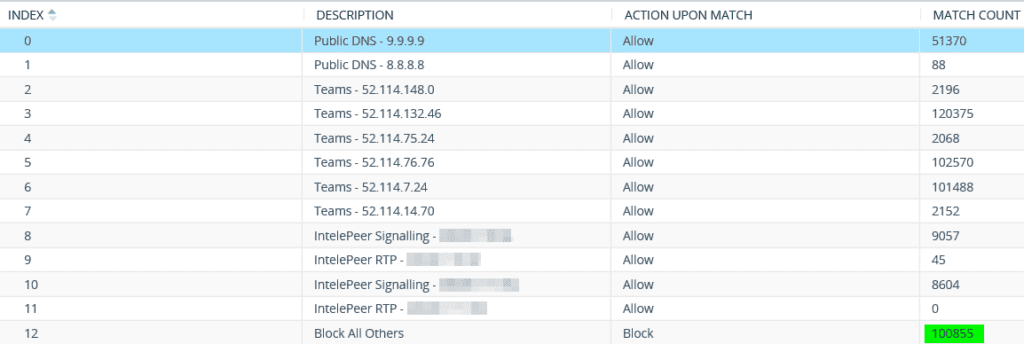
For this particular deployment, the SBC had a single public interface and a single LAN interface. Microsoft Teams and IntelePeer were sharing the same public interface (and IP address). Microsoft Teams was configured to utilize TLS transport and IntelePeer was configured to use UDP transport; thus, one of the reasons to configure the AudioCodes firewall. In this case, the LAN interface was not added to the firewall list. In the example below, the last rule blocks everything that isn’t allowed in the list above that rule. The line items above the last rule were added specifically to allow external DNS lookups, Teams, and IntelePeer Signaling and RTP traffic. Once these rules were configured and tied to the public interface, I no longer saw any malicious SIP attempts. However, you can see the 10,0855 attempts being blocked/dropped as well.
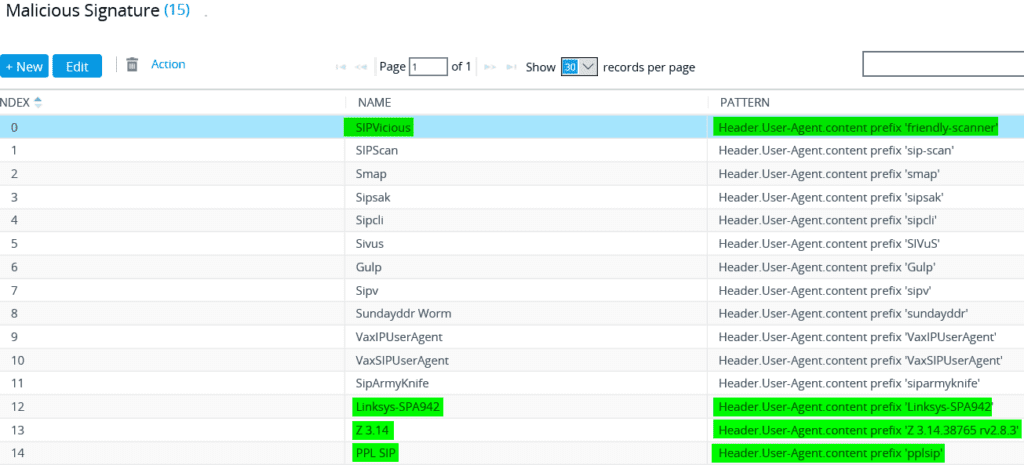
Another method you can use to guard against malicious SIP attacks is to configure and utilize the Malicious Signatures feature in the AudioCodes SBC. By default, AudioCodes has prepared a list of known patterns based on malicious user agents. In the screenshot below, you can see the additions made based on the attacks we were receiving:
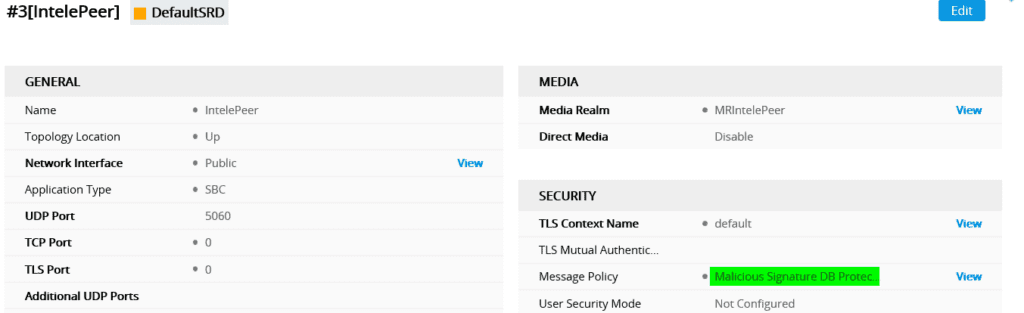
In order to utilize the malicious signatures list, you have to configure a “message policy” and enable the malicious signatures database. You can configure this policy to drop or reject the malicious SIP message, backlist/whitelist, as well as define message limits.
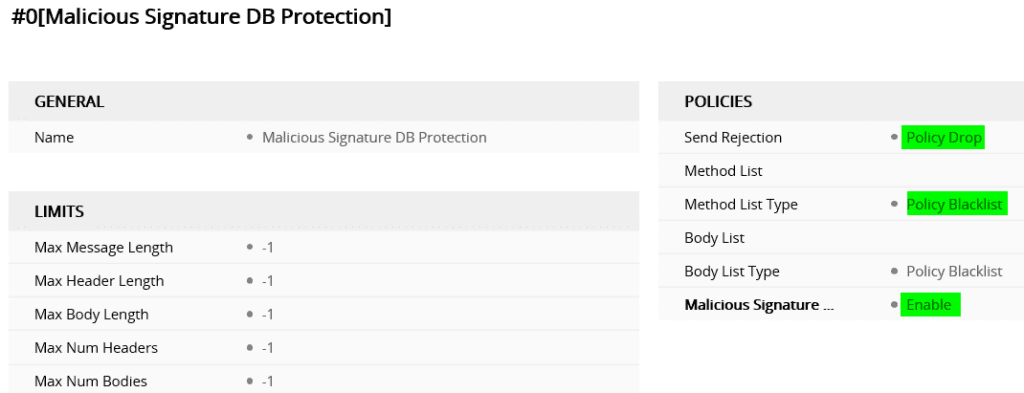
Once the policy has been created you can assign it to the appropriate SIP interface, in this case, the IntelePeer SIP interface. Note that malicious signatures do not apply to calls from IP groups where classification is by proxy set.
Contact Us!
For additional information or assistance securing and configuring your SBC Teams Direct Routing, contact our team of experts today! Our team has years of experience and knows all of the “minefields” to prevent missteps.

Cloud Solutions Architect - eGroup | Enabling Technologies
Last updated on July 31st, 2023 at 01:02 pm