Seven Steps for Successful
Incident Response Tabletop Exercises

A tabletop exercise simulates real world scenarios, stress testing the readiness of the participants to execute their procedures to respond to cyber incidents. eGroup | Enabling Technologies has been conducting Incident Response Tabletop Exercises for over two years now. The interest level has spiked of late, likely because AIG and other cyber insurance providers are now asking about tabletop exercises in their latest renewal paperwork.
This blog outlines some (good) practices for organizations to make the most out of conducting tabletop exercises.
1.Don’t test a process that doesn’t exist
Tabletop exercises are the most successful when they stress test an existing, documented process and procedure. Some organizations lack the high-level policies and RACI (Responsible/Accountable/Consulted/Informed) matrices defining the basics. If the process only exists in someone’s head, it’s too early to test.
2. Pick a methodology
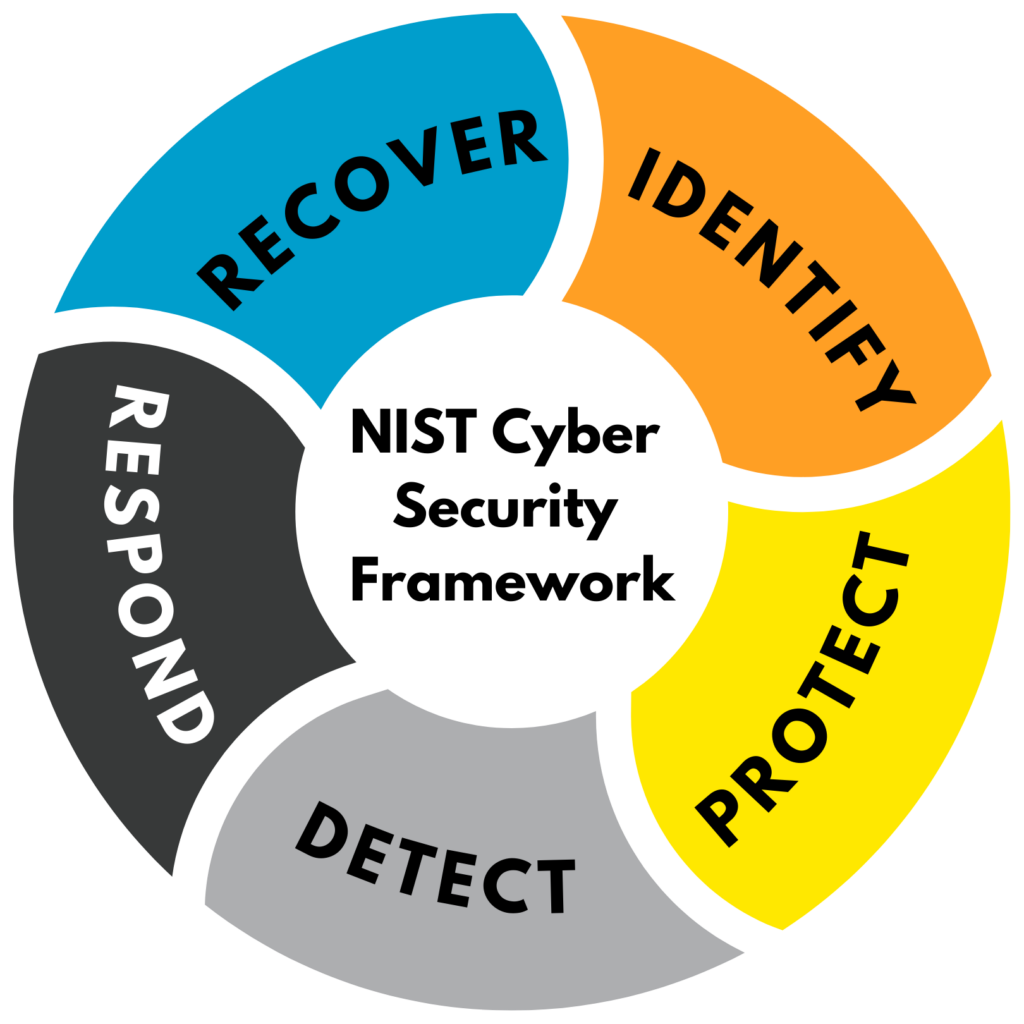
Our team uses a framework based on the National Institute of Standards Technology methodology, NIST 800-84. More mature organizations that need to keep their practitioners interested may prefer aspects of the Backdoors and Breaches game, which can be played online or with playing cards. In either case, the focus should be on the detect, respond, and recover phases of the NIST cyber security framework (below).
3. Include the right people
Incident response plans require a team that extends beyond IT, including communications personnel, legal advisors, and the CFO (if not the CEO). If these players aren’t already aware and trained in their role, they should at least be a part of the kickoff and closeout of the tabletop exercise. That way, the IT team can get the buy-in and external support needed to allow them to focus on the incident itself.
4. Assess the right incidents
Each organization has different priorities. Rather than just work through a standard list of scenarios, start with those most pertinent to the organization’s risk model and business operations. For most, this means addressing their crown jewels, which often are ERP or manufacturing/inventory systems. Put a significant amount of effort into ensuring the processes to respond and recover these critical systems before spending time on less pertinent scenarios.
5. Focus on the basics
When conducting the live exercises, ask about the “Who/what/when/how” for each scenario. For instance, when discussing a scenario where a VIP loses their smartphone with corporate content on it, we ask how IT would know if the device was lost or stolen, who the person would alert about the lost device, and then who and how someone would lock accounts, what tool is used to delete organizational info from the device, who would issue temporary access on another device, etc.
Important aspects to look for here include whether the process is documented, who has (pre-approved) authority to take immediate action to respond, and who will take responsibility if the remediation steps impact business in a negative way.
6. Inject challenges
For a process that is well documented, people already know who will do what and when, and what tools to use to recover. If the team is at this stage, throw in some curveballs. For instance, in the middle of recovering from a ransomware incident, the adversary posts your customer data to Pastebin, making the media aware of the situation. Who handles that flak while the response team continues to isolate and recover?
7. Keep it fresh
After working through a semi-formal exercise a time or two, an organization can get its practitioners thinking about incident response in more day-to-day situations. Why not bring it up over lunch? “What would we do if Microsoft 365 goes down for two days” would start a vibrant mealtime dialog!
This is important to do when a new vector or incident becomes public. For instance, even if an organization didn’t use Solarwinds, they should have talked through and documented how they’d respond to a similar situation (i.e. Kaseya).
Summary
Tabletop exercises are an integral part of a maturing organization’s security lifecycle. When conducted at the right time with the right people, they can be extremely helpful to identify critical opportunities for improvement.
Said one of our customers, “Working with eGroup | Enabling on developing tabletop exercises for our top threats was an integral part of upgrading our information security risk management plan. It was a great experience and helped us identify and fill critical gaps in our own internal procedures. These documented exercises are serving as a training tool for all IT staff as well.”
Interested in learning more? Contact us at info@eGroup-us.com to set up an Incident Response Plan Tabletop Exercise, a Cybersecurity Health Check, or a Microsoft Security Assessment!

CTO & VP of Strategy - eGroup | Enabling Technologies
Last updated on December 22nd, 2023 at 11:11 am